Similar presentations:
Java Core. Introduction
1.
Java CoreINTRODUCTION
MODULE 02
January, 2019
Andrii Pavelchak
CONFIDENTIAL
1
2.
Agenda1. History
2. Feature of Java
3. JAVA Platform
4. Primitive vs Reference
5. Garbage Collection
6. Steps to create a Java application
7. Code convention
8. Javadoc
CONFIDENTIAL
2
3.
HistoryJames Gosling (born May 19, 1955) is a Canadian
computer scientist, best known as the founder and
lead designer behind the Java programming
language.
James Gosling, Mike Sheridan, and Patrick Naughton initiated the Java
language project in June 1991. The small team of sun engineers called Green
Team.
Originally designed for small, embedded systems in electronic appliances like
set-top boxes.
Firstly, it was called "Greentalk" by James Gosling, and file extension was .gt.
After that, it was called Oak and was developed as a part of the Green project.
In 1995, Oak was renamed as "Java" because it was already a trademark by
Oak Technologies. Java is an island of Indonesia where first coffee was
produced (called java coffee).
CONFIDENTIAL
3
4.
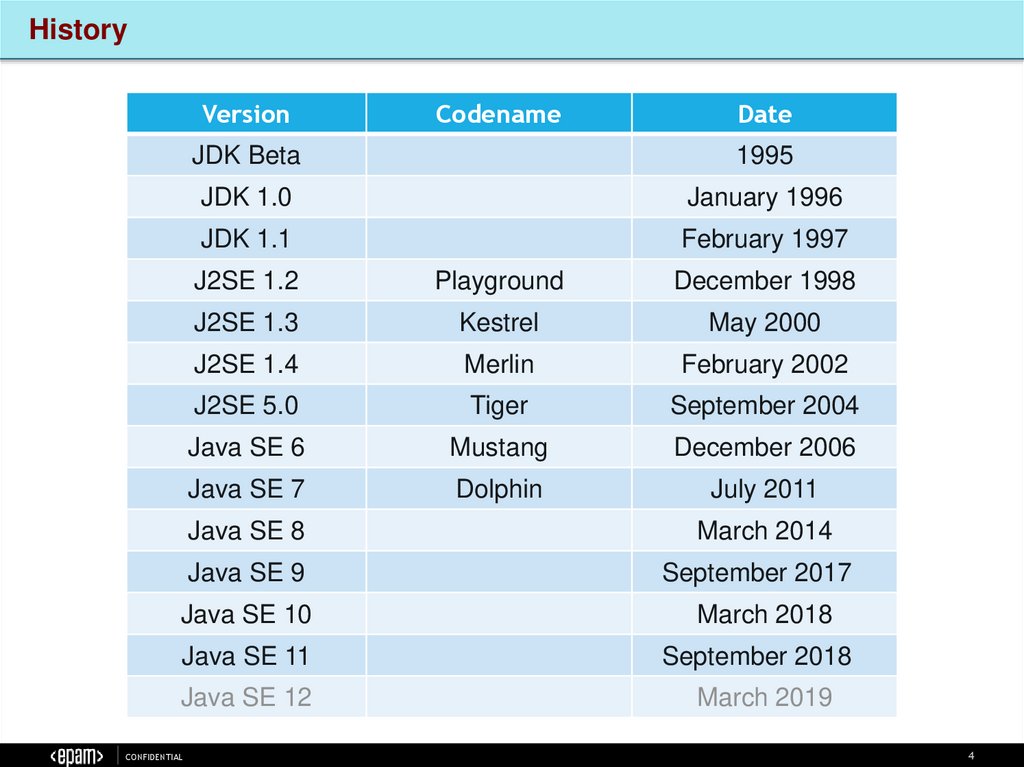
HistoryVersion
Date
JDK Beta
1995
JDK 1.0
January 1996
JDK 1.1
February 1997
J2SE 1.2
Playground
December 1998
J2SE 1.3
Kestrel
May 2000
J2SE 1.4
Merlin
February 2002
J2SE 5.0
Tiger
September 2004
Java SE 6
Mustang
December 2006
Java SE 7
Dolphin
July 2011
Java SE 8
Java SE 9
Java SE 10
Java SE 11
Java SE 12
CONFIDENTIAL
Codename
March 2014
September 2017
March 2018
September 2018
March 2019
4
5.
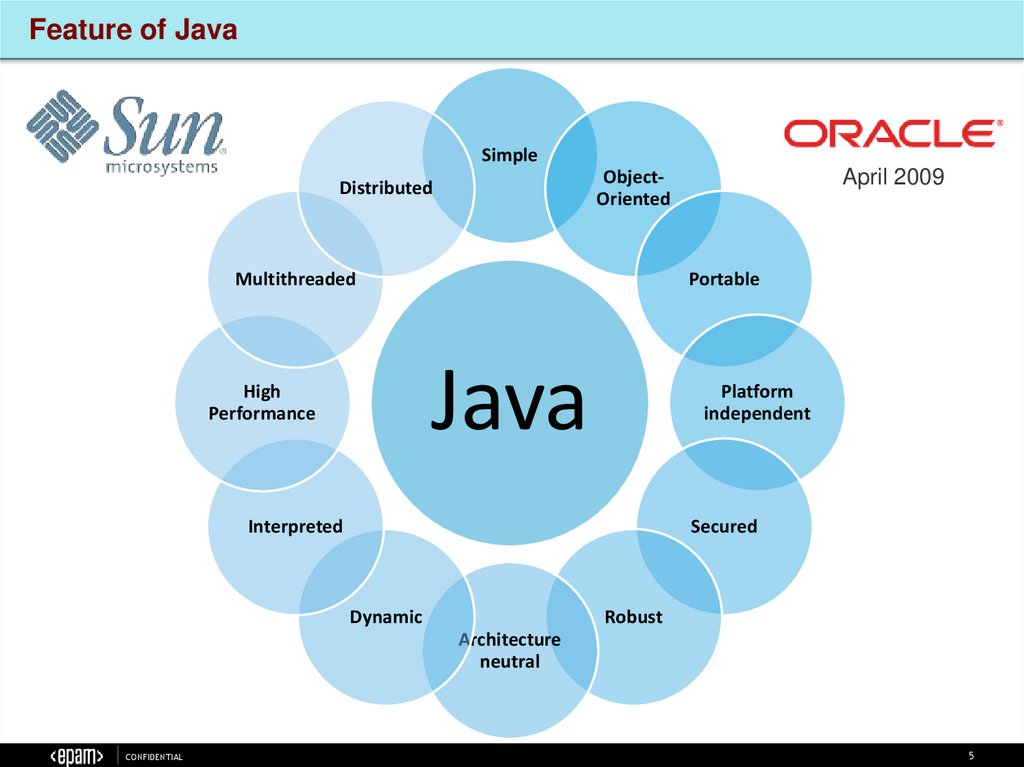
Feature of JavaSimple
Multithreaded
Portable
Java
High
Performance
April 2009
ObjectOriented
Distributed
Platform
independent
Interpreted
Secured
Dynamic
Robust
Architecture
neutral
CONFIDENTIAL
5
6.
Feature of JavaObject Oriented − In Java, everything is an Object. Java can be easily
extended since it is based on the Object model.
Platform Independent − Unlike many other programming languages including
C and C++, when Java is compiled, it is not compiled into platform specific
machine, rather into platform independent byte code. This byte code is
distributed over the web and interpreted by the Virtual Machine (JVM) on
whichever platform it is being run on.
Class file
CONFIDENTIAL
Windows
JVM
Windows
Linux
JVM
Linux
Mac/OS
JVM
Mac/OS
6
7.
