Similar presentations:
Week_7_lesson_4_vocabularyCrime and Punishment (1)
1. Vocabulary Crime and Punishment
Astana IT UniversityDepartment of General Disciplines
English for Academic Purposes
B1- level
Vocabulary
Crime and Punishment
Week 7 Lesson 4
2.
Glossary (A–Z)antivirus = software that detects and removes computer viruses and malware
authentication = the process of confirming a person’s identity before giving access to a
system
backup = a copy of important data kept in case the original is lost or damaged
cyberattack = an attempt by hackers to damage or gain illegal access to a computer
system or network
data = information stored or processed on a computer
data breach = when private or sensitive information is accessed or shared without
permission
encryption = a method of protecting information by turning it into a secret code
firewall = a system that protects computers or networks from unauthorized access
hacker = a person who uses computers to get into systems or data without permission
hacking = the act of breaking into computer systems to steal or change information
3.
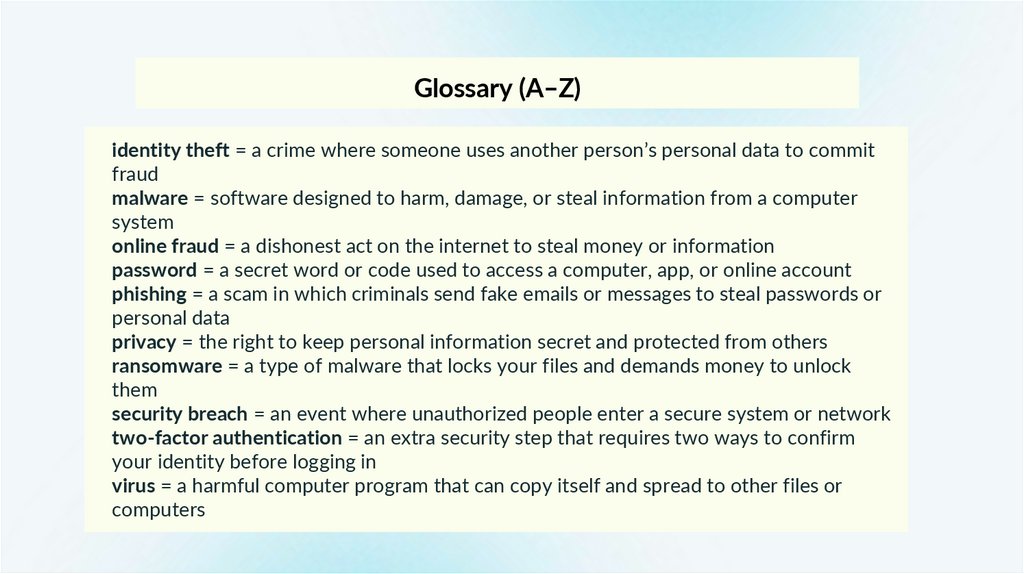
Glossary (A–Z)identity theft = a crime where someone uses another person’s personal data to commit
fraud
malware = software designed to harm, damage, or steal information from a computer
system
online fraud = a dishonest act on the internet to steal money or information
password = a secret word or code used to access a computer, app, or online account
phishing = a scam in which criminals send fake emails or messages to steal passwords or
personal data
privacy = the right to keep personal information secret and protected from others
ransomware = a type of malware that locks your files and demands money to unlock
them
security breach = an event where unauthorized people enter a secure system or network
two-factor authentication = an extra security step that requires two ways to confirm
your identity before logging in
virus = a harmful computer program that can copy itself and spread to other files or
computers
4.
ExercisesExercise 1. Match each situation with the correct item from the box. Two items are extra.
cyberattack, hackers, hacking, access, phishing email, virus, ransomware, password, encryption, firewall,
identity theft, fake online shop, online fraud, backup, antivirus, two-factor authentication, phishing scam, data
leak
5.
