Similar presentations:
Digital Signature Cryptography
1.
Digital SignatureCryptography
2. Digital signature
• ‘Digital signature’ means authentication of anyelectronic record by means of an electronic method
• Electronic record means data, record or data
generated, image or sound, received or sent in an
electronic form or microfilm or computer generated
fiche
• Digital Signature Certificate to be issued by Certifying
Authority
• Asymmetric Crypto System and hash functions
details - as prescribed
3. Digital Signature
Basically a digital signature is a two way process,involving two parties:
• The signer (creator of the digital signature) and
• The recipient (verifier of the digital signature).
A digital signature is complete, if and only if, the
recipient successfully verifies it.
4. Need for Digital Signature
It has been realized that Internet being a publicnetwork would never be secure enough and there
would always be a fear of interception, transmission
errors, delays, deletion, authenticity or verification of
an electronic message using Internet as a medium.
Hence the goal was to protect the message, not the
medium.
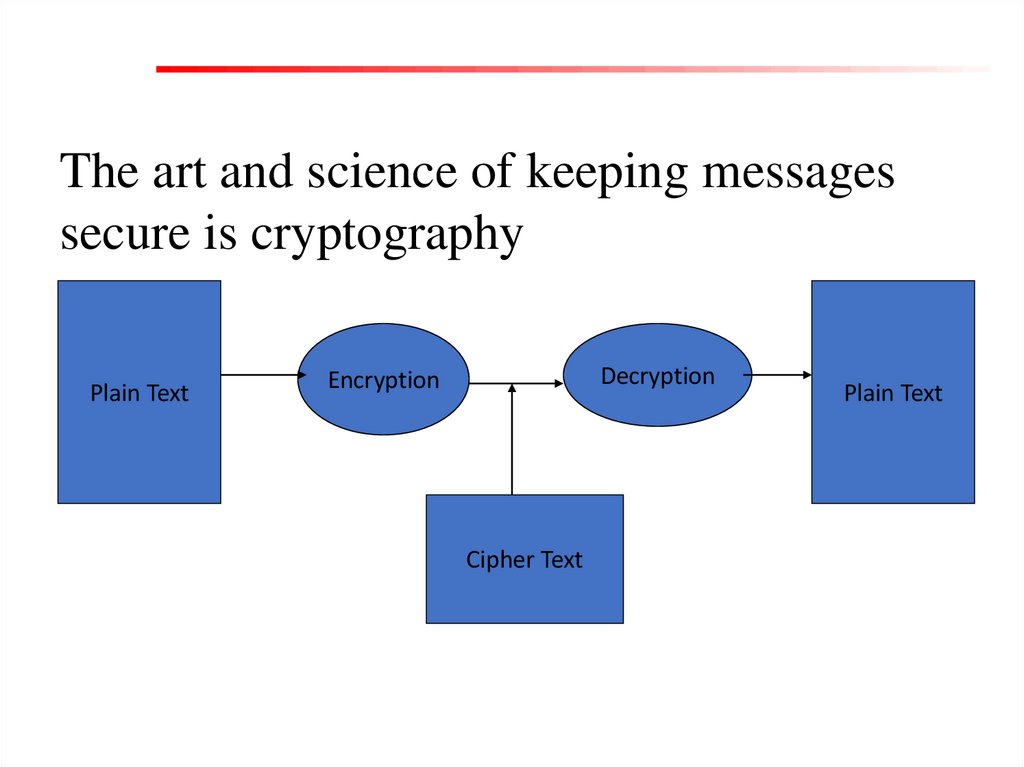
5.