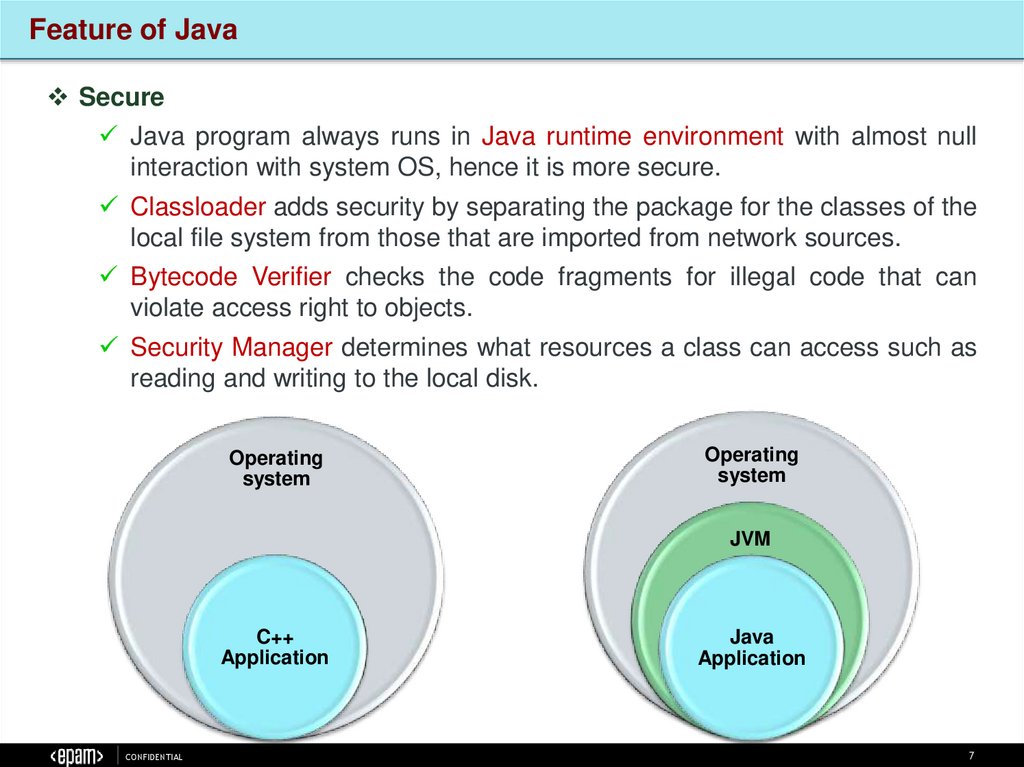
Feature of JavaSecure
Java program always runs in Java runtime environment with almost null
interaction with system OS, hence it is more secure.
Classloader adds security by separating the package for the classes of the
local file system from those that are imported from network sources.
Bytecode Verifier checks the code fragments for illegal code that can
violate access right to objects.
Security Manager determines what resources a class can access such as
reading and writing to the local disk.
Operating
system
Operating
system
JVM
C++
Application
CONFIDENTIAL
Java
Application
7
8.
Feature of JavaHigh-performance
Java uses Just-In-Time compilers.
Garbage collector, collect the unused memory space and improve the
performance of the application.
It has no pointers so that using this language we can develop an
application very easily.
It support multithreading, because of this time consuming process can be
reduced to executing the program.
Dynamic − Java is considered to be more dynamic than C or C++ since it is
designed to adapt to an evolving environment. Java programs can carry
extensive amount of run-time information that can be used to verify and
resolve accesses to objects on run-time.
Distributed − Java is designed for the distributed environment of the internet.
Robust − One of the major advantages of Java over C++ is that it prevents
memory leaks. Java manages memory on its own and does garbage collection
automatically. Bad memory management in C++ is a big source of errors in
programs.
CONFIDENTIAL
8
9.
Feature of JavaJAVA
C/C++
CONFIDENTIAL
familiar syntax
Smalltalk
Virtual machine,
JIT compilation,
Bytecode,
Garbage collection
9
10.
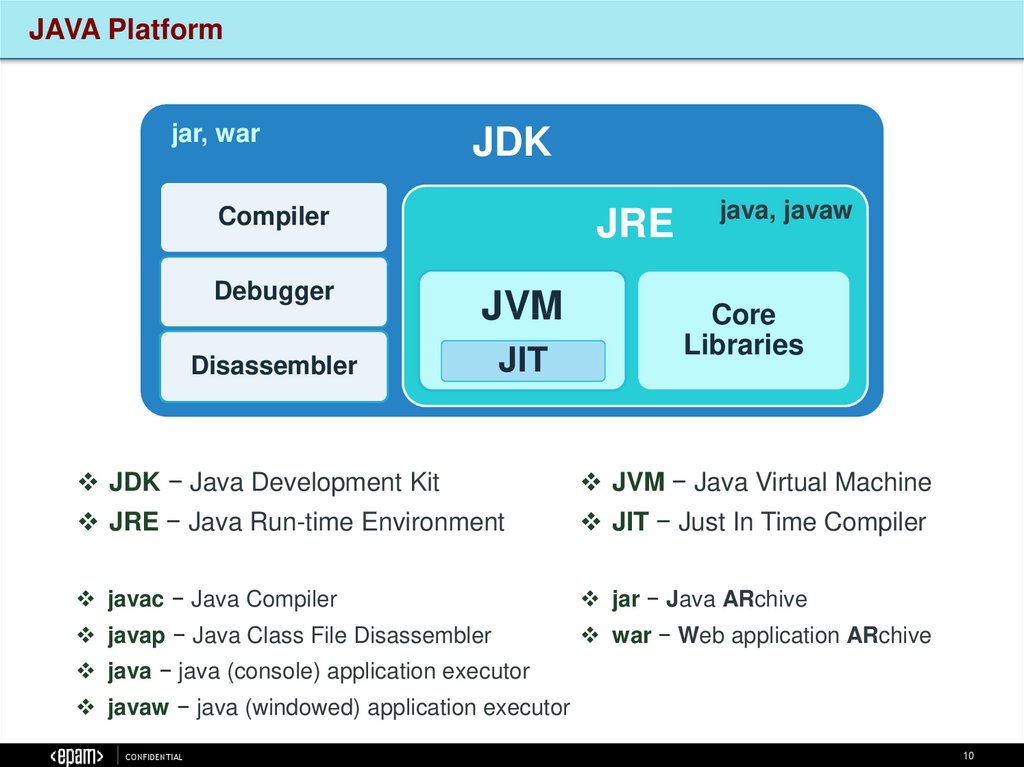
JAVA Platformjar, war
JDK
Compiler
JRE
Debugger
JVM
Disassembler
JIT
java, javaw
Core
Libraries
JDK − Java Development Kit
JVM − Java Virtual Machine
JRE − Java Run-time Environment
JIT − Just In Time Compiler
javac − Java Compiler
jar − Java ARchive
javap − Java Class File Disassembler
war − Web application ARchive
java − java (console) application executor
javaw − java (windowed) application executor
CONFIDENTIAL
10
11.
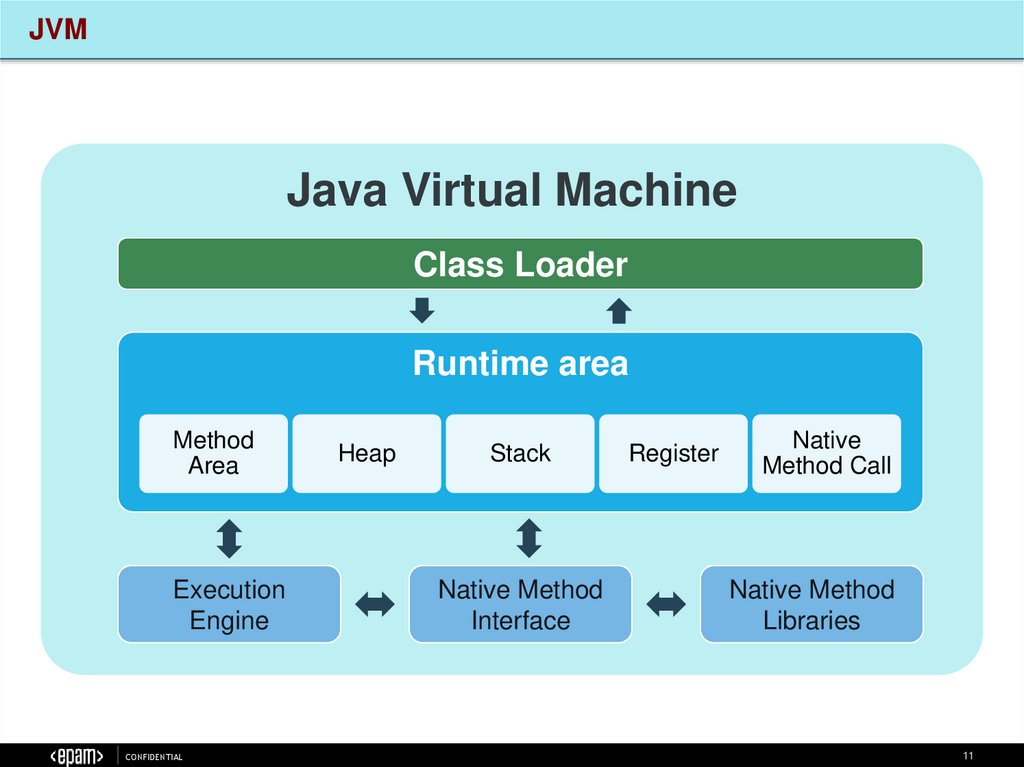
JVMJava Virtual Machine
Class Loader
Runtime area
Method
Area
Execution
Engine
CONFIDENTIAL
Heap
Stack
Native Method
Interface
Register
Native
Method Call
Native Method
Libraries
11
12.
