Similar presentations:
Symmetric Stream Ciphers in Cryptography (lecture 6)
1.
Symmetric Stream Ciphers inCryptography
2.
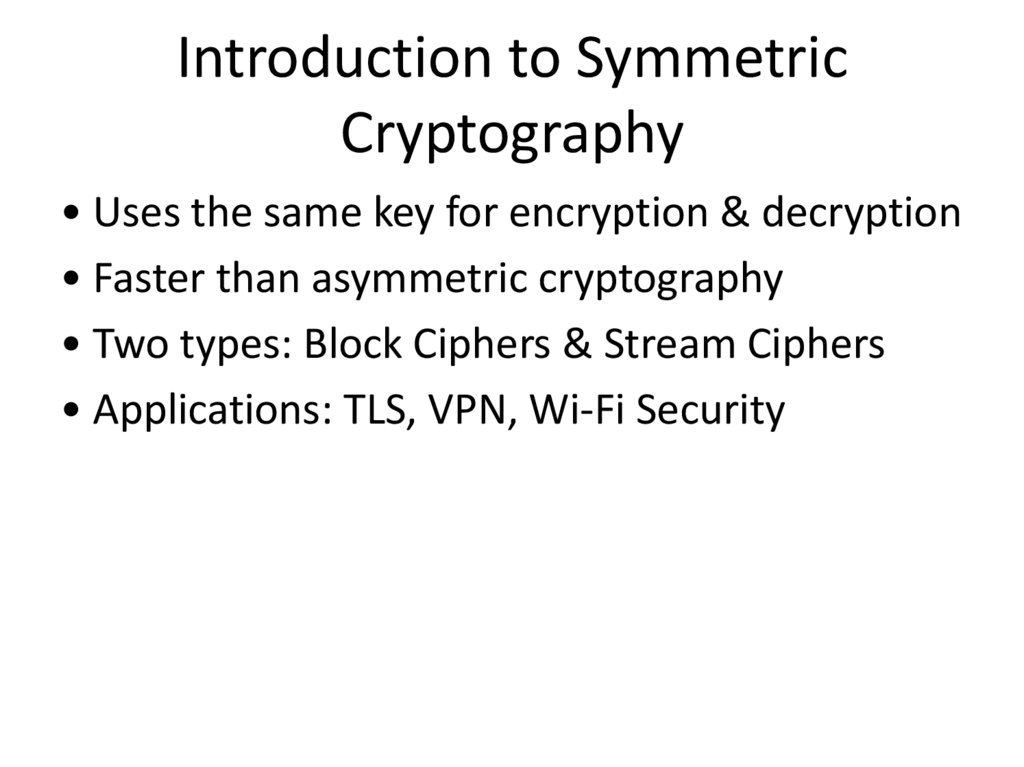
Introduction to SymmetricCryptography
• Uses the same key for encryption & decryption
• Faster than asymmetric cryptography
• Two types: Block Ciphers & Stream Ciphers
• Applications: TLS, VPN, Wi-Fi Security
3.
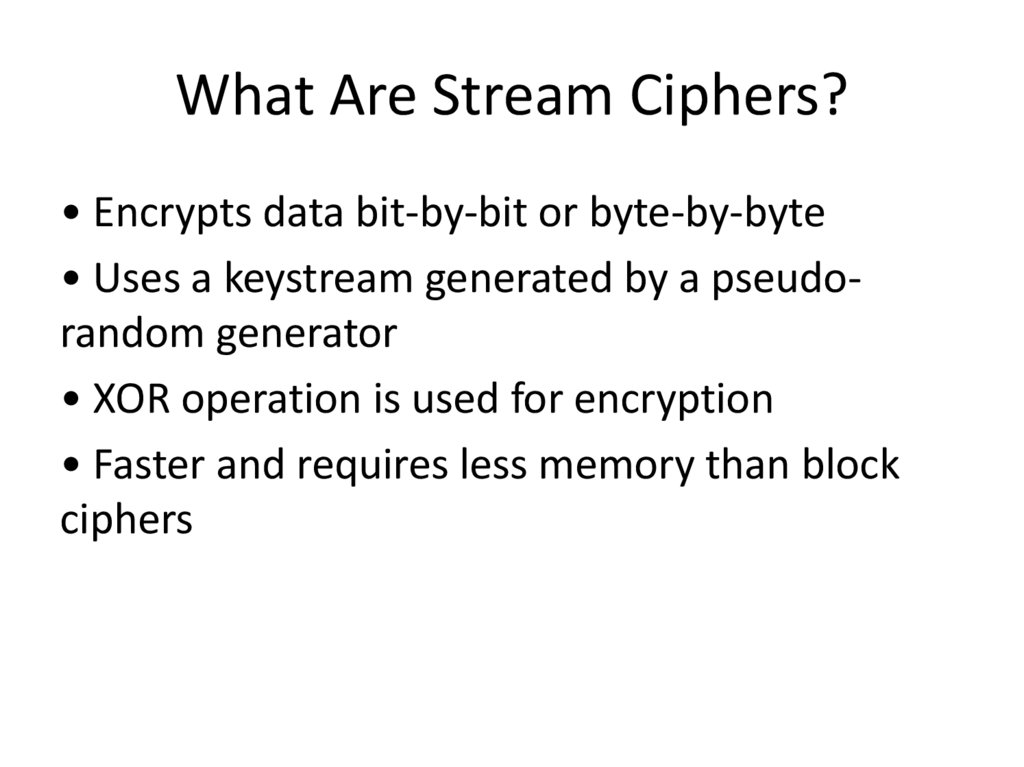
What Are Stream Ciphers?• Encrypts data bit-by-bit or byte-by-byte
• Uses a keystream generated by a pseudorandom generator
• XOR operation is used for encryption
• Faster and requires less memory than block
ciphers
4.
