Similar presentations:
Методы реверс-инжиниринга обфусцированного и виртуализированного приложения
1. Методы РЕВЕРС-ИНЖИНИРИНГА ОБФУСЦИРОВАННОГО и ВИРТУАЛИЗИРОВАННОГО ПРИЛОЖЕНИЯ
МЕТОДЫ РЕВЕРС-ИНЖИНИРИНГАОБФУСЦИРОВАННОГО И
ВИРТУАЛИЗИРОВАННОГО ПРИЛОЖЕНИЯ
Алюшин Виктор
2. СПОСОБЫ Защиты приложений
СПОСОБЫ ЗАЩИТЫПРИЛОЖЕНИЙ
• Упаковка / шифрование всего файла
• Обфускация отдельных строк / машинного кода
• Виртуализация кода
• Обнаружение отладчиков/эмуляторов/песочниц/виртуалок
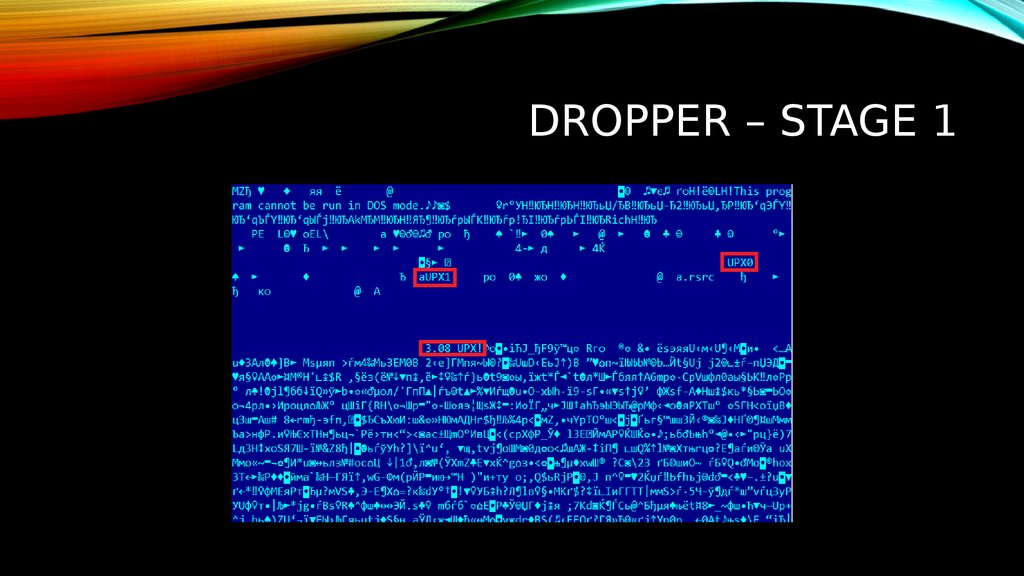
3. DroPPER – STAGE 1
DROPPER – STAGE 14. DroPPER – STAGE 1
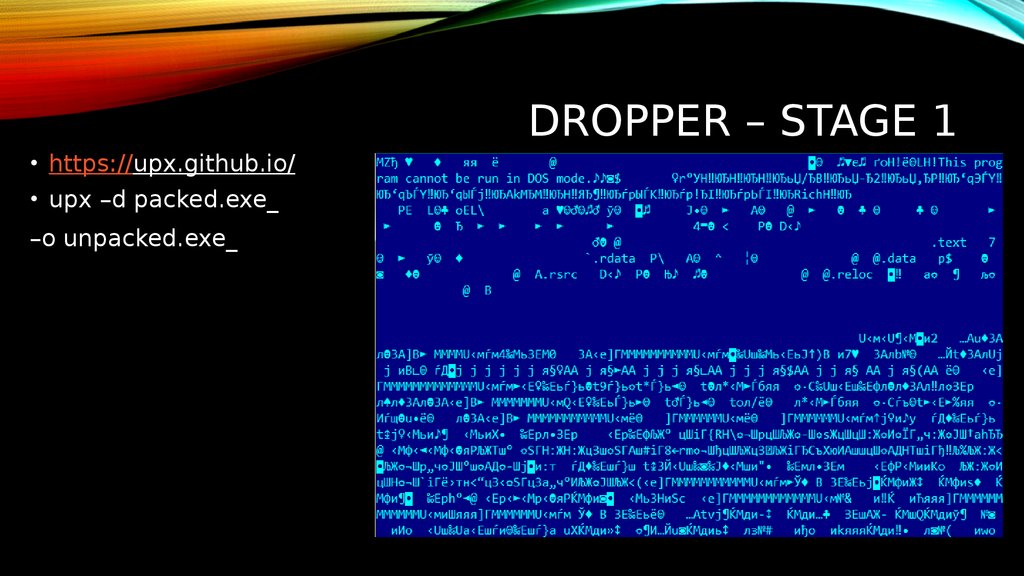
DROPPER – STAGE 1• https://upx.github.io/