JVMJVM Classloader
Hierarchy
Bootatrap
Classloader
<JAVA_HOME>/jre/lib
Extention
Classloader
<JAVA_HOME>/jre/lib/ext
System
Classloader
CLASSPATH
directory
directory
directory
User-defined
Classloader
User-defined
Classloader
CONFIDENTIAL
User-defined
Classloader
12
13.
Stack and HeapStack − This memory is used for execution of a thread. Stack memory
only contains local primitive variables and reference variables. Stack
memory is very fast but less in size compare to heap.
Heap − Whenever we create any object, it’s always created in the Heap
and reference variable of object in the stack. Any object created in the
heap has global access and can be referenced from anywhere of the
application.
Instance variables and objects live on the heap.
Local variables live on the stack.
CONFIDENTIAL
13
14.
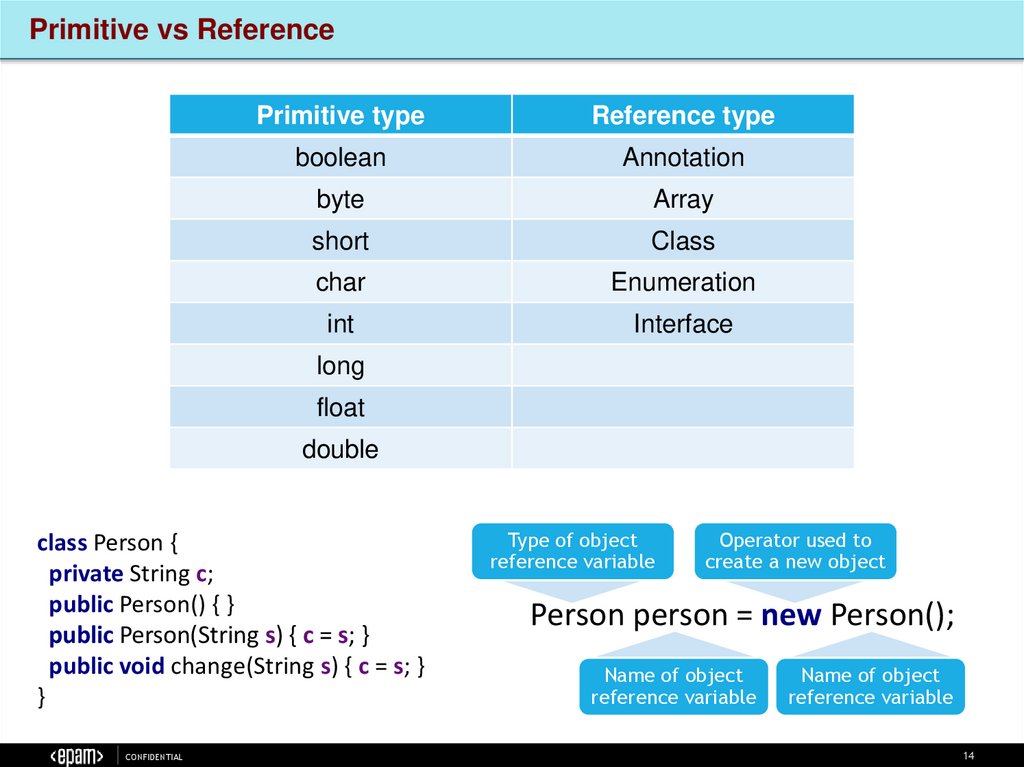
Primitive vs ReferencePrimitive type
Reference type
boolean
Annotation
byte
Array
short
Class
char
Enumeration
int
Interface
long
float
double
class Person {
private String c;
public Person() { }
public Person(String s) { c = s; }
public void change(String s) { c = s; }
}
CONFIDENTIAL
Type of object
reference variable
Operator used to
create a new object
Person person = new Person();
Name of object
reference variable
Name of object
reference variable
14
15.
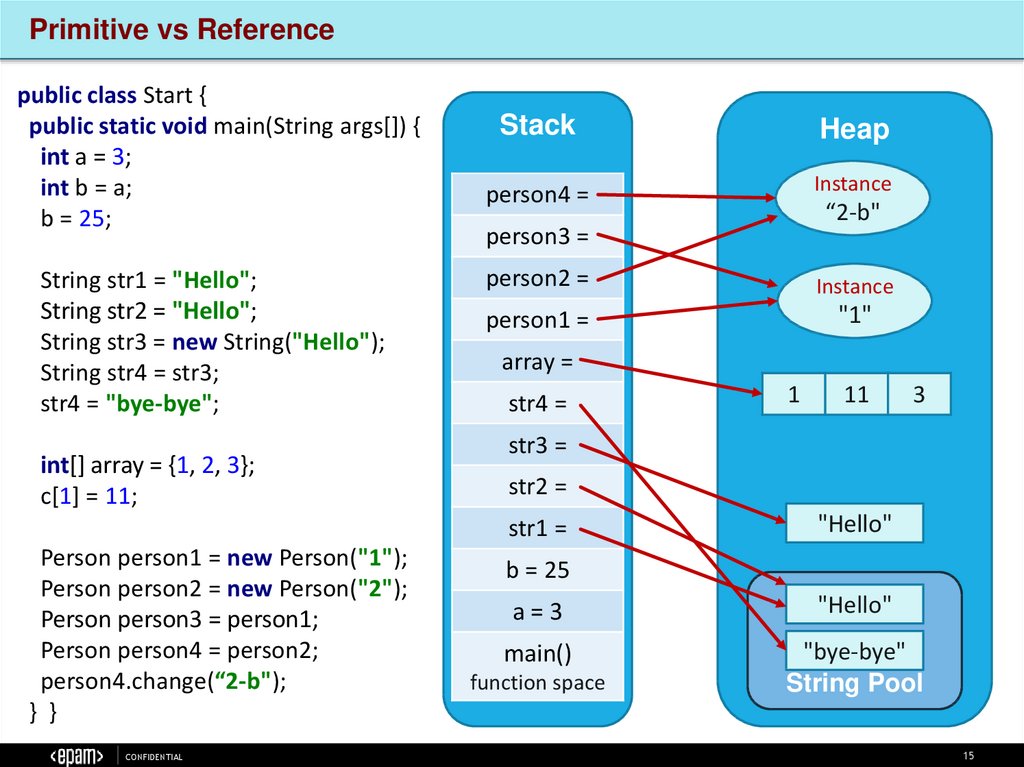
Primitive vs Referencepublic class Start {
public static void main(String args[]) {
int a = 3;
int b = a;
b = 25;
String str1 = "Hello";
String str2 = "Hello";
String str3 = new String("Hello");
String str4 = str3;
str4 = "bye-bye";
int[] array = {1, 2, 3};
c[1] = 11;
Stack
Heap
person4 =
Instance
person3 =
person2 =
Instance
person1 =
"1"
array =
str4 =
CONFIDENTIAL
1
11
3
str3 =
str2 =
str1 =
Person person1 = new Person("1");
Person person2 = new Person("2");
Person person3 = person1;
Person person4 = person2;
person4.change(“2-b");
} }
“2-b"
"Hello"
b = 25
a=3
"Hello"
main()
"bye-bye"
String Pool
function space
15
16.