The art and science of keeping messagessecure is cryptography
Plain Text
Decryption
Encryption
Cipher Text
Plain Text
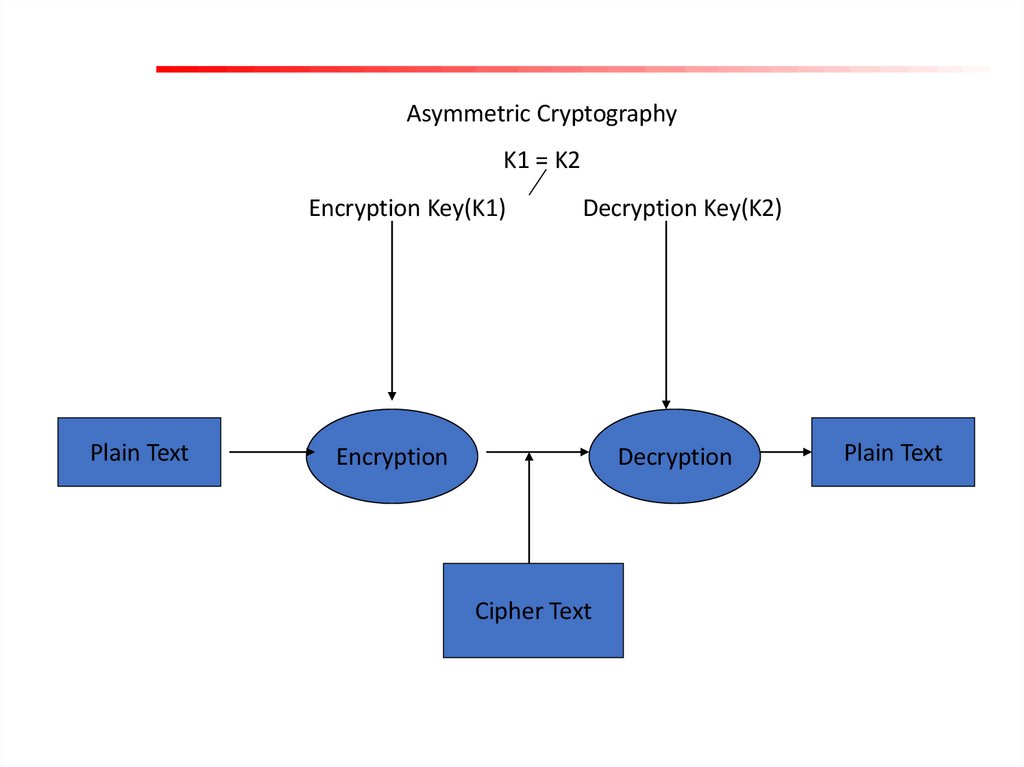
6.
Asymmetric CryptographyK1 = K2
Plain Text
Encryption Key(K1)
Decryption Key(K2)
Encryption
Decryption
Cipher Text
Plain Text
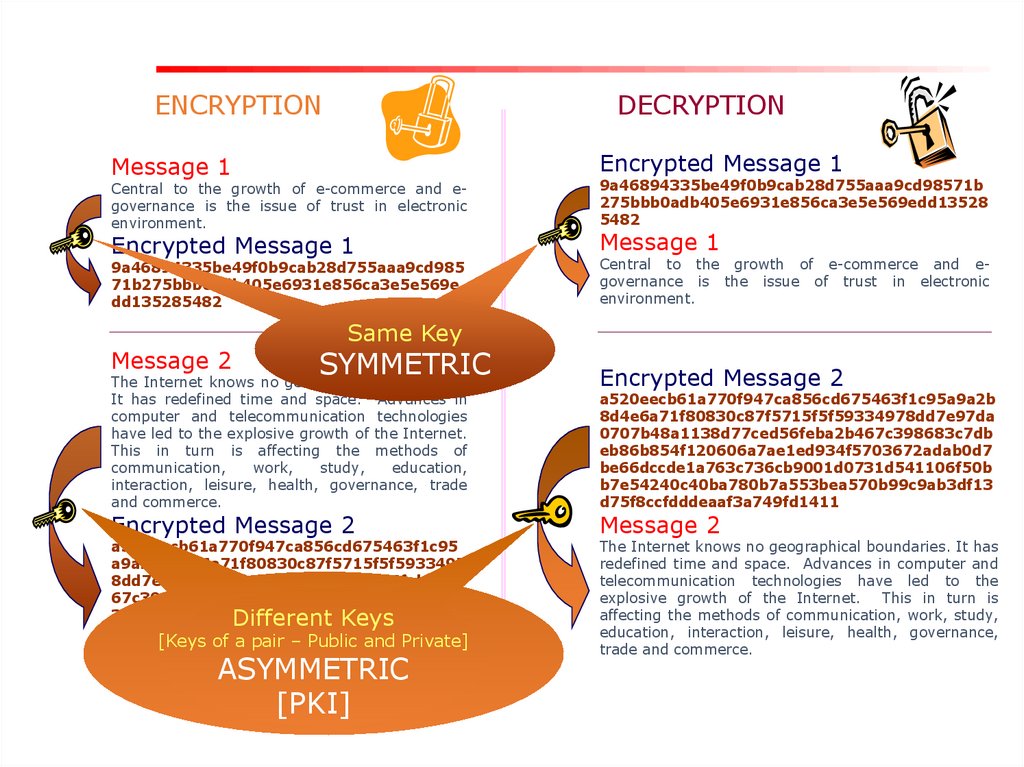
7.
ENCRYPTIONDECRYPTION
Encrypted Message 1
Message 1
Central to the growth of e-commerce and egovernance is the issue of trust in electronic
environment.
9a46894335be49f0b9cab28d755aaa9cd98571b
275bbb0adb405e6931e856ca3e5e569edd13528
5482
9a46894335be49f0b9cab28d755aaa9cd985
71b275bbb0adb405e6931e856ca3e5e569e
dd135285482
Central to the growth of e-commerce and egovernance is the issue of trust in electronic
environment.
Encrypted Message 1
Message 2
Message 1
Same Key
SYMMETRIC
The Internet knows no geographical boundaries.