• upx –d packed.exe_
–o unpacked.exe_
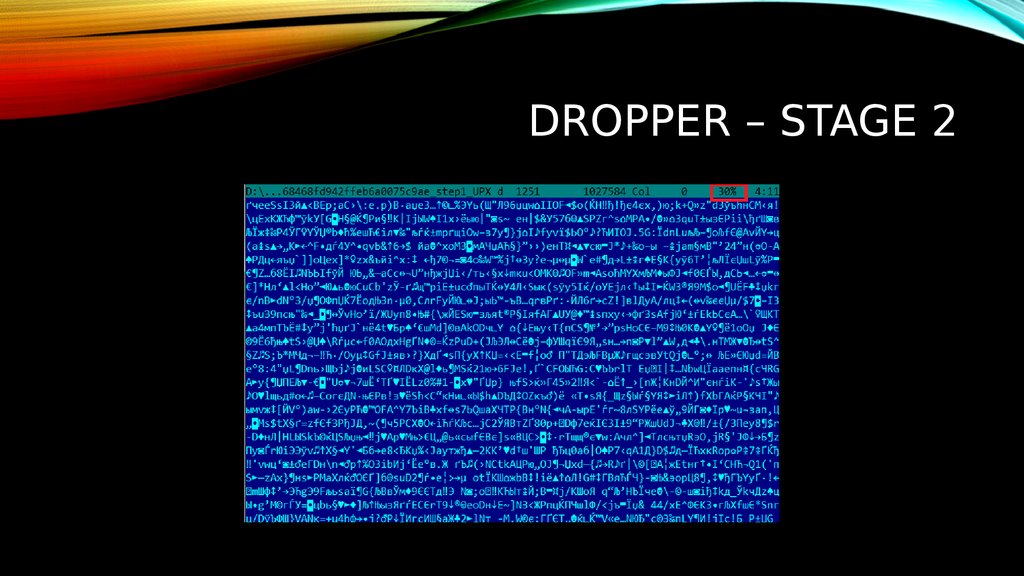
5. Dropper – stage 2
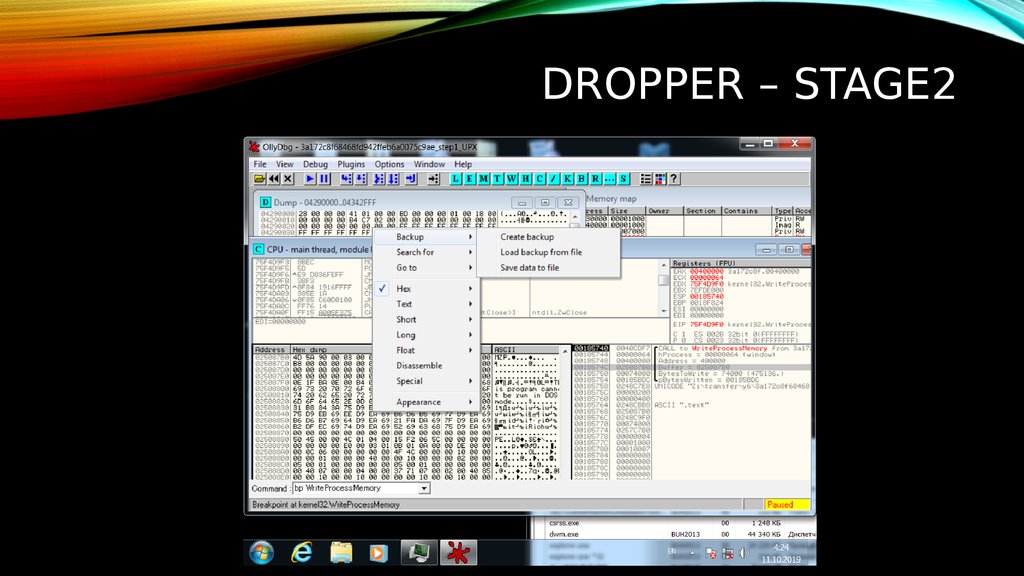
DROPPER – STAGE 26. DROPPER – STAGE2
• OllyDbg + Cmdbar / x64dbg / Immunity Debugger• bp VirtualAlloc
• bp VirtualProtect
• bp VirtualFree
• bp WriteProcessMemory
7. DROPPER – STAGE2