How Stream Ciphers Work1. Generate a pseudo-random keystream
2. XOR keystream with plaintext
3. Receiver uses the same keystream for
decryption
Mathematical Representation:
• Ciphertext = Plaintext ⊕ Keystream
5.
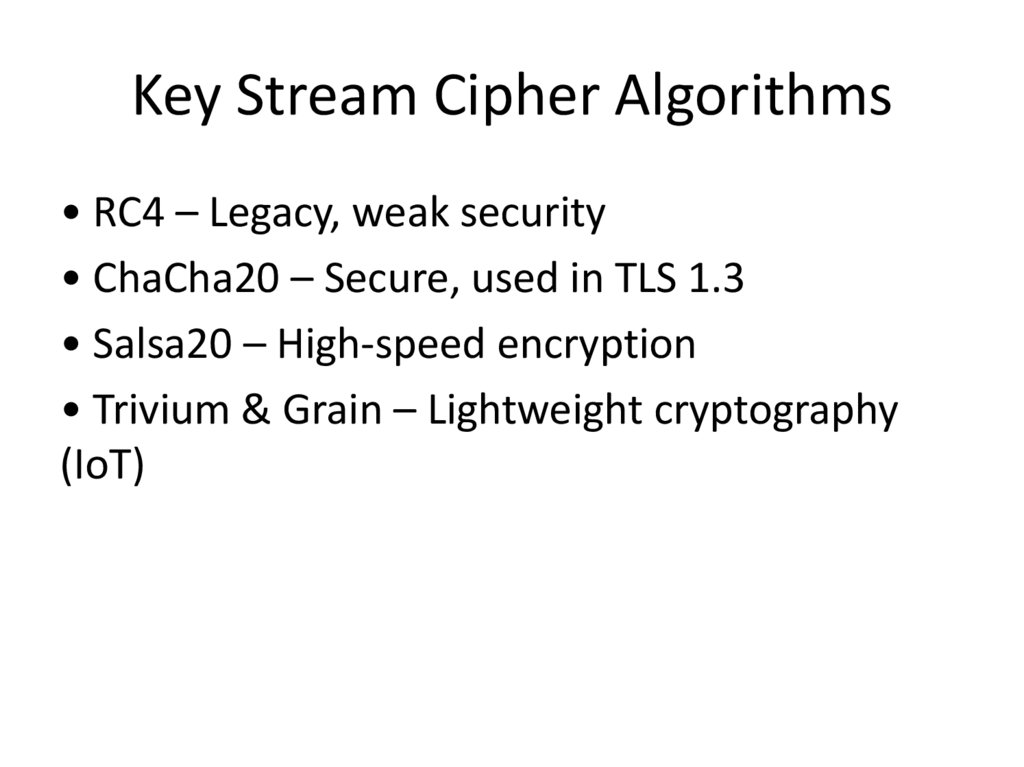
Key Stream Cipher Algorithms• RC4 – Legacy, weak security
• ChaCha20 – Secure, used in TLS 1.3
• Salsa20 – High-speed encryption
• Trivium & Grain – Lightweight cryptography
(IoT)
6.