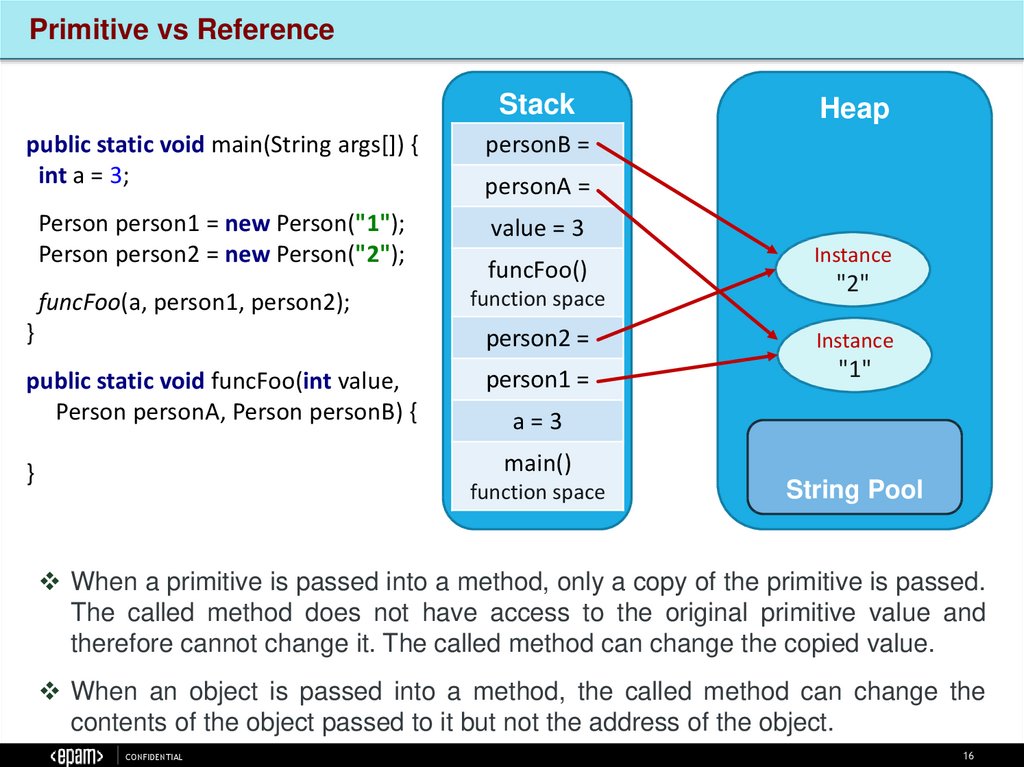
Primitive vs ReferenceStack
public static void main(String args[]) {
int a = 3;
Person person1 = new Person("1");
Person person2 = new Person("2");
funcFoo(a, person1, person2);
Heap
personB =
personA =
value = 3
funcFoo()
function space
Instance
"2"
}
person2 =
Instance
public static void funcFoo(int value,
Person personA, Person personB) {
person1 =
"1"
a=3
main()
}
function space
String Pool
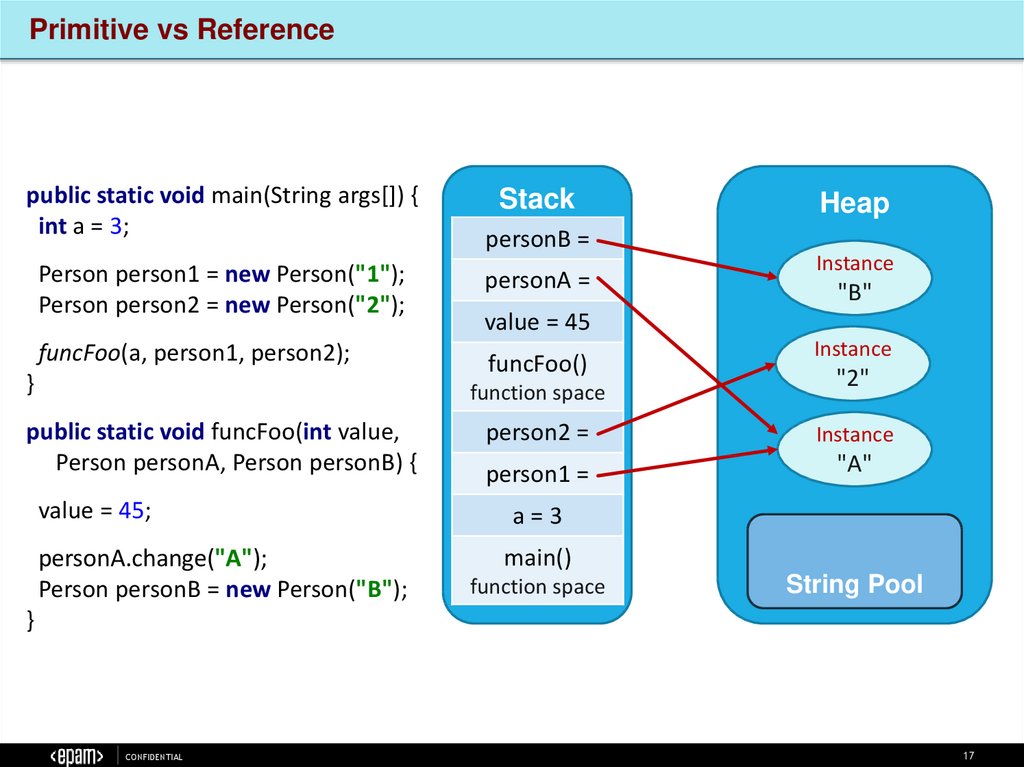
When a primitive is passed into a method, only a copy of the primitive is passed.
The called method does not have access to the original primitive value and
therefore cannot change it. The called method can change the copied value.
When an object is passed into a method, the called method can change the
contents of the object passed to it but not the address of the object.
CONFIDENTIAL
16
17.
Primitive vs Referencepublic static void main(String args[]) {
int a = 3;
Person person1 = new Person("1");
Person person2 = new Person("2");
funcFoo(a, person1, person2);
}
Stack
personB =
personA =
value = 45;
personA.change("A");
Person personB = new Person("B");
Instance
"B"
value = 45
funcFoo()
function space
public static void funcFoo(int value,
Person personA, Person personB) {
Heap
Instance
"2"
person2 =
Instance
person1 =
"A"
a=3
main()
function space
String Pool
}
CONFIDENTIAL
17
18.
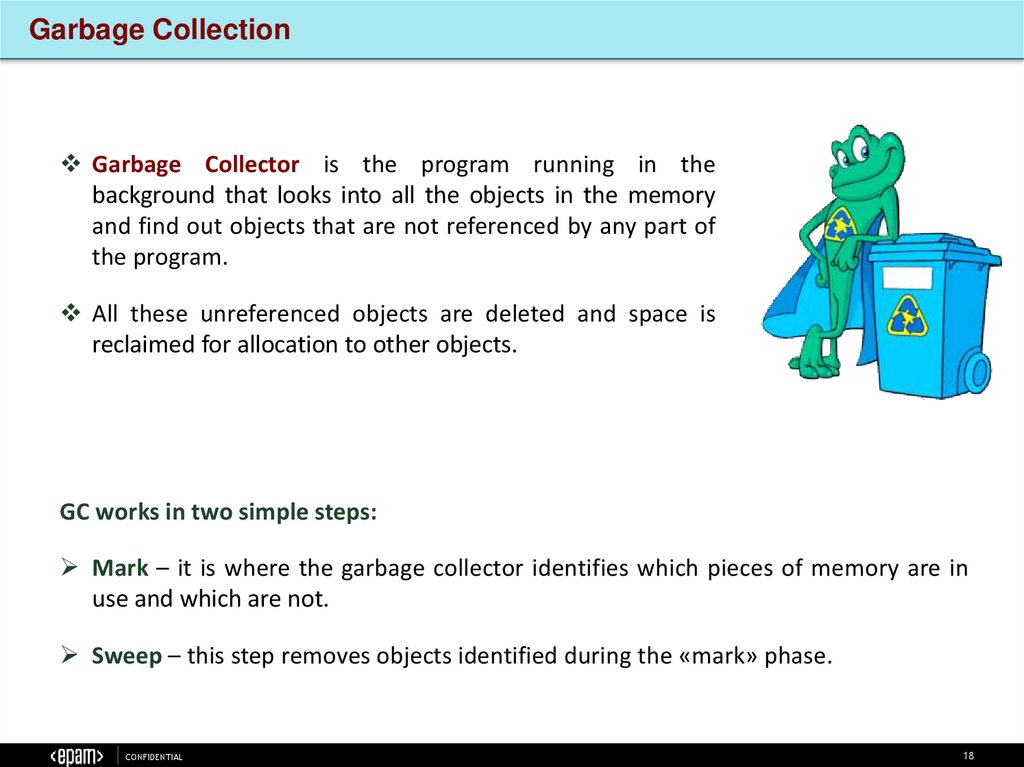
Garbage CollectionGarbage Collector is the program running in the
background that looks into all the objects in the memory
and find out objects that are not referenced by any part of
the program.