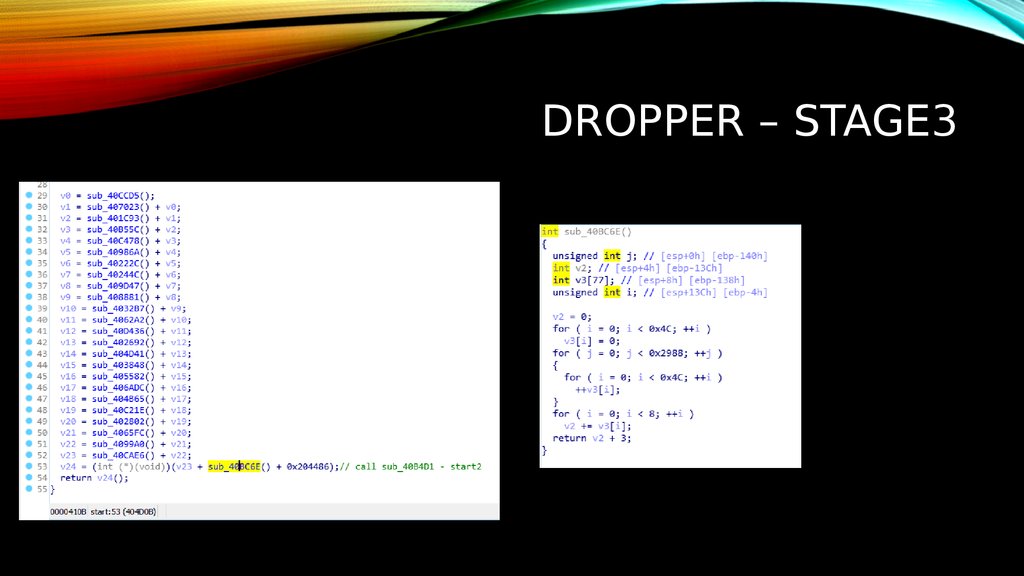
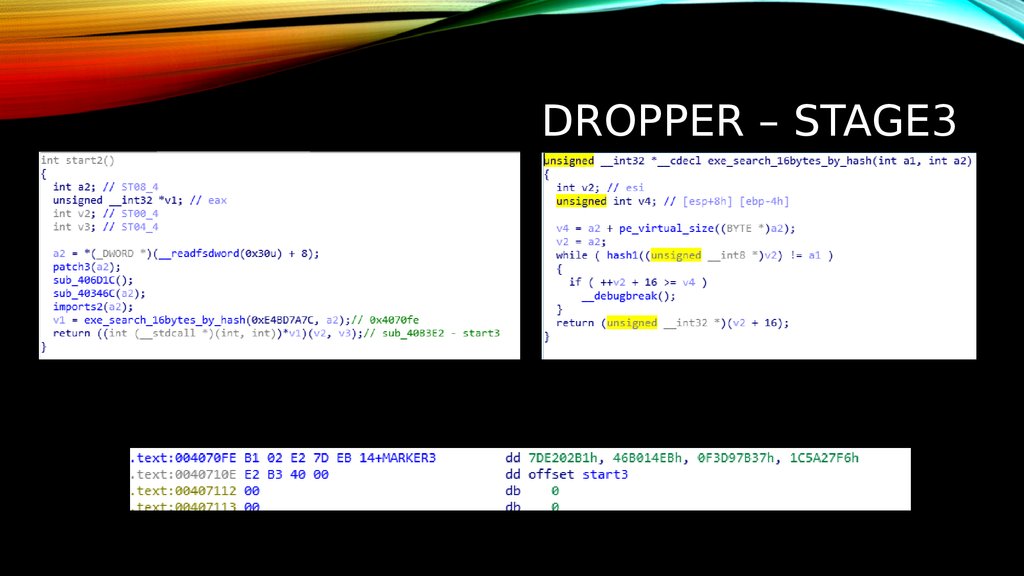
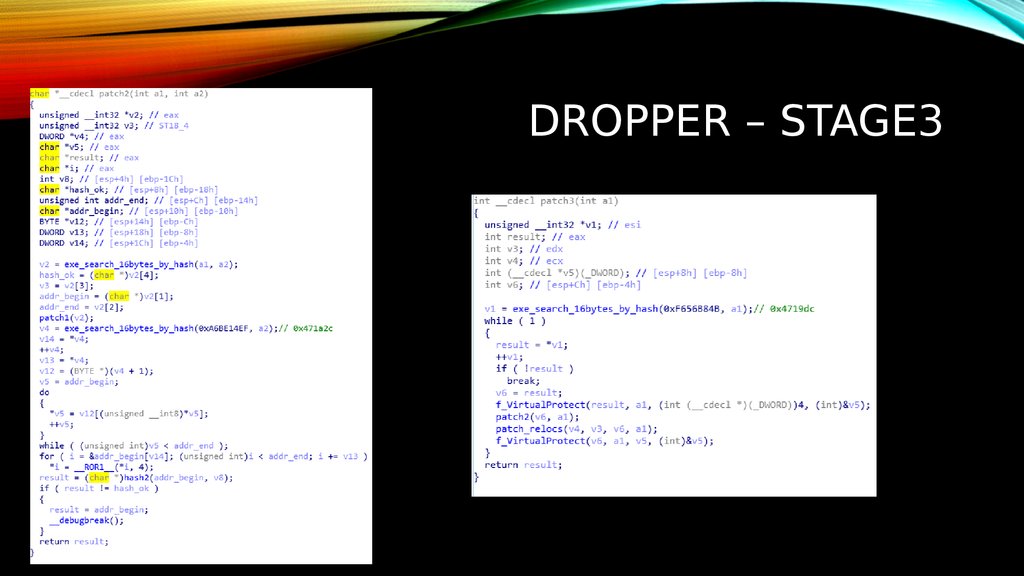
8. DROPPER – STAGE3
9. DROPPER – STAGE3
10. DROPPER – STAGE3
11. dropper – stage3
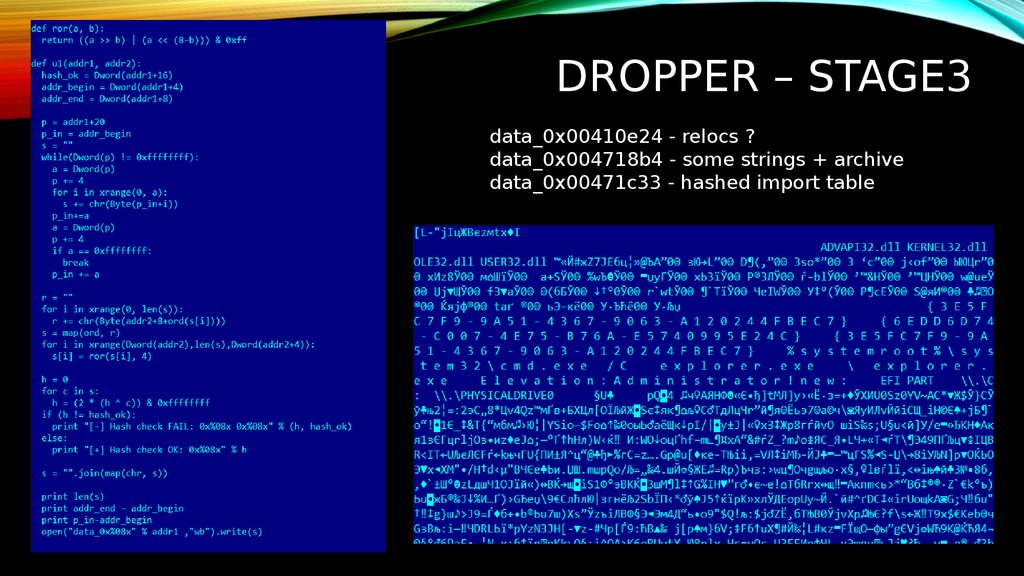
DROPPER – STAGE312. Dropper – stage3
DROPPER – STAGE3data_0x00410e24 - relocs ?
