Similar presentations:
Presentation for cybersecurity executive training
1.
Navigate the maze of cyber threats with SecurityWorld
2.
Executive Training“Cybersecurity for NGOs ”
Aizada Kydyrbekova
Cybersecurity Expert
3.
AGENDA1. What is Cybersecurity
2. NGO Sector under Attack,
3. Why Cybersecurity Is Essential for SOS
4. Cybersecurity now a Leadership Responsibility.
5. 3-Day Executive Training Agenda
6. Practical Outcomes for National Management Team
7. Innovative Learning Approach – Introducing the Villains
8. Investment Proposal
4. 1. What is Cybersecurity
Cybersecurity is a complex approach focused onprotecting of Mission-Critical Digital Assets and Data
What We Must Protect
Confidential data
Sensitive information that must be protected: child records, donor details, employee
files
Valuable digital tools and systems:
Corporate websites, databases, apps.
Financial systems
Platforms and processes that manage donations, budgeting, payroll, and payments
Critical operations
The digital services that support program delivery, case management, crisis response,
and internal coordination
5.
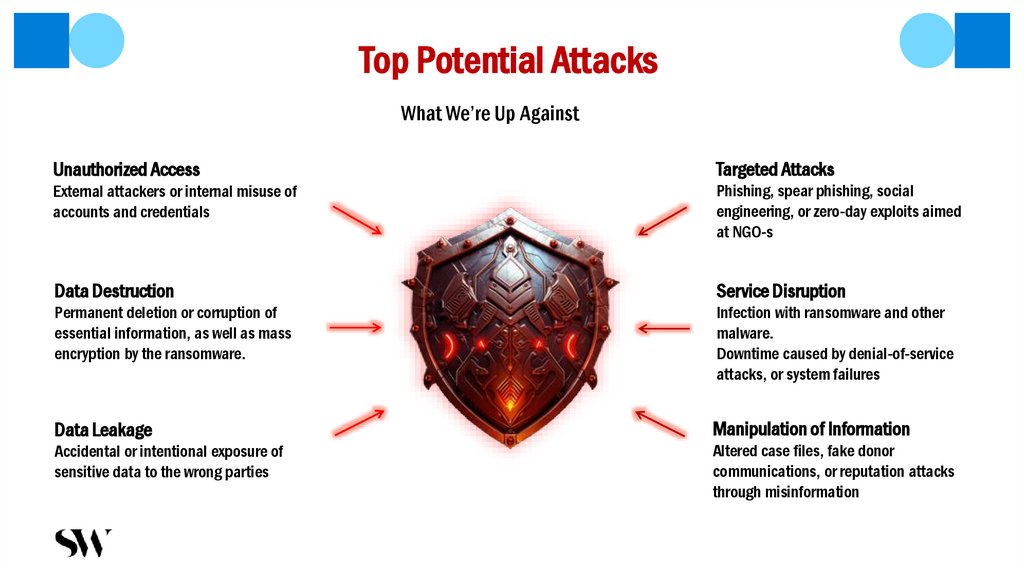
Top Potential AttacksWhat We’re Up Against
Unauthorized Access
Targeted Attacks
External attackers or internal misuse of
accounts and credentials
Phishing, spear phishing, social
engineering, or zero-day exploits aimed
at NGO-s
Data Destruction
Service Disruption
Permanent deletion or corruption of
essential information, as well as mass
encryption by the ransomware.
Infection with ransomware and other
malware.
Downtime caused by denial-of-service
attacks, or system failures
Data Leakage
Manipulation of Information
Accidental or intentional exposure of
sensitive data to the wrong parties
Altered case files, fake donor
communications, or reputation attacks
through misinformation
6.