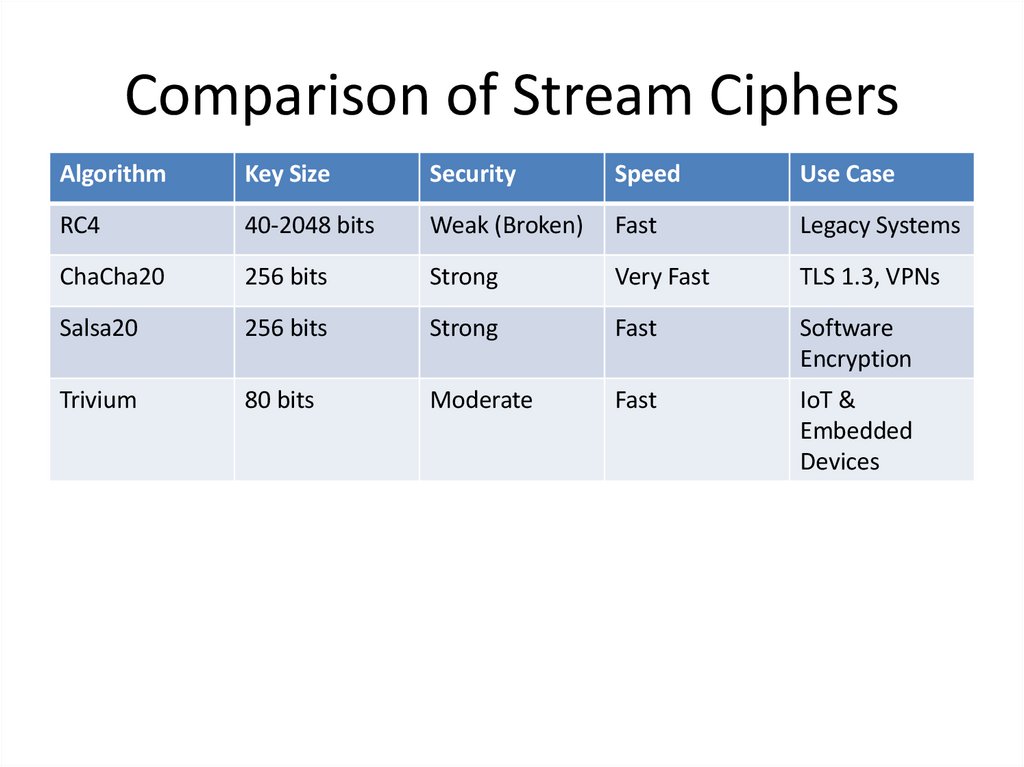
Comparison of Stream CiphersAlgorithm
Key Size
Security
Speed
Use Case
RC4
40-2048 bits
Weak (Broken)
Fast
Legacy Systems
ChaCha20
256 bits
Strong
Very Fast
TLS 1.3, VPNs
Salsa20
256 bits
Strong
Fast
Software
Encryption
Trivium
80 bits
Moderate
Fast
IoT &
Embedded
Devices
7.
RC4 Stream Cipher• A widely used but now insecure stream cipher.
It was implemented in WEP, SSL/TLS, and
other legacy protocols.
• RC4 suffers from keystream biases and
vulnerability to known attacks.
8.
ChaCha20 Stream Cipher• A modern, highly secure stream cipher used in
TLS 1.3, WireGuard VPN, and mobile
encryption.
• It provides strong security, high speed, and
resistance to known cryptographic attacks.
9.
Salsa20 Stream Cipher• An alternative to AES, known for its speed and
security.
• It is used in cryptographic applications
requiring high-performance encryption, such
as file encryption and secure messaging.
10.
Trivium & Grain Stream Cipher• Lightweight stream ciphers designed for
resource-constrained environments such as
IoT devices.
• They provide efficient encryption with
minimal power and memory usage.
11.
Attacks on Stream Ciphers• Key reuse (Two-time pad attack)
• RC4 bias attack
• State recovery attacks
• Mitigations:
✔ Use modern ciphers (ChaCha20)
✔ Never reuse keystreams
✔ Implement strong key management
12.
Real-World Applications✔ TLS 1.3 (Uses ChaCha20-Poly1305)
✔ WireGuard VPN (Fast encryption)
✔ Mobile & IoT (Lightweight cryptography)
✔ Secure Video & Voice Calls
13.
Conclusion• Stream ciphers encrypt data bit-by-bit
• ChaCha20 is the modern, secure standard
• RC4 is deprecated due to security flaws
• Keystream reuse is a major risk!







 informatics
informatics