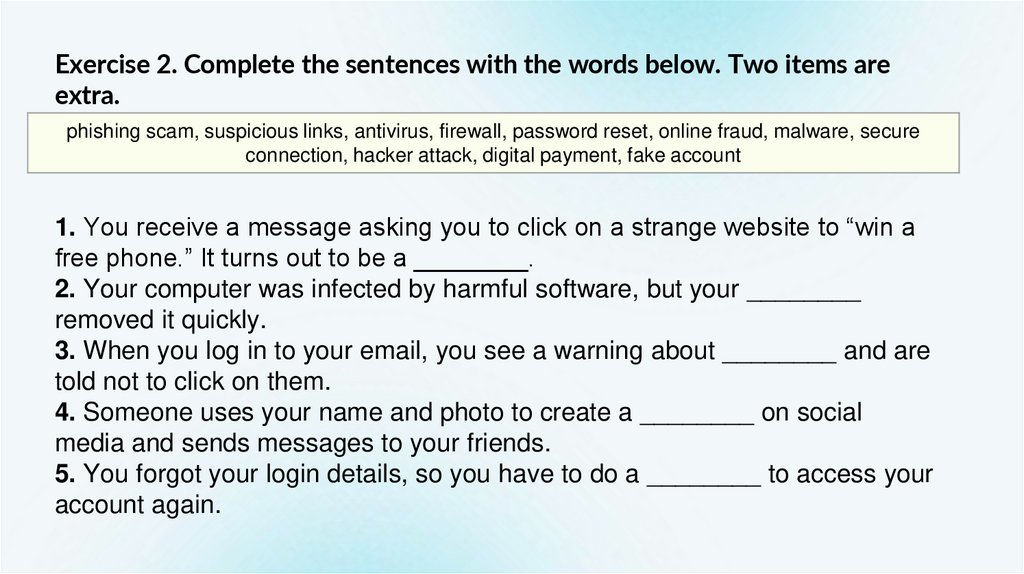
Exercise 2. Complete the sentences with the words below. Two items areextra.
phishing scam, suspicious links, antivirus, firewall, password reset, online fraud, malware, secure
connection, hacker attack, digital payment, fake account
1. You receive a message asking you to click on a strange website to “win a
free phone.” It turns out to be a ________.
2. Your computer was infected by harmful software, but your ________
removed it quickly.
3. When you log in to your email, you see a warning about ________ and are
told not to click on them.
4. Someone uses your name and photo to create a ________ on social
media and sends messages to your friends.
5. You forgot your login details, so you have to do a ________ to access your
account again.
6.
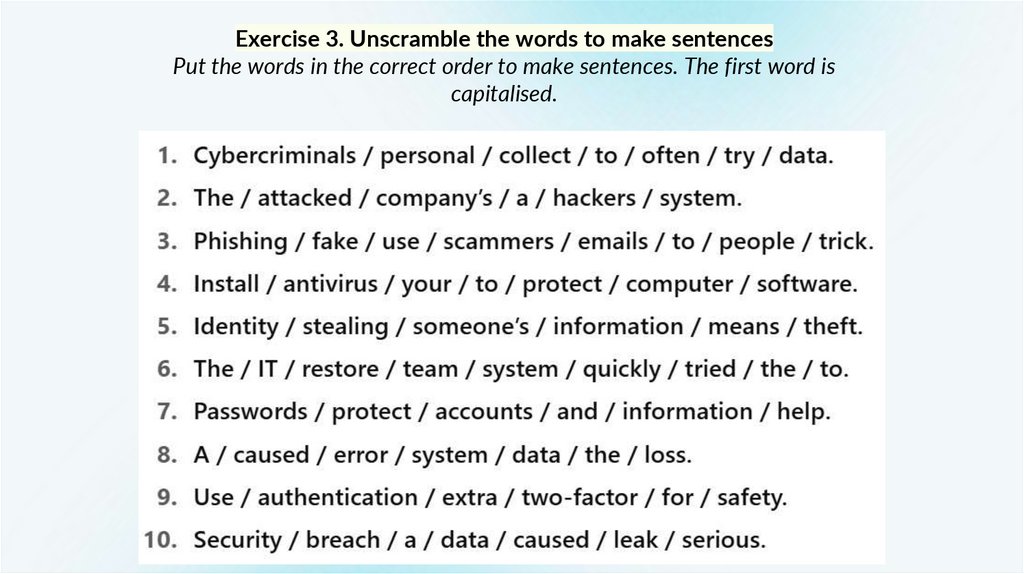
Exercise 3. Unscramble the words to make sentencesPut the words in the correct order to make sentences. The first word is
capitalised.
7.
Exercise 4. Writing TaskCompose sentences using the words from the box.
Use each word in a meaningful sentence about online safety or cybersecurity.
Words in the box:
cyberattack, hackers, phishing email, antivirus, identity theft, malware, password, firewall,
data leak, two-factor authentication
✍ Instructions:
Write one complete sentence for each word. Make sure your sentences show that you
understand the meaning of the word.
Example:
virus → A virus can damage important files on your computer.