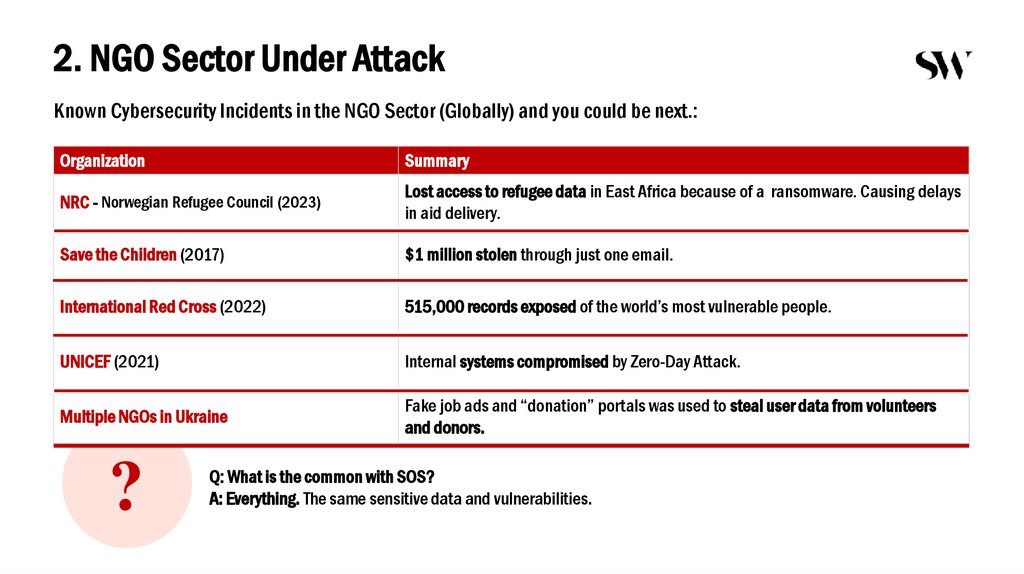
2. NGO Sector Under AttackKnown Cybersecurity Incidents in the NGO Sector (Globally) and you could be next.:
Organization
Summary
NRC - Norwegian Refugee Council (2023)
Lost access to refugee data in East Africa because of a ransomware. Causing delays
in aid delivery.
Save the Children (2017)
$1 million stolen through just one email.
International Red Cross (2022)
515,000 records exposed of the world’s most vulnerable people.
UNICEF (2021)
Internal systems compromised by Zero-Day Attack.
Multiple NGOs in Ukraine
Fake job ads and “donation” portals was used to steal user data from volunteers
and donors.
?
Q: What is the common with SOS?
A: Everything. The same sensitive data and vulnerabilities.
7. For last 35 years SOS Children’s Villages operates a complex, distributed digital environment across 130+ countries. Core
GlobalDigital
Footprint
For last 35 years SOS Children’s Villages operates a complex,
distributed digital environment across 130+ countries.
Core operations rely on the collection, exchange, and storage of
highly sensitive data.
8. What to protect
3. Why Cybersecurity Is Essential for SOSMission-Critical Digital Assets and Risks
What to protect
1.
Confidential Records: Safeguarding reports, legal files, medical data
2.
Mission-Critical Platforms: YouthLinks, YouthCan!, internal systems
3.
Donor Financial Data: Sponsorship info, payment systems, CRM
4.
PII: Children, families, employees, and volunteers
The Risks We Face
1.
Legal exposure (e.g., GDPR violations)
2.
Funding loss due to data breaches or downtime
3.
Reputational damage across national & global levels
4.
Confidential Data leakage
9. 4. Cybersecurity is now a leadership responsibility
Your organization is collecting, storing, andprocessing highly sensitive information.
You’re responsible for:
Budgets funded by governments & private donors
Continuity of processes under your legal entities
Not just for “what” your organization does,
but “how securely it does”.
You are legally accountable for:
• Entity’s operations
• Safety of your employees’ & donors’ personal data
• Complying with laws like GDPR, ISO 270001, etc.