All these unreferenced objects are deleted and space is
reclaimed for allocation to other objects.
GC works in two simple steps:
Mark – it is where the garbage collector identifies which pieces of memory are in
use and which are not.
Sweep – this step removes objects identified during the «mark» phase.
CONFIDENTIAL
18
19.
Garbage CollectionWays to make an object eligible for GC:
Nullifying the reference variable
Re-assigning the reference variable
Object created inside method
Island of Isolation
CONFIDENTIAL
19
20.
Garbage CollectionGarbage Collector Strategies:
Serial Garbage Collector- S GC
Parallel Garbage Collector- P GC (default in Java 7, 8)
CMS Garbage Collector- CMS GC
G1 Garbage Collector- G1 GC (default in Java 9, 10)
The Z Garbage Collector- ZGC (default in Java 11)
CONFIDENTIAL
20
21.
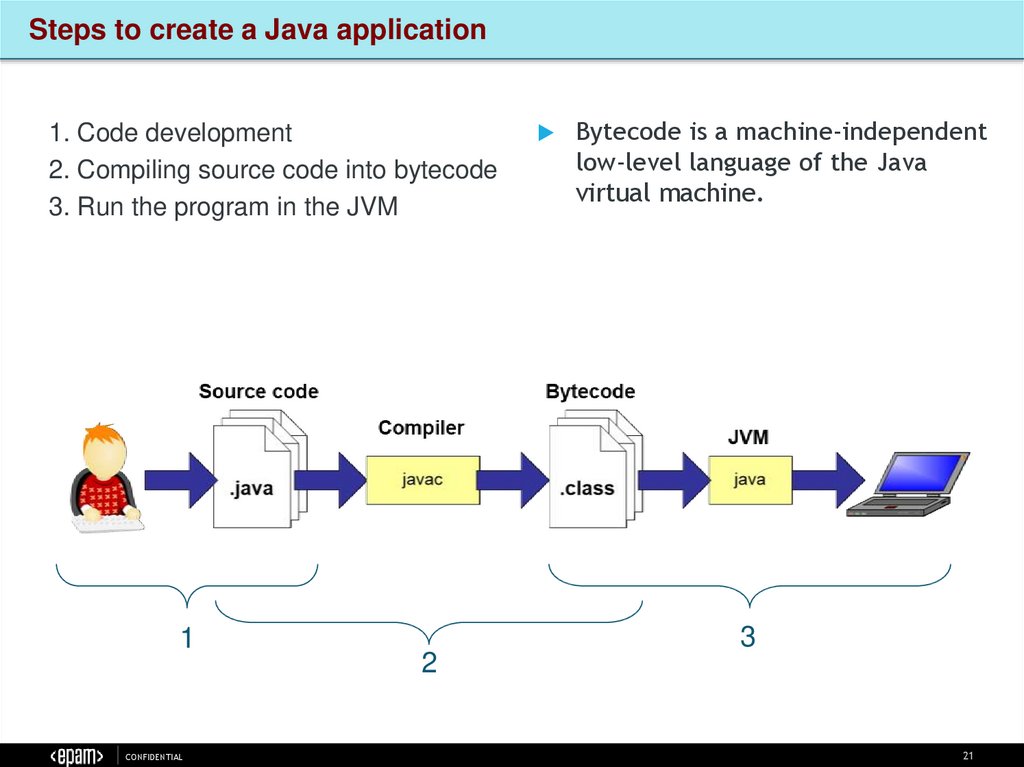
Steps to create a Java application1. Code development
2. Compiling source code into bytecode
3. Run the program in the JVM
1
CONFIDENTIAL
2
Bytecode is a machine-independent
low-level language of the Java
virtual machine.
3
21
22.
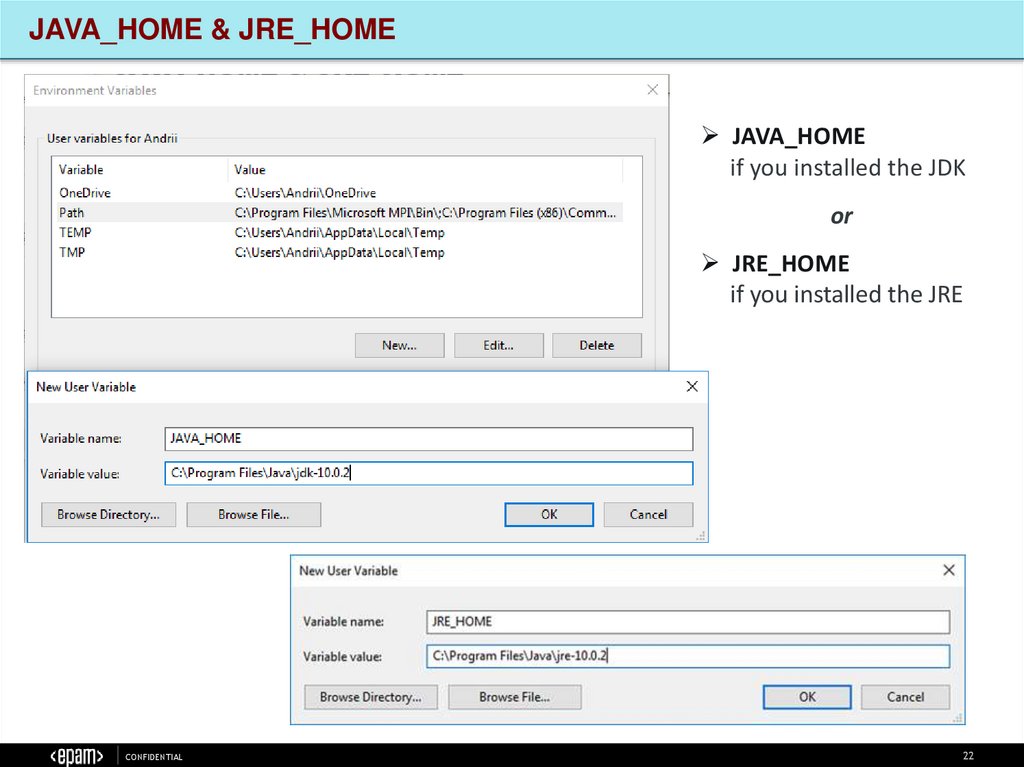
JAVA_HOME & JRE_HOMEJAVA_HOME
if you installed the JDK
or
JRE_HOME
if you installed the JRE
CONFIDENTIAL
22
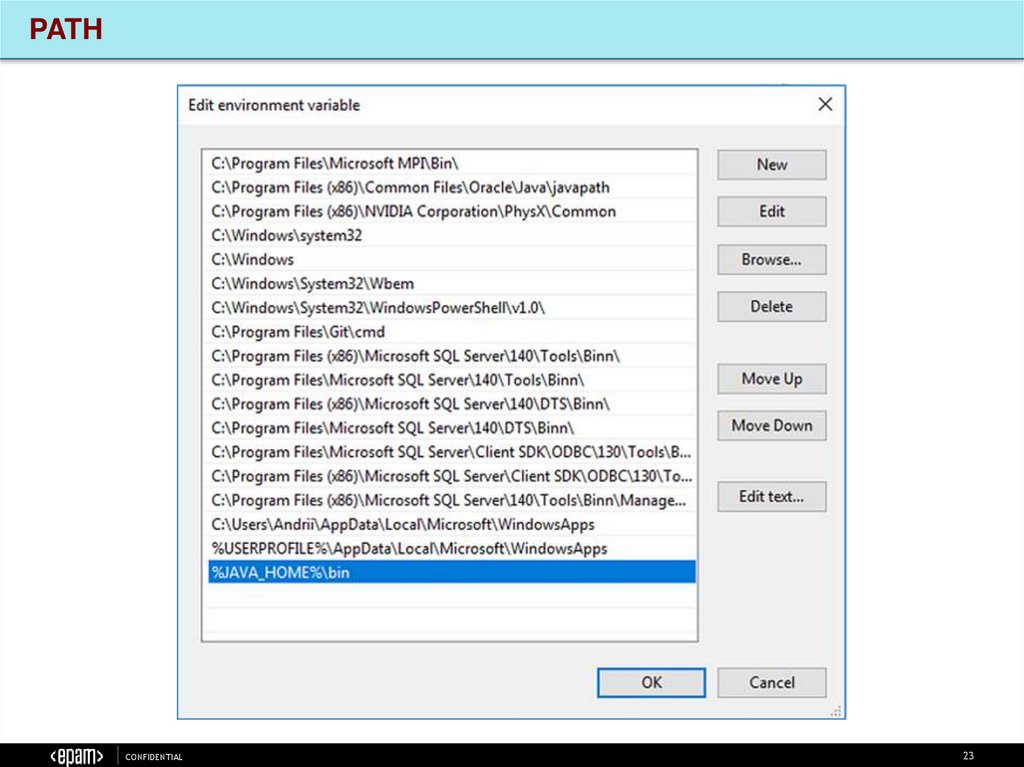
23.