It has redefined time and space. Advances in
computer and telecommunication technologies
have led to the explosive growth of the Internet.
This in turn is affecting the methods of
communication,
work,
study,
education,
interaction, leisure, health, governance, trade
and commerce.
Encrypted Message 2
a520eecb61a770f947ca856cd675463f1c95
a9a2b8d4e6a71f80830c87f5715f5f5933497
8dd7e97da0707b48a1138d77ced56feba2b4
67c398683c7dbeb86b854f120606a7ae1ed9
34f5703672adab0d7be66dccde1a763c736c
b9001d0731d541106f50bb7e54240c40ba7
[Keys of a pair – Public and Private]
80b7a553bea570b99c9ab3df13d75f8ccfddd
eaaf3a749fd1411
Different Keys
ASYMMETRIC
[PKI]
Encrypted Message 2
a520eecb61a770f947ca856cd675463f1c95a9a2b
8d4e6a71f80830c87f5715f5f59334978dd7e97da
0707b48a1138d77ced56feba2b467c398683c7db
eb86b854f120606a7ae1ed934f5703672adab0d7
be66dccde1a763c736cb9001d0731d541106f50b
b7e54240c40ba780b7a553bea570b99c9ab3df13
d75f8ccfdddeaaf3a749fd1411
Message 2
The Internet knows no geographical boundaries. It has
redefined time and space. Advances in computer and
telecommunication technologies have led to the
explosive growth of the Internet.
This in turn is
affecting the methods of communication, work, study,
education, interaction, leisure, health, governance,
trade and commerce.
8.
9.
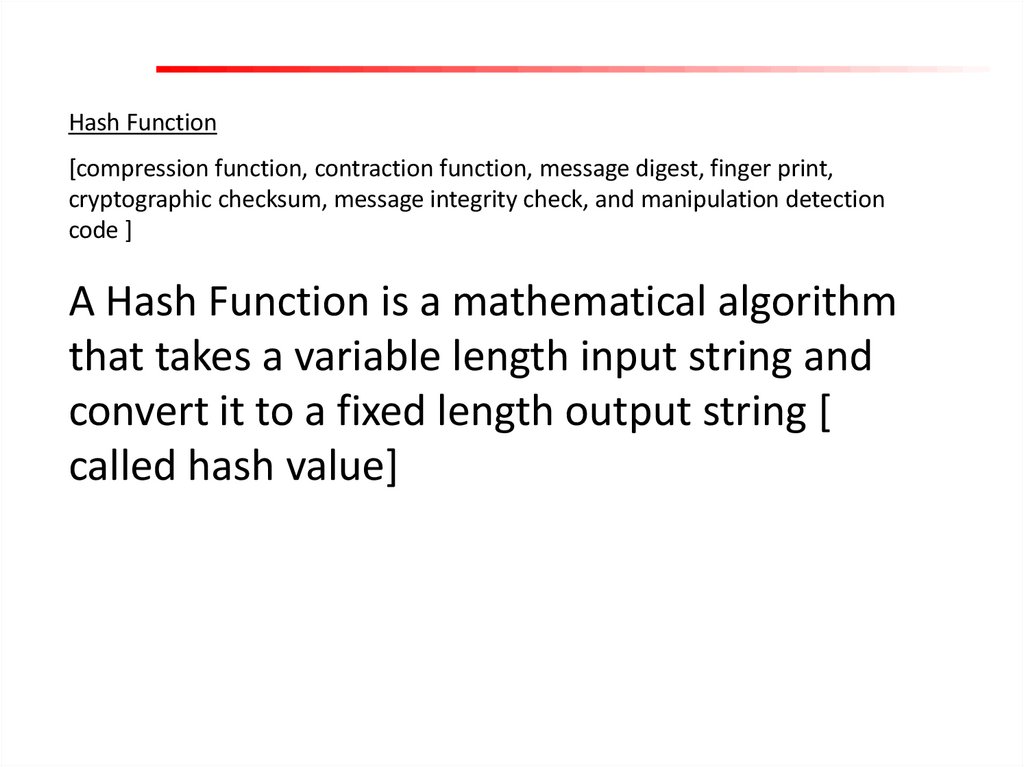
Hash Function[compression function, contraction function, message digest, finger print,
cryptographic checksum, message integrity check, and manipulation detection
code ]
A Hash Function is a mathematical algorithm
that takes a variable length input string and
convert it to a fixed length output string [
called hash value]
10.