data_0x004718b4 - some strings + archive
data_0x00471c33 - hashed import table
13. DROPPER – STAGE3 - ARCHIVE
14. UNPACKING ARCHIVE
• 6 files !!!• BIOS IMAGE
• 16-bit shellcode (3x)
• Driver x32
• Driver x64
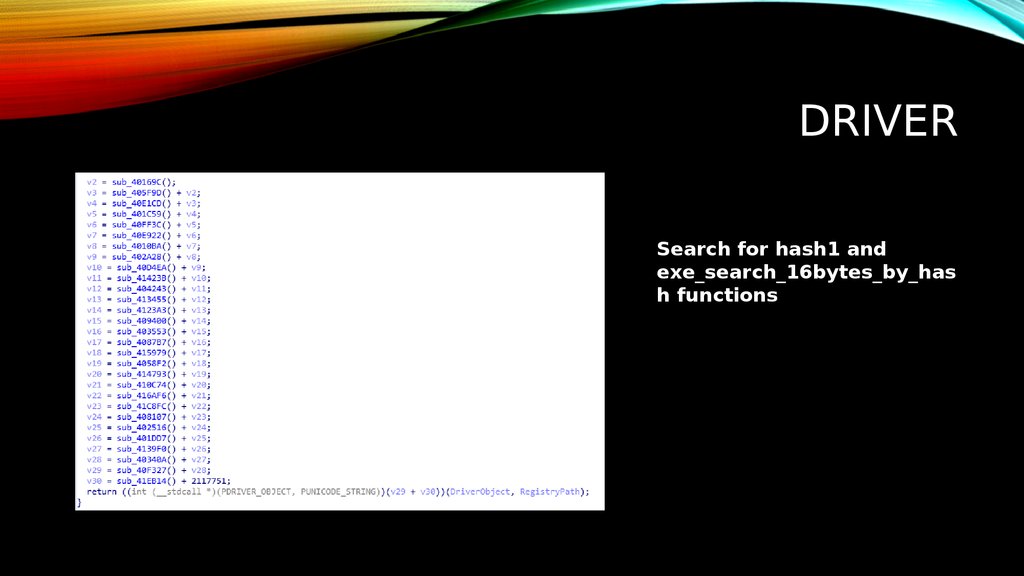
15. DrivER
DRIVERSearch for hash1 and
exe_search_16bytes_by_has
