Similar presentations:
Transbaikal State University
1.
Transbaikal State UniversityPower Engineering Faculty
The Department of Computer Science,
Technique and Applied Math
Encryption
Is done by Budaev Gennady,
student of group CMC-21
2.
What is encryption?• Data encryption is the process of converting data from
a readable format to a scrambled piece of information
• This is done to prevent theft confidential data in transit
• Nowadays it can be applied to documents, files,
messages, or any other form of communication over a
network
3.
The purpose• to show the importance of data protection
• to inform you about the basics of encryption
4.
Importance• Humanity has become significantly more dependent
on technology, especially online communications
• Most of the communications we conduct on a personal
and business level online using smartphones, tablets
and computers
• Considering the elevated risk of cybercrime today, every
person and group that uses the internet should be
familiar with basic encryption techniques
5.
Encryption protects• our data when it’s located on our computers and in data
centers, and it protects it when it’s transmitted around
the Internet
• our conversations, whether video, voice, or text. It
protects our privacy, our bank accounts.
• our anonymity
• our private life
6.
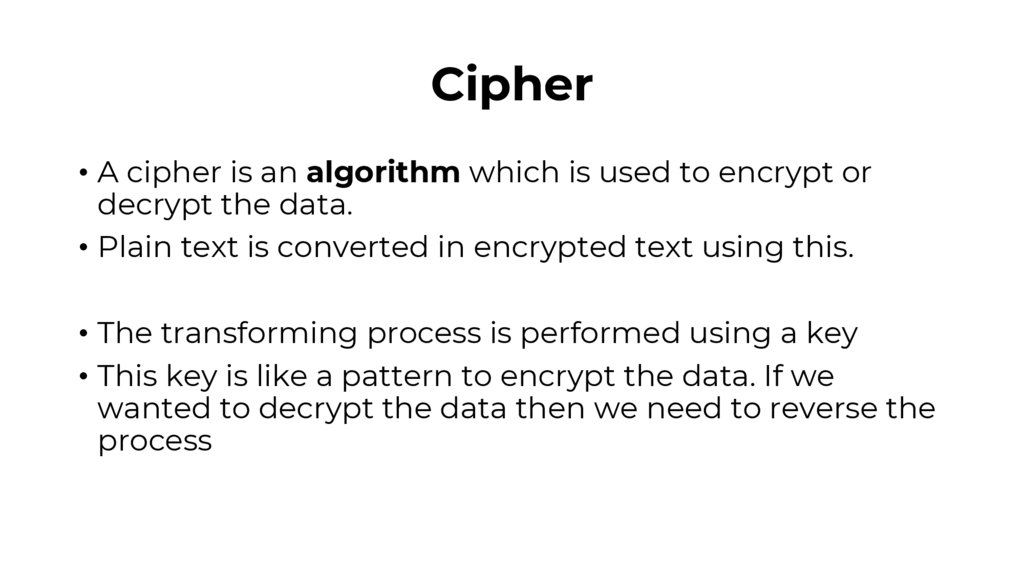
Cipher• A cipher is an algorithm which is used to encrypt or
decrypt the data.
• Plain text is converted in encrypted text using this.
• The transforming process is performed using a key
• This key is like a pattern to encrypt the data. If we
wanted to decrypt the data then we need to reverse the
process
7.
The Caesar Cipher• Text : ABCDEFGHIJKLMNOPQRSTUVWXYZ
• Shift: 3
8.
The Caesar Cipher• Text : ABCDEFGHIJKLMNOPQRSTUVWXYZ
• Shift: 3
• Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
9.
The Caesar Cipher• Text : ABCDEFGHIJKLMNOPQRSTUVWXYZ
• Shift: 3
• Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
• Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
• Shift: 3
• Text: ABCDEFGHIJKLMNOPQRSTUVWXYZ
10.
The Caesar Cipher• Text : ABCDEFGHIJKLMNOPQRSTUVWXYZ
• Shift: 3
• Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
• Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
1. Plain text
2. Encrypted text
3. Decrypted text
4. Key
• Shift: 3
• Text: ABCDEFGHIJKLMNOPQRSTUVWXYZ
11.