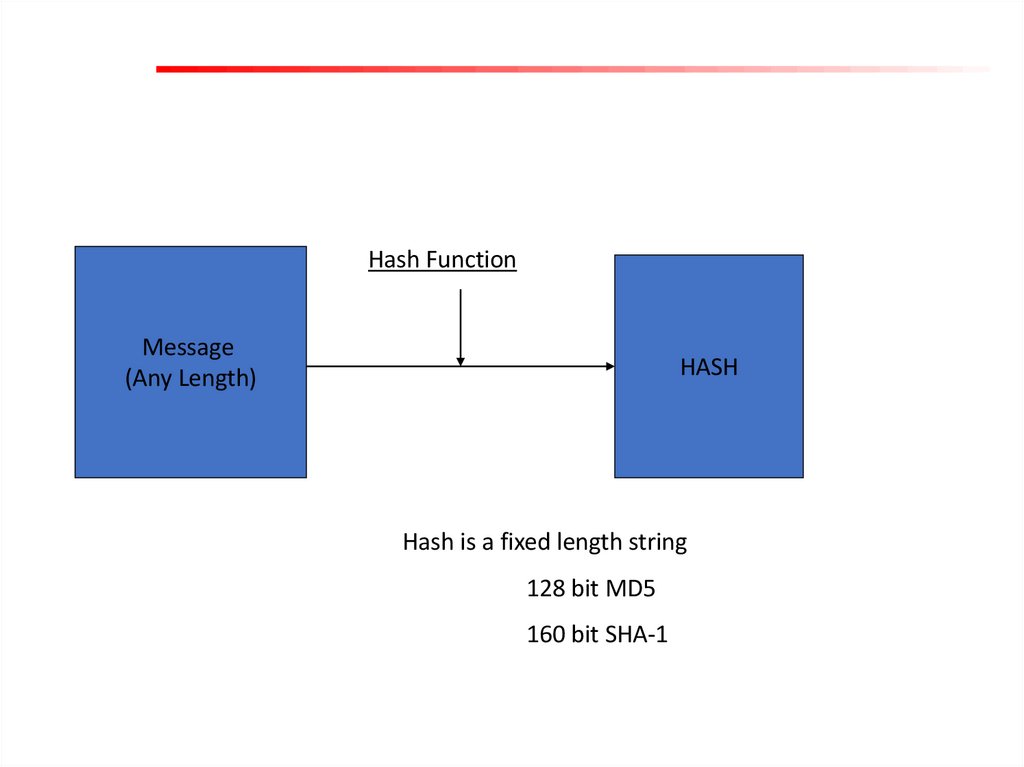
Hash FunctionMessage
(Any Length)
HASH
Hash is a fixed length string
128 bit MD5
160 bit SHA-1
11.
Digital Signature12.
Basically a digital signature is a two way process,involving two parties:
• The signer (creator of the digital signature) and
• The recipient (verifier of the digital signature).
A digital signature is complete, if and only if, the
recipient successfully verifies it.
13.
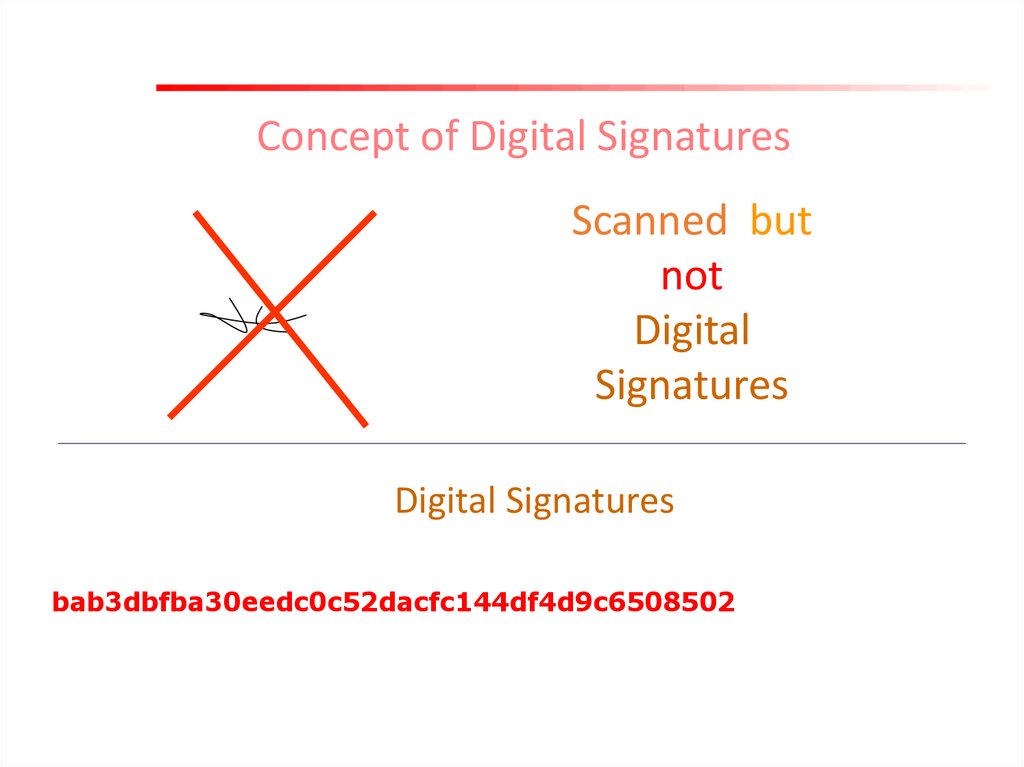
Concept of Digital SignaturesScanned but
not
Digital
Signatures
Digital Signatures
bab3dbfba30eedc0c52dacfc144df4d9c6508502
14.