h functions
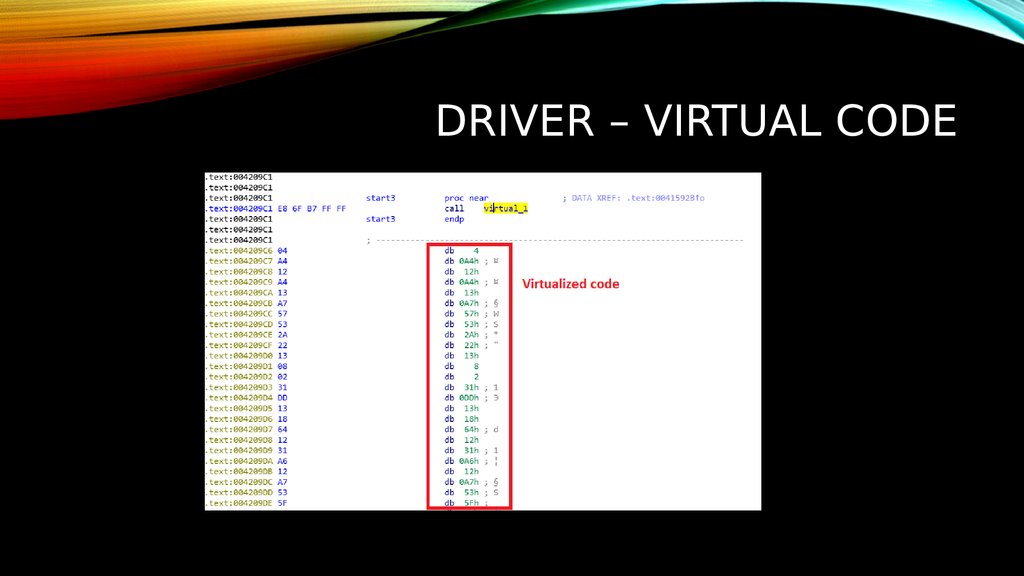
16. DRIVER – VIRTUAL CODE
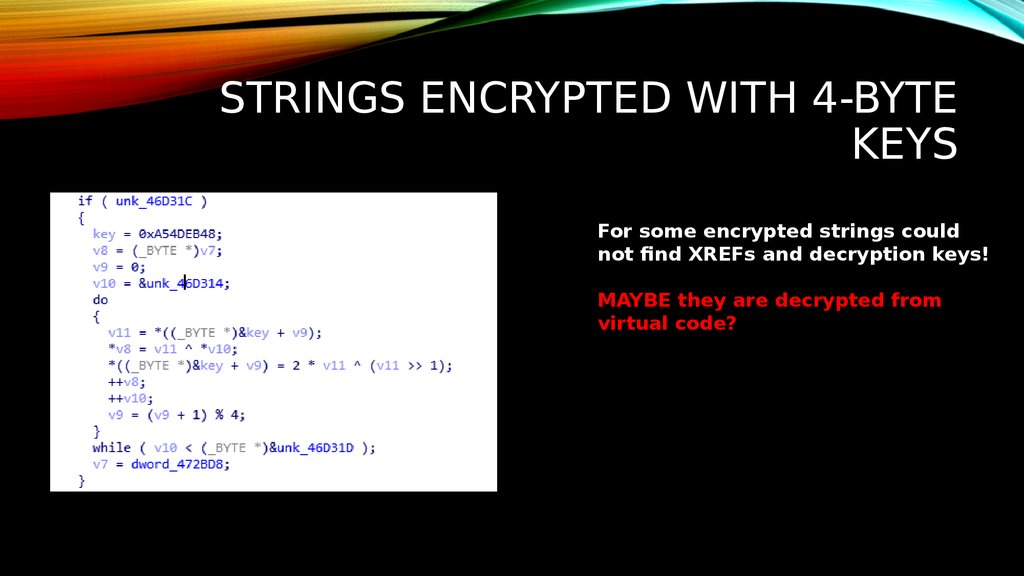
17. STRINGS ENCRYPTED WITH 4-BYTE keys
STRINGS ENCRYPTED WITH 4-BYTEKEYS
For some encrypted strings could
not find XREFs and decryption keys!
MAYBE they are decrypted from
virtual code?