PATHCONFIDENTIAL
23
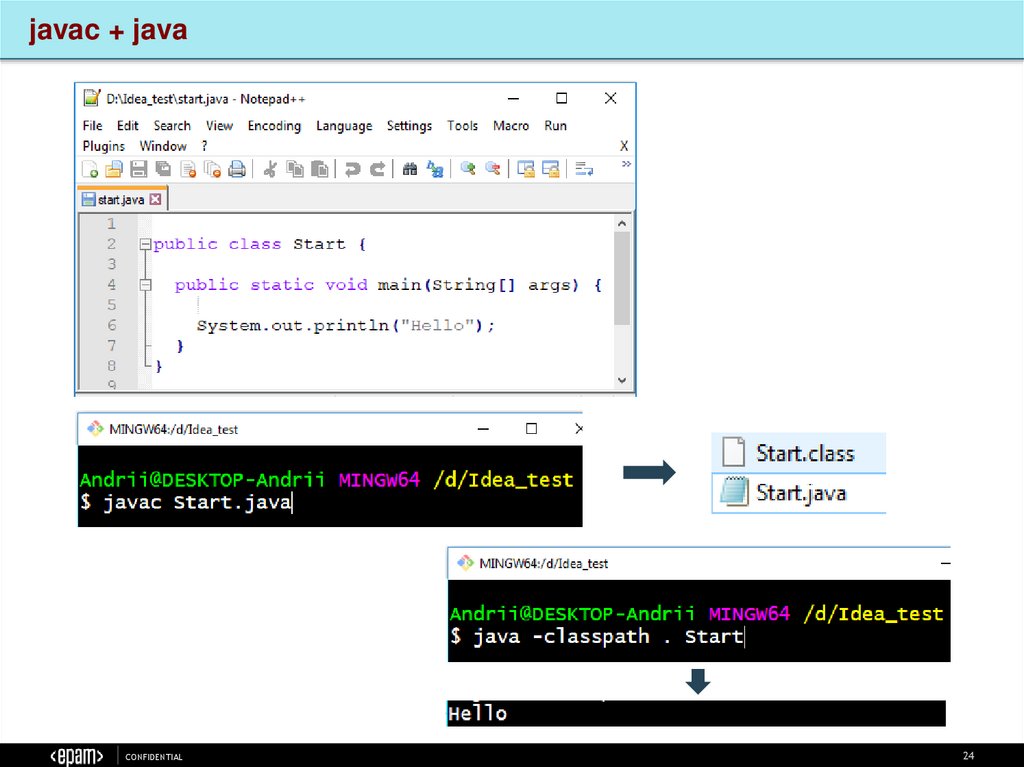
24.
javac + javaCONFIDENTIAL
24
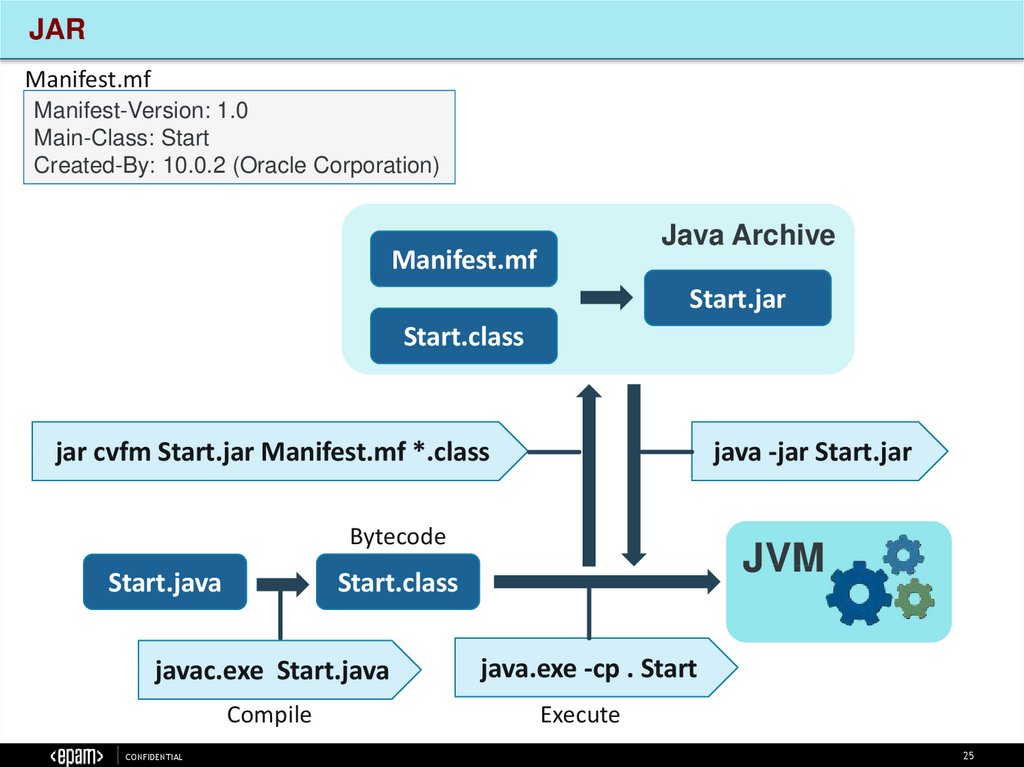
25.
JARManifest.mf
Manifest-Version: 1.0
Main-Class: Start
Created-By: 10.0.2 (Oracle Corporation)
Java Archive
Manifest.mf
Start.jar
Start.class
jar cvfm Start.jar Manifest.mf *.class
java -jar Start.jar
Bytecode
Start.java
javac.exe Start.java
Compile
CONFIDENTIAL
JVM
Start.class
java.exe -cp . Start
Execute
25
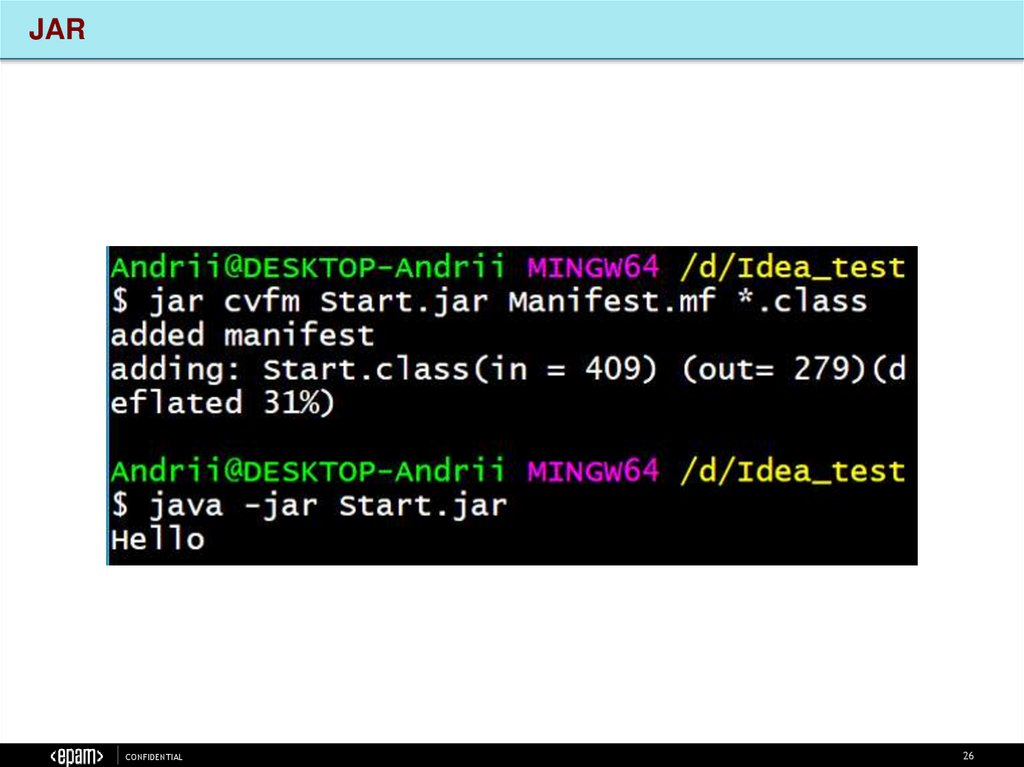
26.