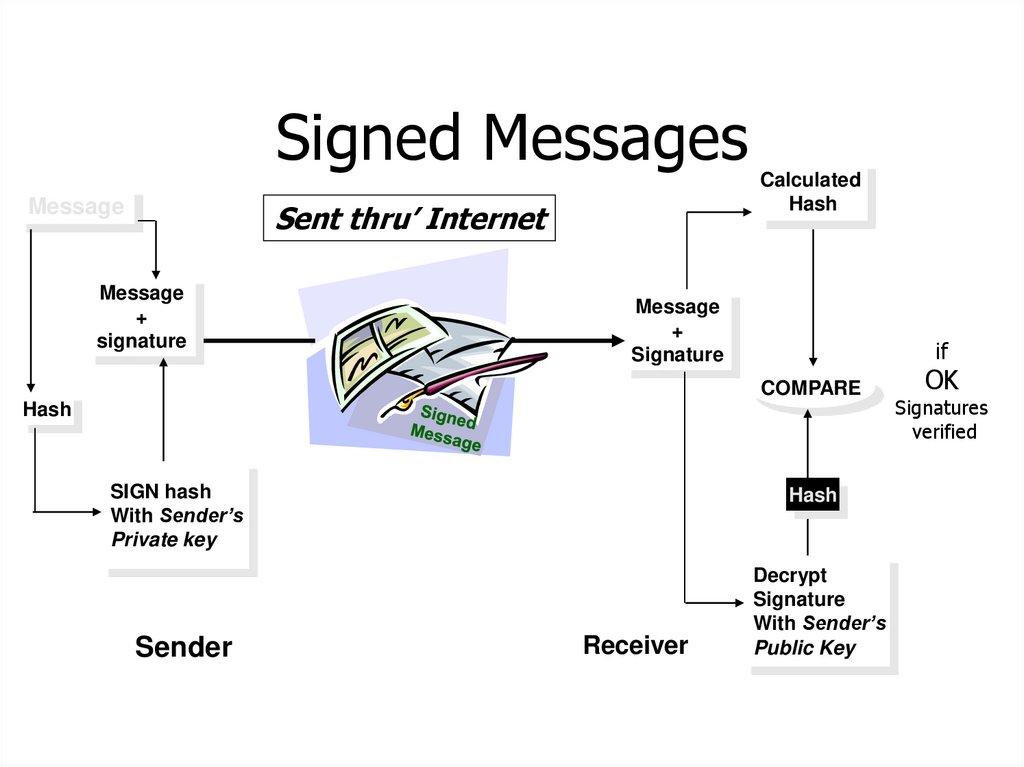
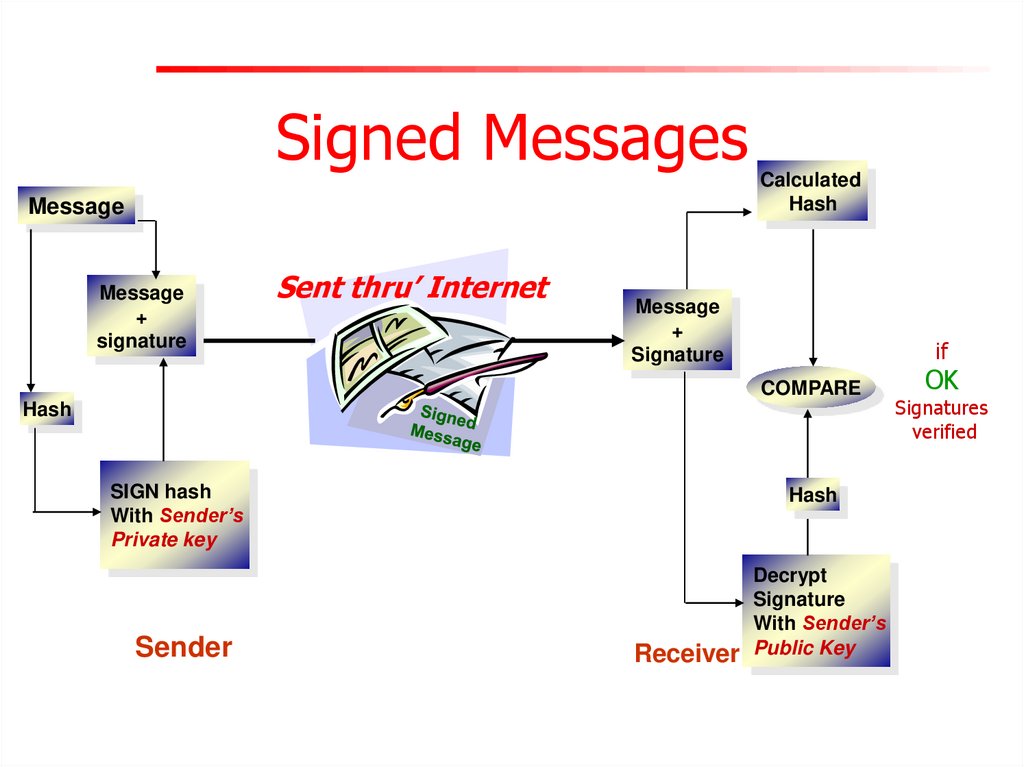
Signed MessagesMessage
Sent thru’ Internet
Message
+
signature
Calculated
Hash
Message
+
Signature
if
COMPARE
Hash
SIGN hash
With Sender’s
Private key
Sender
Hash
Receiver
Decrypt
Signature
With Sender’s
Public Key
OK
Signatures
verified
15.