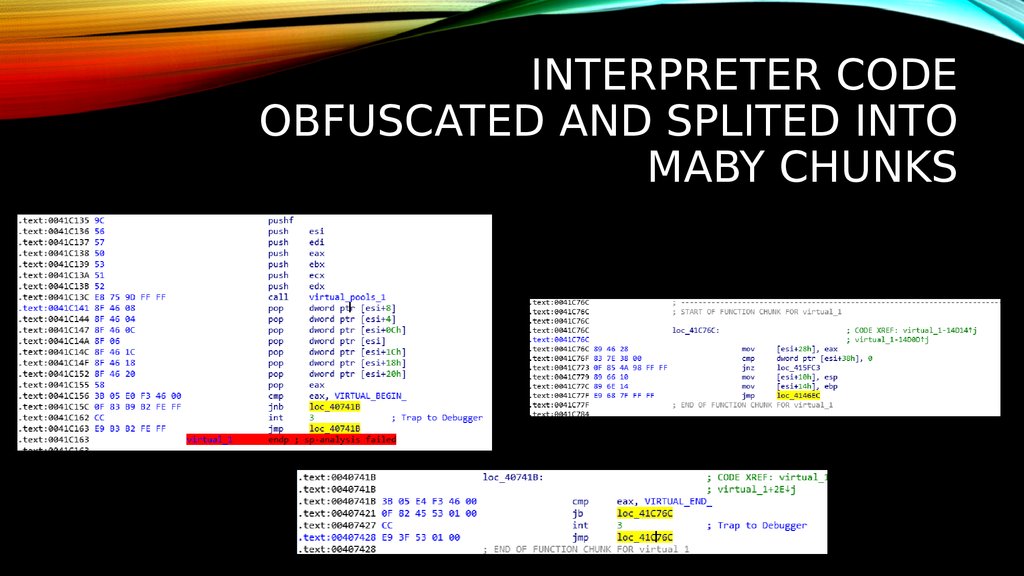
18. INTERPRETER CODE OBFUSCATED aND SPLITED INTO MABY CHUNKS
INTERPRETER CODEOBFUSCATED AND SPLITED INTO
MABY CHUNKS
19. VIRTUAL INSTRUCTIONS
4-byte arguments xored with 0x69B00B7A2-byte arguments xored with 0x13F1
1-byte arguments xored with 0x57
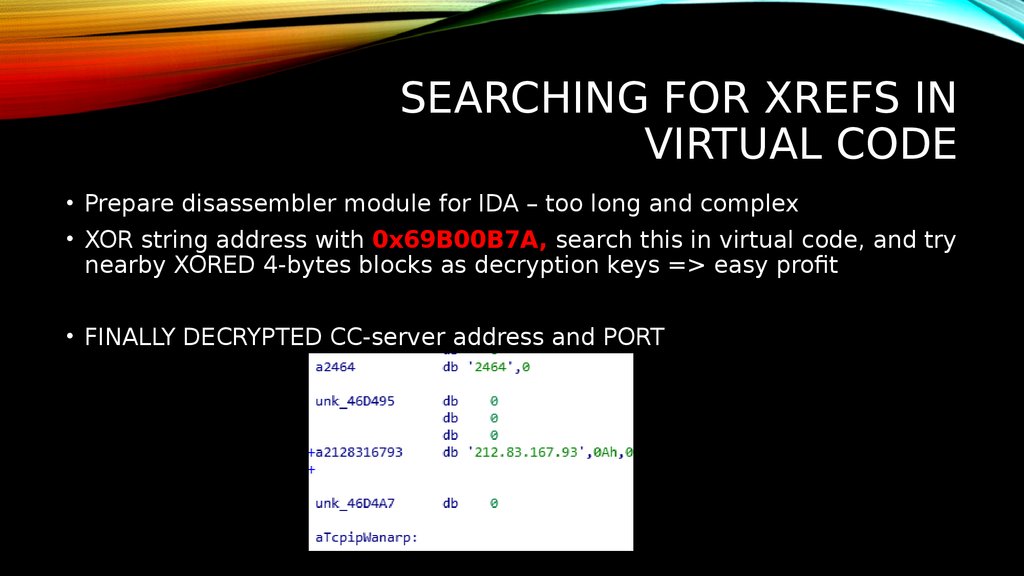
20. SEARCHING FOR XREFS IN VIRTUAL CODE
• Prepare disassembler module for IDA – too long and complex• XOR string address with 0x69B00B7A, search this in virtual code, and try
nearby XORED 4-bytes blocks as decryption keys => easy profit
• FINALLY DECRYPTED CC-server address and PORT
21. DGA algorithm
DGA ALGORITHM• SEEMS DGA ALROTITHM ALSO EXISTS
• NO XREFS FROM NATIVE CODE TO DGA strings
• TODO – time to make IDA PRO processor module
22. Thanks!
THANKS!QUESTIONS ?









 programming
programming