JARCONFIDENTIAL
26
27.
JARLIVE DEMO
CONFIDENTIAL
27
28.
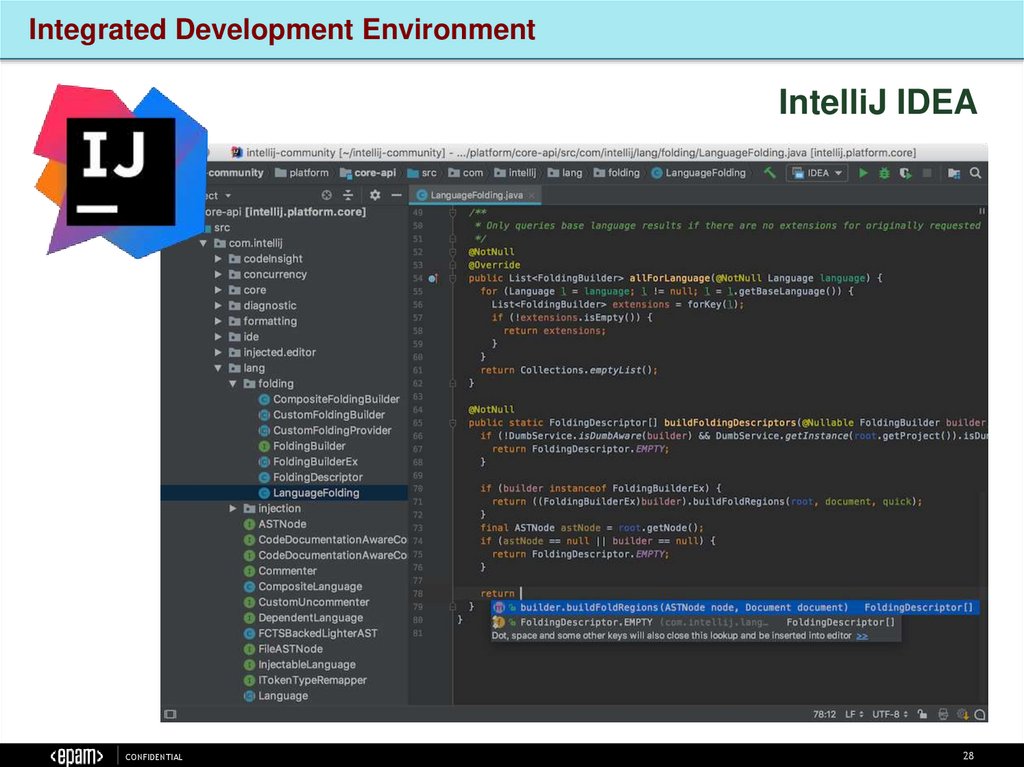
Integrated Development EnvironmentIntelliJ IDEA
CONFIDENTIAL
28
29.
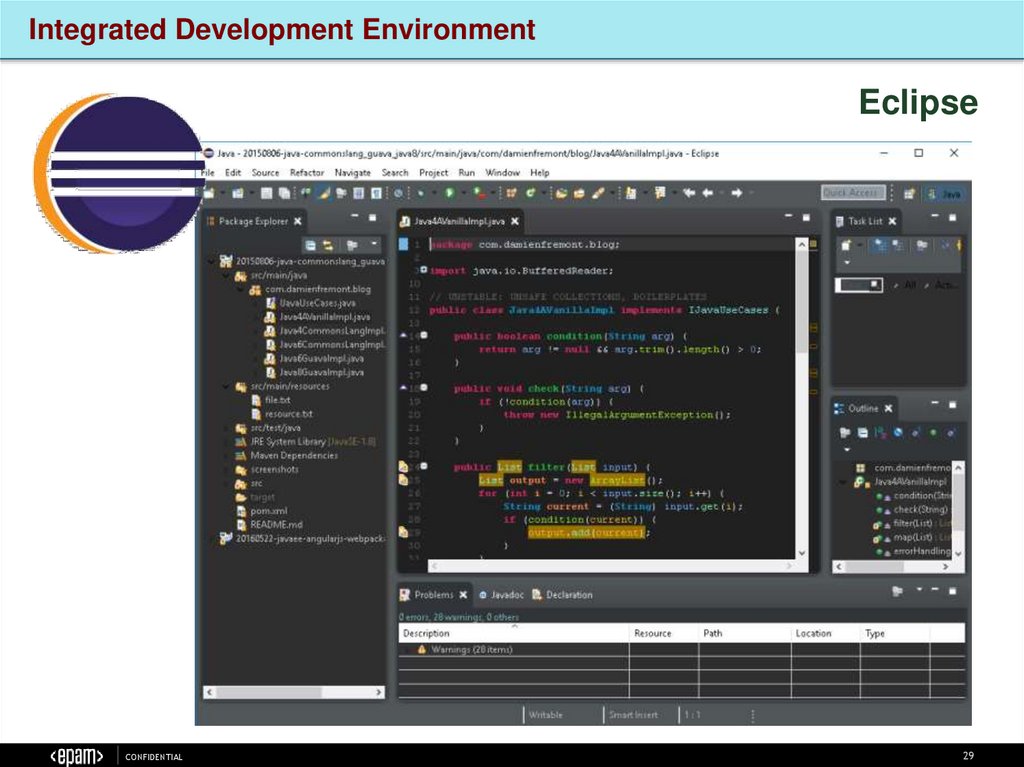
Integrated Development EnvironmentEclipse
CONFIDENTIAL
29
30.
Java FrameworksWeb
Toolkit
CONFIDENTIAL
30
31.