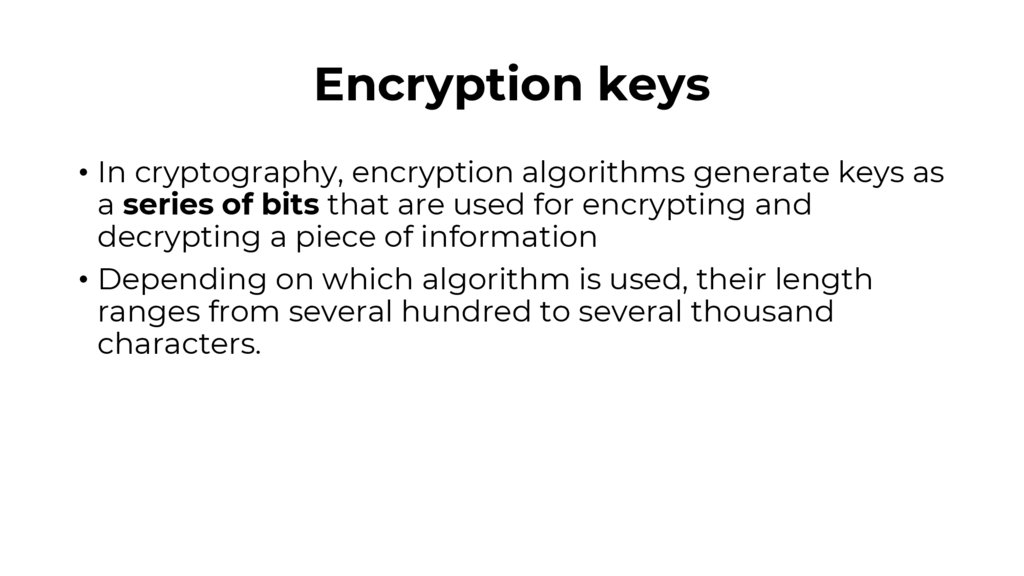
Encryption keys• In cryptography, encryption algorithms generate keys as
a series of bits that are used for encrypting and
decrypting a piece of information
• Depending on which algorithm is used, their length
ranges from several hundred to several thousand
characters.
12.
Symmetric | Asymmetric13.
Symmetric | Asymmetric14.
Symmetric | Asymmetric• Symmetric encryption algorithms use the same key to
perform both the encryption and decryption functions
• This method requires the sender and the receiver to have
access to the same key
15.
16.
17.
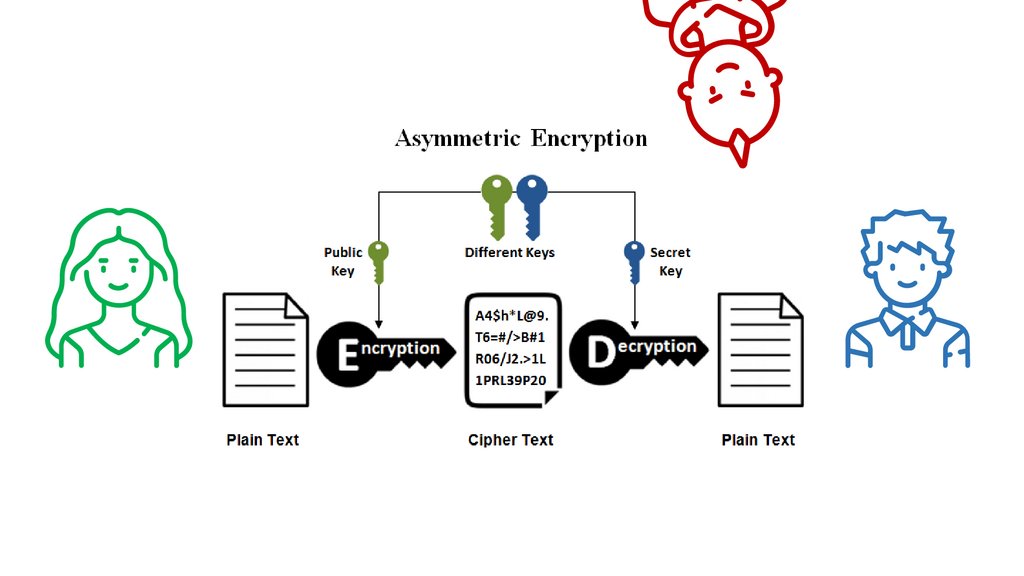
Symmetric | Asymmetric• This method uses two keys for the encryption process: a
public and a private key, which are mathematically linked
• The user employs one key for encryption and the other for
decryption
• The public key is freely available to anyone, but the private
key remains with the intended recipients only, who need it
to decipher the messages
18.
19.
20.
21.
