Similar presentations:
Corporate Cybersecurity Final Project
1.
CYBERSECURITYANALYSIS OF
Meta
PLATFORMS,
INC.
Presented by:
Group SIS-2128
Tugalev Artem, Rodionov Radislav, Lev Tsoy,
Yerkimbekov Insar
2.
EXECUTIVEOVERVIEW
Purpose of the Project
The purpose of this project is to evaluate and enhance Meta
Platforms, Inc.'s cybersecurity posture by identifying
vulnerabilities, addressing unique challenges, and proposing
advanced solutions. This ensures data protection, regulatory
compliance, and resilience across Meta's platforms—Facebook,
Instagram, and WhatsApp.
Corporate Context
Meta Platforms, Inc., based in Menlo
Park, California, is a global leader in
technology and social media, with
over 3 billion monthly active users.
Its platforms connect people
worldwide, and its advancements in
virtual reality and artificial
intelligence solidify its position as a
tech industry pioneer.
Key Characteristics:
• Industry: Social media, virtual reality,
and digital advertising.
• Size: Market capitalization exceeding
$500 billion; employs over 70,000 staff
globally.
• Unique Cybersecurity Challenges:
⚬ Protection of vast amounts of user
data.
⚬ Preventing misinformation and
fake account propagation.
⚬ Mitigating sophisticated
cyberattacks from global
adversaries.
⚬ Securing emerging technologies
such as AI content moderation and
metaverse platforms.
3.
ANALYSIS OFCURRENT
CYBERSECURITY
POSTURE
Threat Landscape
External Threats
• Phishing: Meta faces large-scale phishing attacks
targeting its users and employees, often seeking
to gain unauthorized access to accounts.
• Ransomware: Although not directly impacting
user data, supply chain vulnerabilities may expose
third-party vendors to ransomware.
• Advanced Persistent Threats (APTs): Statesponsored actors frequently target Meta's
platforms to extract sensitive information or
spread disinformation.
• Distributed Denial of Service (DDoS): Attackers
aim to disrupt services and degrade platform
availability.
Internal Risks
• Insider Threats: Disgruntled
employees or contractors could
misuse access privileges.
• Shadow IT: Unapproved tools and
applications in use by employees
may create unforeseen
vulnerabilities.
• Lack of Awareness: Human error
due to inadequate cybersecurity
training contributes to
vulnerabilities.
4.
SECURITYEVALUATION AND
Innovation
Security Infrastructure Evaluation
Tools overview:
• Firewalls: Monitor and block unauthorized traffic.
• Endpoint Security: Advanced malware protection for devices.
• SIEM Tools: Real-time monitoring and threat detection.
• Encryption: Secures data in transit and at rest.
• Access Management: Enforces MFA and role-based controls.
Compliance and
Governance
• Alignment with Regulations: Adheres to
GDPR, ISO 27001, and SOX requirements.
• Policy Enforcement: Robust data retention,
access control, and incident response policies
in place, ensuring regulatory compliance.
Innovation
• AI Integration: Utilizes AI for proactive threat detection and analysis.
• Automation: Streamlined incident response through automation.
• Zero Trust: Incorporates Zero Trust principles for enhanced access
security.
• Evolving Threats: Adaptive measures to counter ransomware and
advanced persistent threats (APTs).
5.
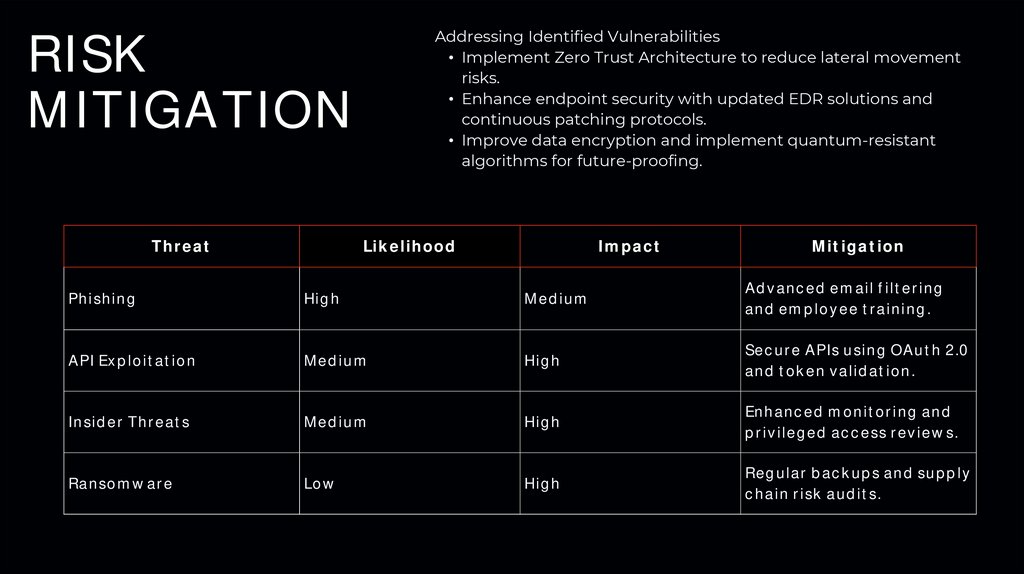
RISKMITIGATION
Threat
Addressing Identified Vulnerabilities
• Implement Zero Trust Architecture to reduce lateral movement
risks.