10. High-Risk Attack Scenarios
Cybersecurity risk = New class of business risk1. A single phishing email leads to donor data leakage
→ Leads to: GDPR violation + donor withdrawal
2. A ransomware attack shuts down YouthLinks for a week
→ Leads to: Interrupted services + reputational harm
3. An IT staff member misconfigures data access
→ Leads to: internal policy breach + safeguarding failure
11. 5. 3-Day Executive Training Agenda
DAY 1DAY 2
DAY 3
Risk Awareness & Leaders Accountability
Cyber Incident Prevention & Response
Governance, ROI & Cyber-Resilience Culture
1. Cybersecurity & Mission Impact:
Why it matters for SOS Children’s Villages
1. Real-World NGO Breach Cases:
Lessons from humanitarian sector attacks
1. Cybersecurity as Investment:
Value for donor trust, continuity, and compliance
2. Understanding Threats:
Ransomware, phishing, insider threats
2. Crisis Simulation:
“What if it happened to us?” (headline role-play)
2. Budget Simulation Exercise:
“Spend €100,000 to protect what matters”
3. Cyber Risk = Business Risk:
Linking to donor trust, safeguarding, and service
continuity
3. Prevention vs. Preparedness:
Balancing investments, responsibilities & policies
3. Policy, People, and Culture:
Building executive accountability
4. Tactical Engagement:
+ Asset ownership
+ Contract & policy review
+ Legal/regulatory exposure
4. Threat Deep Dive:
+ Insider Threats & Malware in NGO operations.
+ Risk Map and mitigation strategy discussion.
4. SOS Strategy 2030 Alignment:
Digital trust, child protection, and organizational
resilience
5. Interactive Exercises:
+ Cyber Myth-Busting
+ Asset Identification & Risk Mapping
5. Threat Deep Dive:
+ Zero-Day Attacks
+ Ransomware Risks in SOS Platforms
+ Updated Risk Map with expert analysis
5. Final Leadership Task:
“ROI Elevator Pitch”: Each leader crafts their case for
cybersecurity to donors or boards
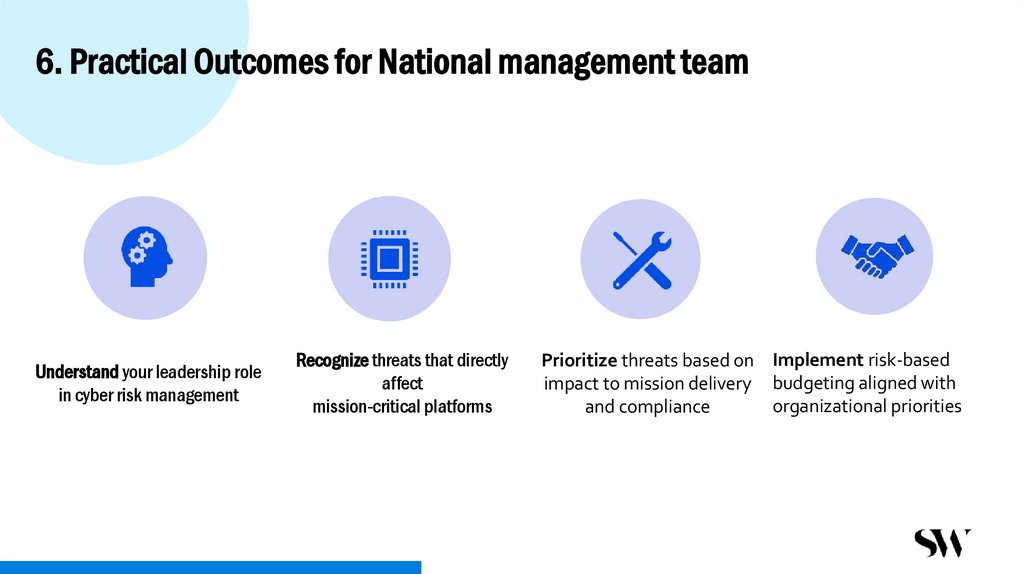
12. 6. Practical Outcomes for National management team
Understand your leadership rolein cyber risk management
Recognize threats that directly
affect
mission-critical platforms
Prioritize threats based on Implement risk-based
impact to mission delivery budgeting aligned with
organizational priorities
and compliance
13.
Transformation PromiseMost cybersecurity courses are designed for IT specialists,
this training is designed for LEADERS.
NOT boring theory
NOT technical terminology
→ exact attack scenarios against SOS.
→ simple metaphors with cyber-villains
NOT generic recommendations
NOT another one–time training
→ a personalized protection strategy.