Signed MessagesMessage
Message
+
signature
Sent thru’ Internet
Calculated
Hash
Message
+
Signature
if
COMPARE
Hash
SIGN hash
With Sender’s
Private key
Sender
Hash
Decrypt
Signature
With Sender’s
Receiver Public Key
OK
Signatures
verified
16.
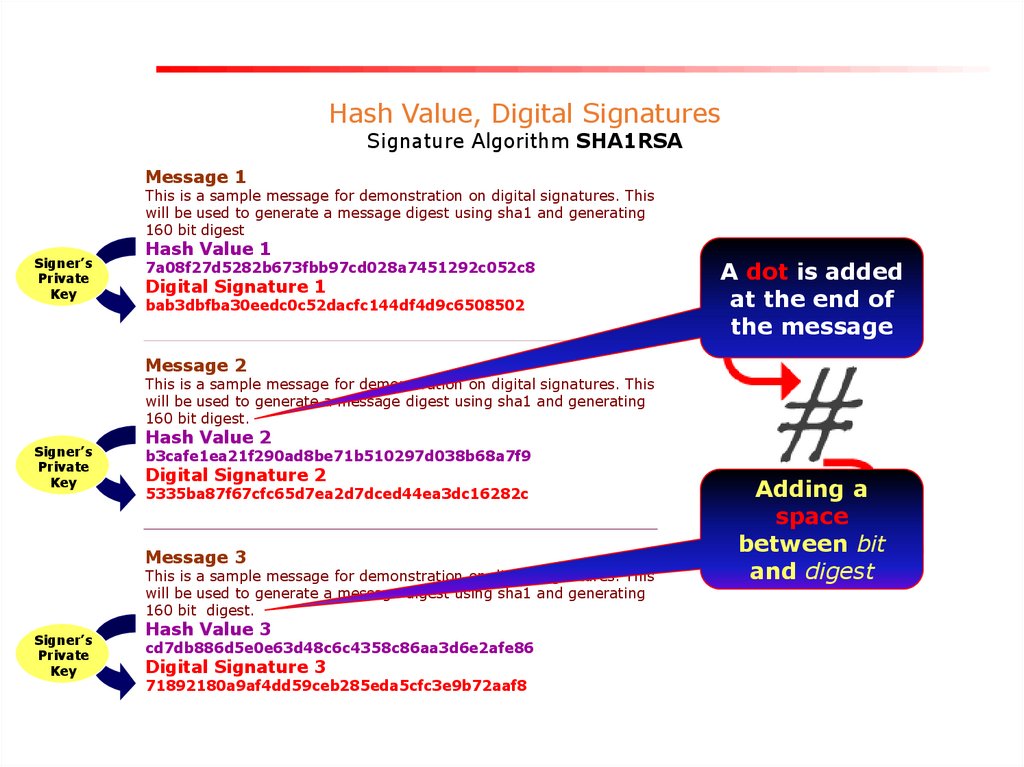
Hash Value, Digital SignaturesSignature Algorithm SHA1RSA
Message 1
This is a sample message for demonstration on digital signatures. This
will be used to generate a message digest using sha1 and generating
160 bit digest
Signer’s
Private
Key
Hash Value 1
7a08f27d5282b673fbb97cd028a7451292c052c8
Digital Signature 1
bab3dbfba30eedc0c52dacfc144df4d9c6508502
A dot is added
at the end of
the message
Message 2
This is a sample message for demonstration on digital signatures. This
will be used to generate a message digest using sha1 and generating
160 bit digest.