• Enhance endpoint security with updated EDR solutions and
continuous patching protocols.
• Improve data encryption and implement quantum-resistant
algorithms for future-proofing.
Likelihood
Impact
Mitigation
Phishing
High
Medium
Advanced email filtering
and employee training.
API Exploitation
Medium
High
Secure APIs using OAuth 2.0
and token validation.
Insider Threats
Medium
High
Enhanced monitoring and
privileged access reviews.
Ransomware
Low
High
Regular backups and supply
chain risk audits.
6.
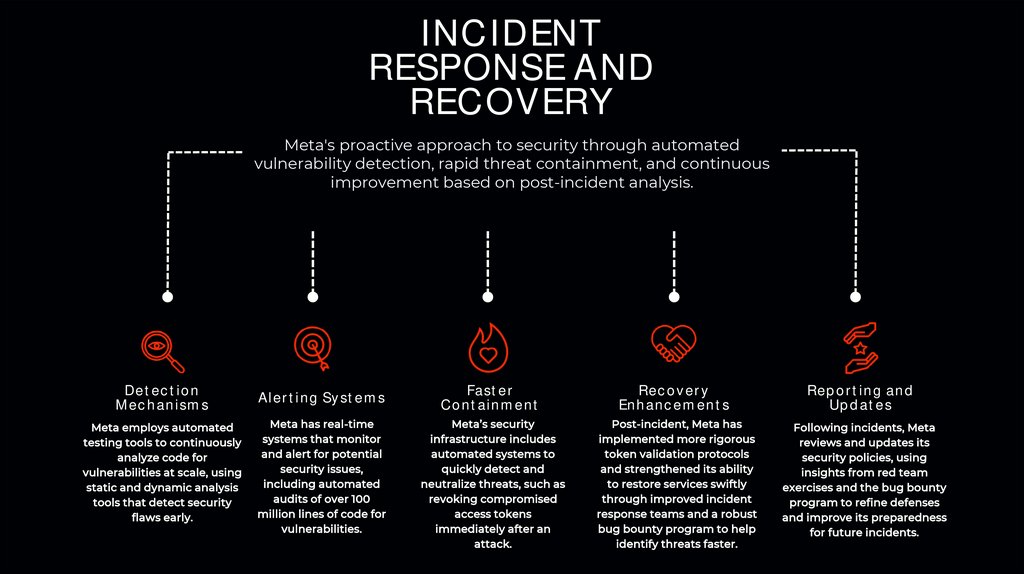
INCIDENTRESPONSE AND
RECOVERY
Meta's proactive approach to security through automated
vulnerability detection, rapid threat containment, and continuous
improvement based on post-incident analysis.
Detection
Mechanisms
Alerting Systems
Meta employs automated
testing tools to continuously
analyze code for
vulnerabilities at scale, using
static and dynamic analysis
tools that detect security
flaws early.
Meta has real-time
systems that monitor
and alert for potential
security issues,
including automated
audits of over 100
million lines of code for
vulnerabilities.
Faster
Containment
Recovery
Enhancements
Reporting and
Updates
Meta’s security
infrastructure includes
automated systems to
quickly detect and
neutralize threats, such as
revoking compromised
access tokens
immediately after an
attack.
Post-incident, Meta has
implemented more rigorous
token validation protocols
and strengthened its ability
to restore services swiftly
through improved incident
response teams and a robust
bug bounty program to help
identify threats faster.
Following incidents, Meta
reviews and updates its
security policies, using
insights from red team
exercises and the bug bounty
program to refine defenses
and improve its preparedness
for future incidents.
7.