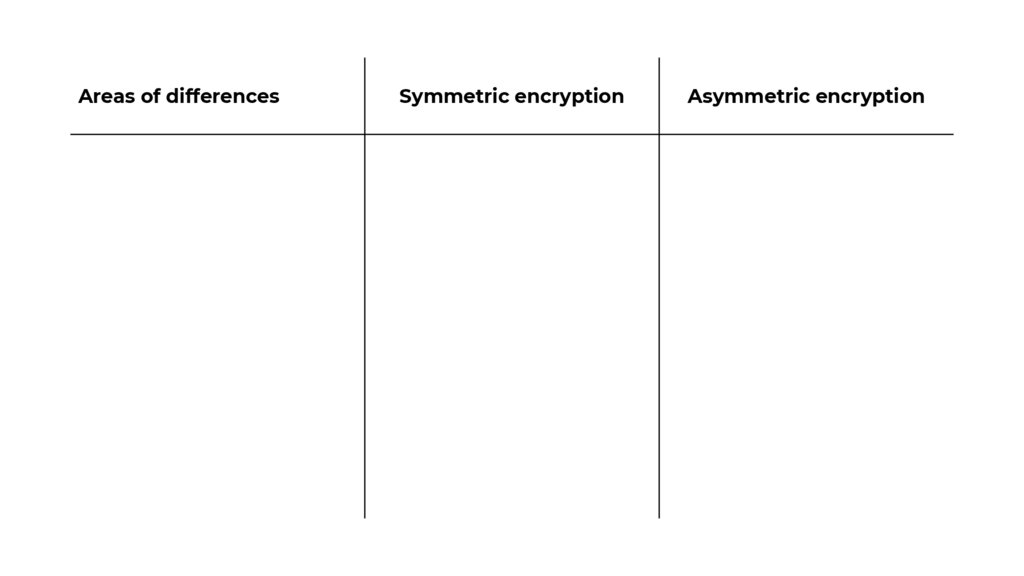
Areas of differencesSymmetric encryption
Asymmetric encryption
22.
Areas of differencesKey lengths
Symmetric encryption
128-bit or 256-bit
Asymmetric encryption
2048-bit or higher
23.
Areas of differencesSymmetric encryption
Asymmetric encryption
Key lengths
128-bit or 256-bit
2048-bit or higher
Data volume
Used in transmitting large
data volume
Used in transmitting low
data volume
24.
Areas of differencesSymmetric encryption
Asymmetric encryption
Key lengths
128-bit or 256-bit
2048-bit or higher
Data volume
Used in transmitting large
data volume
Used in transmitting low
data volume
Consumption of resources
Works with lesser usage of
resources
Works with high resource
consumption
25.
Areas of differencesSymmetric encryption
Asymmetric encryption
Key lengths
128-bit or 256-bit
2048-bit or higher
Data volume
Used in transmitting large
data volume
Used in transmitting low
data volume
Consumption of resources
Works with lesser usage of
resources
Works with high resource
consumption
Speed
It’s fast
It’s comparatively slower
26.
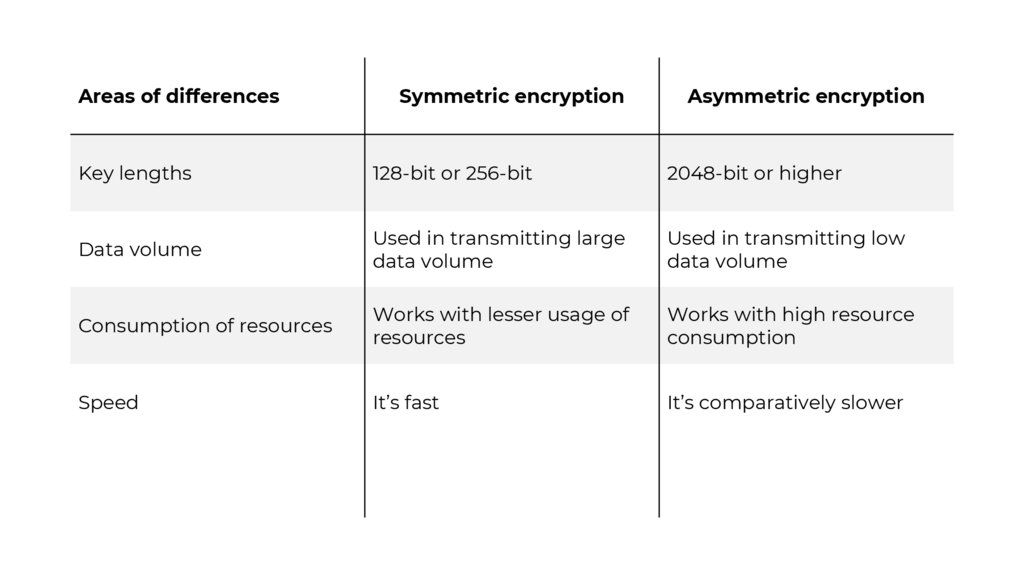
Areas of differencesSymmetric encryption
Asymmetric encryption
Key lengths
128-bit or 256-bit
2048-bit or higher
Data volume
Used in transmitting large
data volume
Used in transmitting low
data volume
Consumption of resources
Works with lesser usage of
resources
Works with high resource
consumption
Speed
It’s fast
It’s comparatively slower
Security
Offers less security
Provides more protection
27.