→ structured road-map of building robust
cybersecurity step by step
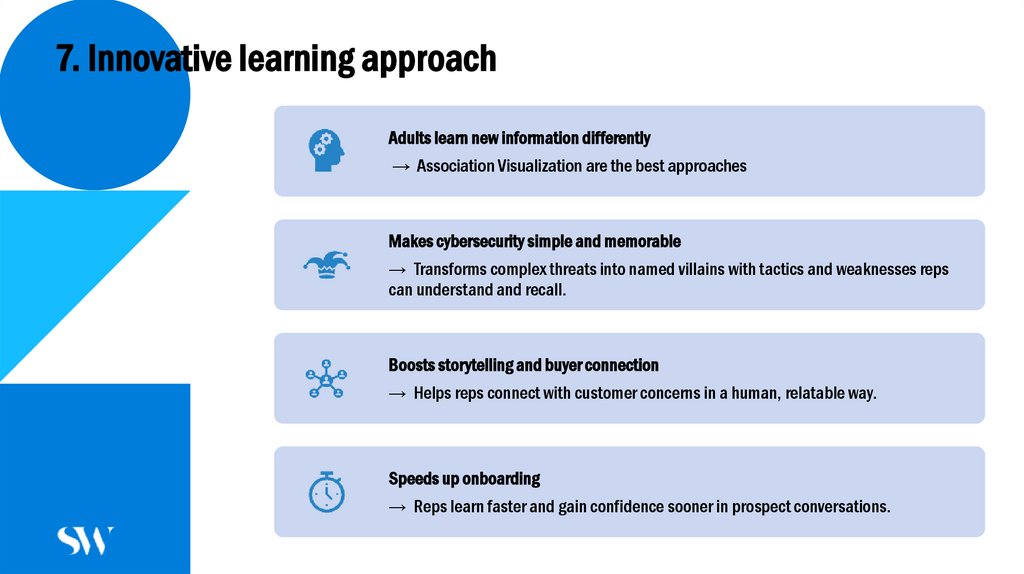
14. 7. Innovative learning approach
Adults learn new information differently→ Association Visualization are the best approaches
Makes cybersecurity simple and memorable
→ Transforms complex threats into named villains with tactics and weaknesses reps
can understand and recall.
Boosts storytelling and buyer connection
→ Helps reps connect with customer concerns in a human, relatable way.
Speeds up onboarding
→ Reps learn faster and gain confidence sooner in prospect conversations.
15. CYBERSECURITY VILLAINS
16.
CYBERSECURITY VILLAINSZERO-DAY GIRL
• Appearance: Nobody know, that she exists until she comes. Difficult to track
down and predict.
• Tactics: Exploits unknown vulnerabilities. Can bring damage and stay
hidden.
• Weaknesses: Regular software updates, deploy security patches, use
advanced threat detection systems.
• Impact: Zero-day exploits can lead to major breaches.
17.
CYBERSECURITY VILLAINSTHE PHISHER
• Appearance: constantly changing appearance to deceive victims.
• Tactics: Fake emails ,websites, to trick victims into revealing sensitive
information. Never uses brute force.
• Weaknesses: Employee trainings, implementing strong verification processes,
Multi-factor authentication, email filtering tools and behaviour analytics
• Impact: Data breaches and financial loss, starting point for more serious cyber
attacks.
18.
CYBERSECURITY VILLAINSDATA THIEF
• Appearance: shadowy figure, always cloaked in digital camouflage. His
cape with symbols of keys and lockpicks, representing his skill in
bypassing security measures.
• Tactics: he specializes in infiltrating networks undetected and finding and
exploiting weak points in software and systems to gain unauthorized
access, Social Engineering and Data Exfiltration.
• Weaknesses: strong encryption and multi-factor authentication,
monitoring network activity and and Anomaly Detection
• Impact: Data Breaches, Intellectual Property Theft can cause a company's
competitive edge, privacy violations and loss of customers’ trust
19.
The Training ResultsIdentify where your critical digital assets are, and what
could go wrong
Learn which digital risks exist today—and which are most
relevant and dangerous in your own country
Understand what actions you must take to manage,
reduce, or mitigate those risks