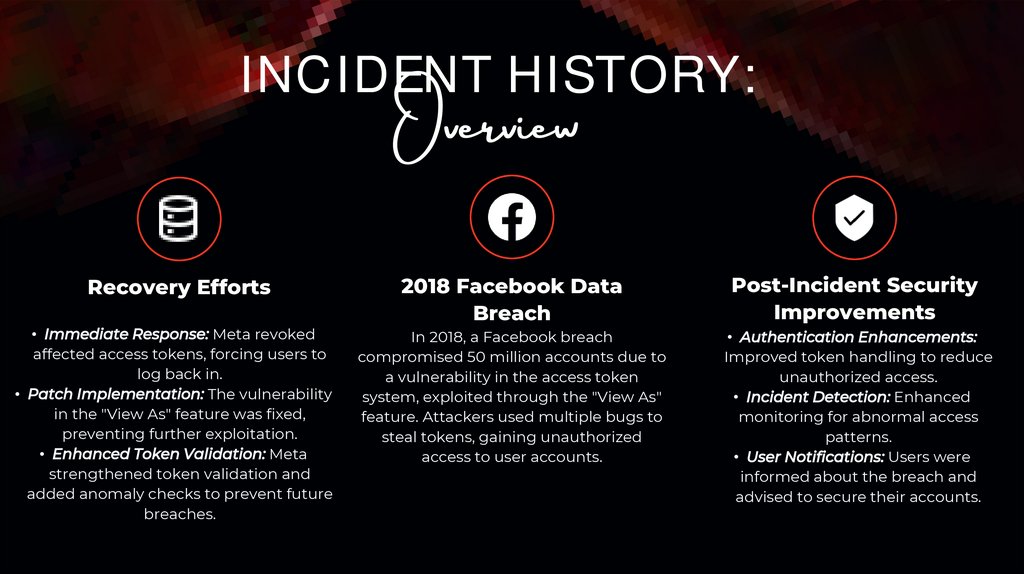
INCIDENT HISTORY:Overview
Recovery Efforts
• Immediate Response: Meta revoked
affected access tokens, forcing users to
log back in.
• Patch Implementation: The vulnerability
in the "View As" feature was fixed,
preventing further exploitation.
• Enhanced Token Validation: Meta
strengthened token validation and
added anomaly checks to prevent future
breaches.
2018 Facebook Data
Breach
Post-Incident Security
Improvements
In 2018, a Facebook breach
compromised 50 million accounts due to
a vulnerability in the access token
system, exploited through the "View As"
feature. Attackers used multiple bugs to
steal tokens, gaining unauthorized
access to user accounts.
• Authentication Enhancements:
Improved token handling to reduce
unauthorized access.
• Incident Detection: Enhanced
monitoring for abnormal access
patterns.
• User Notifications: Users were
informed about the breach and
advised to secure their accounts.
8.
COMPLIANCEALIGNMENT
Demonstration Meta's commitment to adhering to global compliance
requirements
GDPR (General Data
Protection Regulation)
NIST (National Institute of
Standards and
Technology)
ISO 27001 (International
Organization for
Standardization)
Ongoing Audits and
Updates
Meta improves data
handling practices,
strengthens breach
notification processes, and
ensures data protection by
design and default, reducing
risks of unauthorized access
and ensuring timely breach
responses in compliance
with GDPR obligations.
Meta implements NIST’s
cybersecurity frameworks,
particularly the NIST
Cybersecurity Framework
(CSF), to identify, assess, and
mitigate cybersecurity risks,
following best practices in
cybersecurity management.
Meta’s practices align with
ISO 27001, a leading
international standard for
information security
management, establishing
an Information Security
Management System (ISMS)
that is regularly monitored
and improved.
Meta conducts internal and
third-party audits to verify
compliance with GDPR, NIST,
and ISO 27001 standards, while
the security framework is
continuously updated to
respond to emerging threats,
new regulations, and audit
findings.
9.