Signer’s
Private
Key
Hash Value 2
b3cafe1ea21f290ad8be71b510297d038b68a7f9
Digital Signature 2
5335ba87f67cfc65d7ea2d7dced44ea3dc16282c
Message 3
This is a sample message for demonstration on digital signatures. This
will be used to generate a message digest using sha1 and generating
160 bit digest.
Signer’s
Private
Key
Hash Value 3
cd7db886d5e0e63d48c6c4358c86aa3d6e2afe86
Digital Signature 3
71892180a9af4dd59ceb285eda5cfc3e9b72aaf8
Adding a
space
between bit
and digest
17.
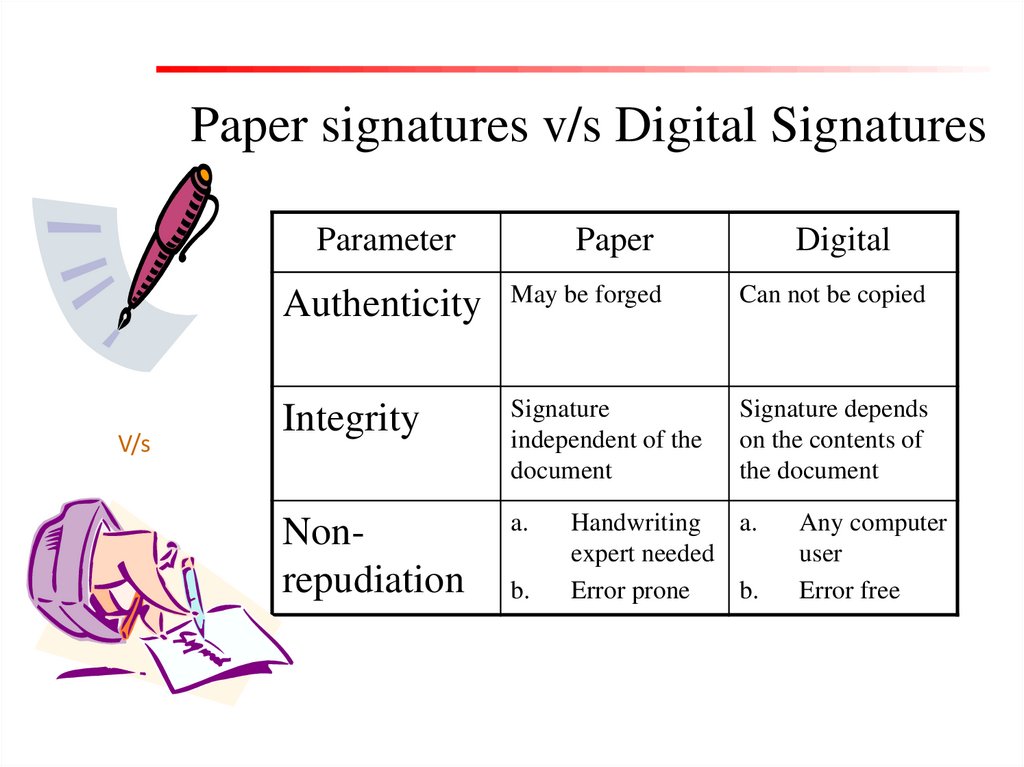
Paper signatures v/s Digital SignaturesParameter
V/s
Paper
Digital
Authenticity
May be forged
Can not be copied
Integrity
Signature
independent of the
document
Signature depends
on the contents of
the document
Nonrepudiation
a.
b.
Handwriting
a.
expert needed
Error prone
b.
Any computer
user
Error free
18.