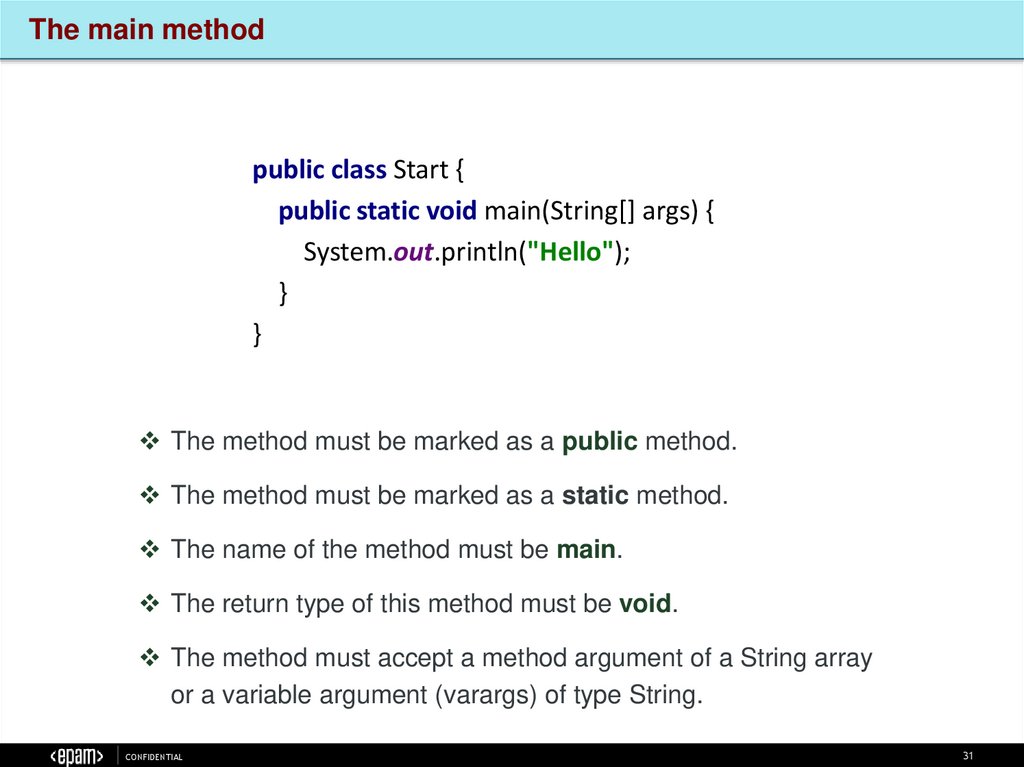
The main methodpublic class Start {
public static void main(String[] args) {
System.out.println("Hello");
}
}
The method must be marked as a public method.
The method must be marked as a static method.
The name of the method must be main.
The return type of this method must be void.
The method must accept a method argument of a String array
or a variable argument (varargs) of type String.
CONFIDENTIAL
31
32.
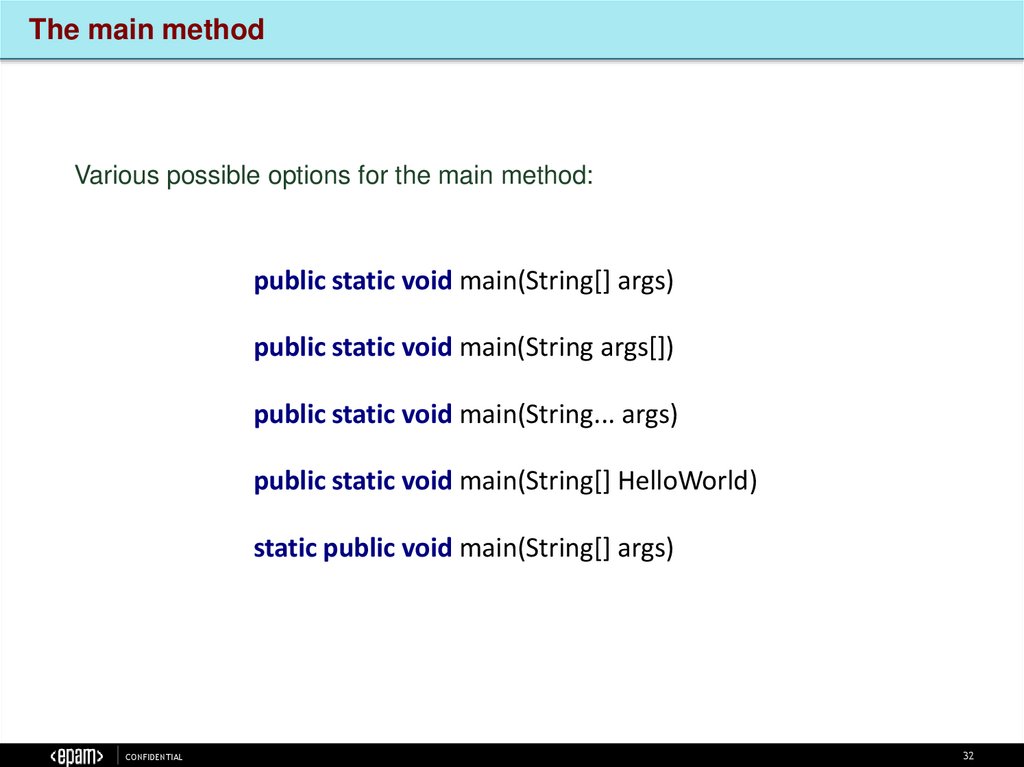
The main methodVarious possible options for the main method:
public static void main(String[] args)
public static void main(String args[])
public static void main(String... args)
public static void main(String[] HelloWorld)
static public void main(String[] args)
CONFIDENTIAL
32
33.
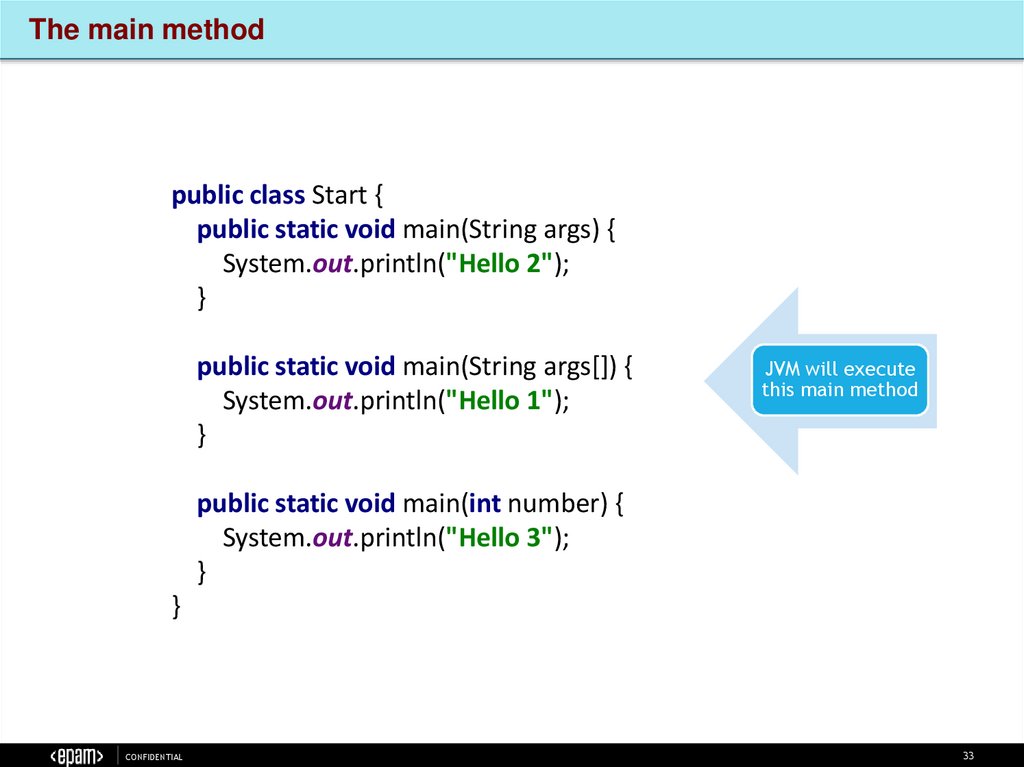
The main methodpublic class Start {
public static void main(String args) {
System.out.println("Hello 2");
}
public static void main(String args[]) {
System.out.println("Hello 1");
}
JVM will execute
this main method
public static void main(int number) {
System.out.println("Hello 3");
}
}
CONFIDENTIAL
33
34.
Code conventionCONFIDENTIAL
34
35.
JavadocCONFIDENTIAL
35
36.
Maven projectLIVE DEMO
CONFIDENTIAL
36
37.
Q&ACONFIDENTIAL
37
38.
Home Work1. Compile and run java app from console.
2. Write program (Maven project), which will pass requirements:
- User enter the interval (for example: [1;100]);
- Program prints odd numbers from start to the end of interval and even from end to
start;
- Program prints the sum of odd and even numbers;
- Program build Fibonacci numbers: F1 will be the biggest odd number and F2 – the
biggest even number, user can enter the size of set (N);
- Program prints percentage of odd and even Fibonacci numbers;
3. Create and generate JavaDoc.
4. Add the following plugins to Maven project: FindBugs, Checkstyle, PMD. Then execute
the command “mvn site” and view the results of its execution in the folder
“target/site”. Fix all errors in the code that plugins will detect.
5. Object-Oriented analysis and design (read info).
CONFIDENTIAL
38









 programming
programming