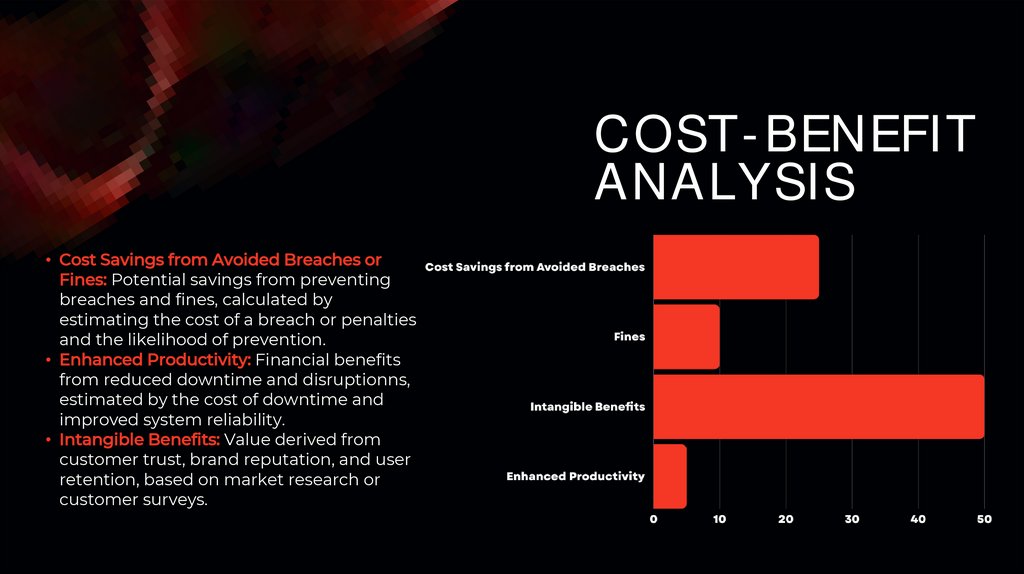
COST-BENEFITANALYSIS
• Cost Savings from Avoided Breaches or
Fines: Potential savings from preventing
breaches and fines, calculated by
estimating the cost of a breach or penalties
and the likelihood of prevention.
• Enhanced Productivity: Financial benefits
from reduced downtime and disruptionns,
estimated by the cost of downtime and
improved system reliability.
• Intangible Benefits: Value derived from
customer trust, brand reputation, and user
retention, based on market research or
customer surveys.
10.
STAKEHOLDERENGAGEMENT
IT Teams for Technical Feasibility
• Collaboration with IT Security Teams:
⚬ IT teams provide technical input to assess the
feasibility of proposed security tools and systems,
ensuring they integrate seamlessly with existing
infrastructure.
⚬ Feedback on the scalability of solutions and how they
can be adapted as Meta grows.
• Pilot Testing:
⚬ Early-stage testing and validation of tools such as EDR
solutions, SIEM platforms, and encryption protocols to
ensure they meet the company’s security
requirements.
⚬ Regular meetings to discuss performance, potential
issues, and necessary adjustments.
• Implementation Support:
⚬ IT teams play a key role in deploying and configuring
security tools, ensuring the smooth integration of new
technologies without disrupting ongoing operations.
11.
• Compatibility with AI-Driven Analytics: Theinfrastructure supports integration with AIpowered threat detection and predictive
analytics, enhancing the ability to identify and
mitigate risks in real-time.
• Preparedness for Quantum Computing
Threats: The project incorporates research and
alignment with emerging post-quantum
cryptographic standards to protect against
future quantum-based vulnerabilities.
• Integration with New Security Tools or
Standards: Designed with flexibility in mind,
the project allows for seamless adoption of
cutting-edge security technologies and
adherence to updated regulatory frameworks
as they arise.
SCALABILITY
AND FUTUREPROOFING
The project is designed to support Meta’s growth and
evolving technological landscape, ensuring long-term
security and operational efficiency.
12.
TRAININGAND
AWARENESS
Employee involvement is pivotal in maintaining a secure organizational
environment. A well-informed workforce acts as the first line of defense
against cyber threats.
Training Programs:
Practical Exercises:
Regularly scheduled cybersecurity
training sessions equip employees with
the knowledge to identify and respond
to threats such as phishing attempts,
social engineering, and malware
attacks. These programs cover best
practices for secure data handling,
password management, and
recognizing suspicious activity.
Conducting periodic phishing simulations
and hands-on security drills ensures
employees stay vigilant and capable of
handling real-world scenarios. These
exercises provide measurable insights into
employee readiness and highlight areas for
improvement.
13.
CONCLUSIONMeta’s cybersecurity efforts bolster defenses
against evolving threats, ensuring
compliance, scalability, and operational
efficiency. By integrating AI-driven analytics,
robust security frameworks, and adaptive
response systems, Meta safeguards user data
and maintains reliability. Regular audits,
employee training, and innovations like Zero
Trust prepare the company for future
challenges, fostering customer trust and
strengthening its reputation.
14.
THANK YOUFOR YOUR
ATTENTION!










 internet
internet