Security | Speed• While choosing between symmetric and asymmetric
encryption, you’ll come across a situation that will
require you to make a trade-off between security and
speed
• Encrypting a message provides security independently
of what encryption you use. It’s just that the level of
security can vary
• You can use both methods to safeguard the information
better
28.
RSA• The idea of RSA is based on the fact that it is difficult to
decompose into prime multipliers a large number
• The public key consists of two numbers where one
number is a multiplication of two large prime (simple)
numbers
• And private key is also derived from the same two prime
numbers
• Encryption strength totally lies on the key size and if we
double or triple the key size, the strength of encryption
increases exponentially
29.
Generating Public KeyP = 53 and Q = 59
First part of the Public key: n = P*Q = 3127
e is an exponent:
• an integer
• not a multiplier of n
• 1 < e < (P-1)*(Q-1)
e=3
30.
Generating Private KeyF(n) = (P-1)*(Q-1)
F(n) = 3016
Now calculate Private Key, d :
• d = (k*F(n) + 1) / e (for some integer k)
• For k = 2, value of d is 2011.
31.
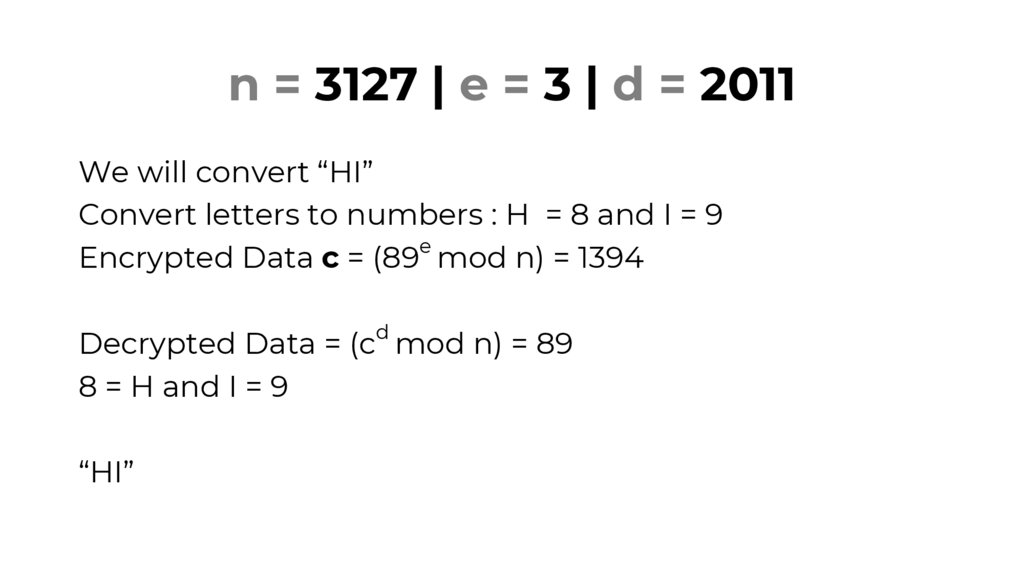
n = 3127 | e = 3 | d = 2011We will convert “HI”
Convert letters to numbers : H = 8 and I = 9
Encrypted Data c = (89e mod n) = 1394
Decrypted Data = (cd mod n) = 89
8 = H and I = 9
“HI”
32.
Prospect• As knowledge has become one of the 21st century's
most important assets, efforts to keep information
secure have correspondingly become increasingly
important
• The science of encryption continues to evolve to defend
against newer and more complex threats and dangers
• Both symmetric and asymmetric cryptographic
systems will likely stay relevant to computer security
33.
34.
List of references• https://www.2brightsparks.com/resources/articles/data-encryption.html
• https://www.simplilearn.com/data-encryption-methods-article#what_is_data_encryption
• https://www.schneier.com/blog/archives/2015/06/why_we_encrypt.html
• https://www.goodcore.co.uk/blog/types-of-encryption/
• https://www.simplilearn.com/data-encryption-methodsarticle#what_are_the_2_types_of_data_encryption_techniques
• https://www.g2.com/articles/symmetric-encryption
• https://www.csoonline.com/article/3513899/what-is-information-security-definitionprinciples-and-jobs.html
• https://www.geeksforgeeks.org/rsa-algorithm-cryptography/





























 informatics
informatics