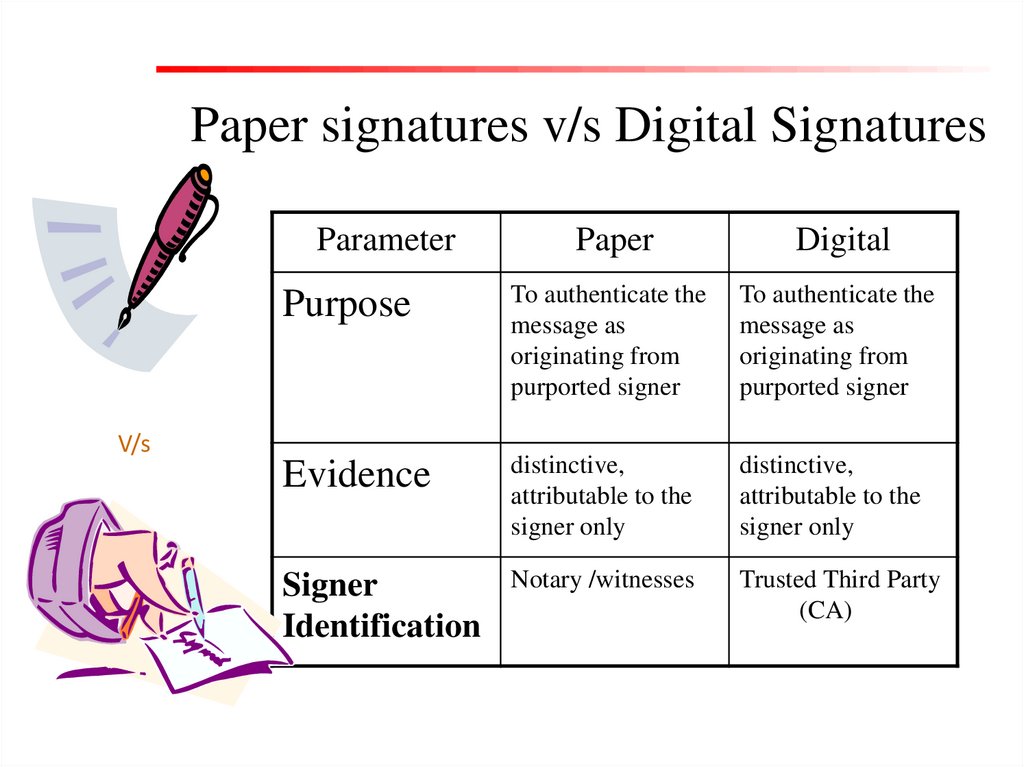
Paper signatures v/s Digital SignaturesParameter
Paper
Digital
Purpose
To authenticate the
message as
originating from
purported signer
To authenticate the
message as
originating from
purported signer
Evidence
distinctive,
attributable to the
signer only
distinctive,
attributable to the
signer only
Signer
Identification
Notary /witnesses
Trusted Third Party
(CA)
V/s
19.
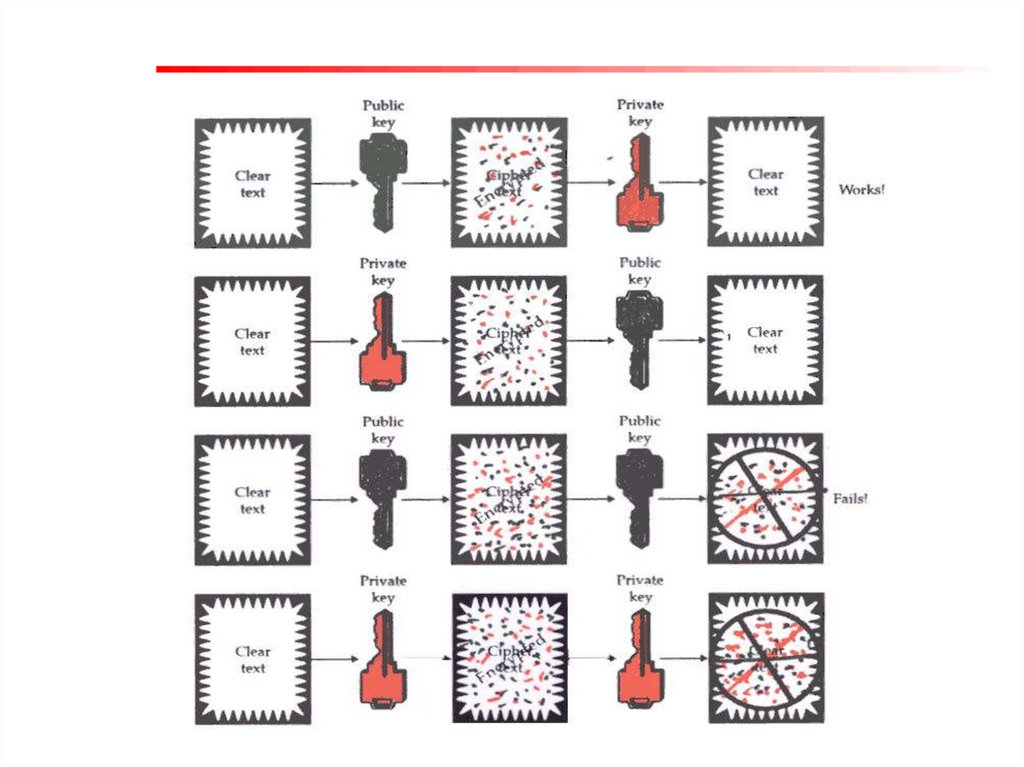
Digital signatures are based onasymmetric,
or
public
key,
cryptography and are capable of
fulfilling the demand of burgeoning ecommerce by not only providing
message authentication, integrity and
non-repudiation function but also
making it highly scalable.
20.
The basic problem with the aforesaid digitalsignature regime is that it operates in online,
software driven space, without human
intervention.
Sender sends a digitally signed message; recipient
receives and verifies it.
The only requirement is that both sender and the
recipient to have digital signature software at their
respective ends.








 informatics
informatics








