Similar presentations:
Information Security Risk
1.
Information Security RiskManagement
INF 203 Information security
Week 13
2.
Content:• Introduction to risk management
• Risk management steps
• Vulnerability assessment
• Risk assessment
• Risk treatment
• Risk monitoring
• Compliance
3.
Introduction to risk managementInformation security risk management, or ISRM, is the
process of managing risks associated with the use of
information technology.
It involves identifying, assessing, and treating risks to the confidentiality, integrity,
and availability of an organization’s assets. The end goal of this process is to treat
risks in accordance with an organization’s overall risk tolerance. Businesses
shouldn’t expect to eliminate all risks; rather, they should seek to identify and
achieve an acceptable risk level for their organization.
4.
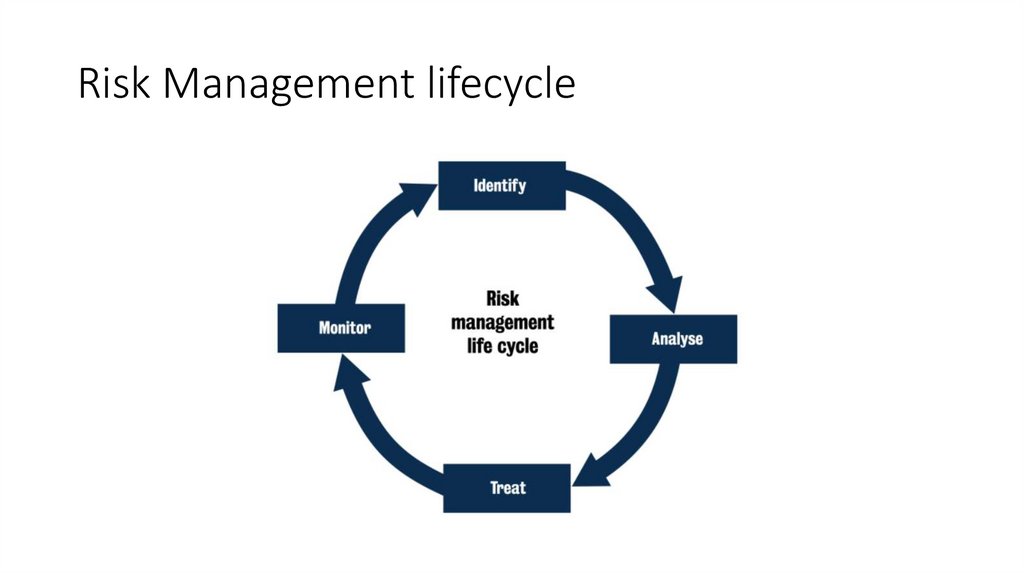
Risk Management lifecycle5.
Risk Management Steps• Asset Identification (and their value)
• Threat Assessment
• Vulnerability Assessment
• Risk Assessment
• Risk Treatment
• Risk Monitoring
6.
Asset IdentificationAll organisational assets and systems that are necessary for the delivery of effective
operations or are of specific organisational value (e.g., commercially sensitive information),
should be identified. These may be: physical items, data stored or transmitted in any
format (e.g. hard or electronic copy), personnel with specific knowledge/skills, or crowded
places requiring protection. Engaging a suitable organisation-wide stakeholder group to
conduct this exercise and provide ongoing support to the risk assessment/management
process, will provide the greatest benefits.
Organisations should consider what, if stolen, damaged, divulged or has its
confidentiality, integrity and/or availability compromised in any other way, may cause:
• Reputational damage
• Financial damage
• Injury or loss of life to you, a stakeholder or partner, or the wider public
• Assist in furthering the aims of a malicious / hostile entity.
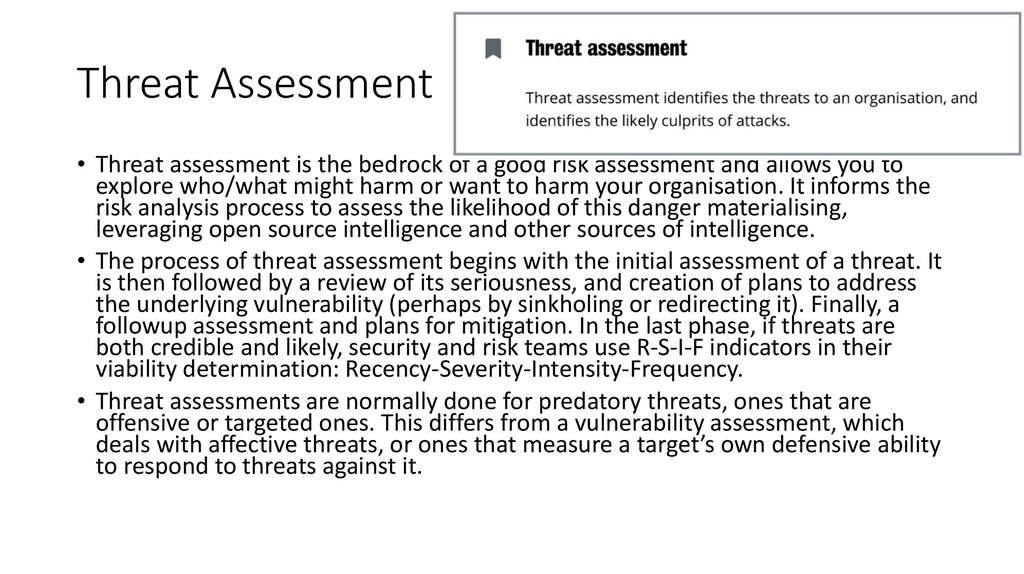
7.
Threat Assessment• Threat assessment is the bedrock of a good risk assessment and allows you to
explore who/what might harm or want to harm your organisation. It informs the
risk analysis process to assess the likelihood of this danger materialising,
leveraging open source intelligence and other sources of intelligence.
• The process of threat assessment begins with the initial assessment of a threat. It
is then followed by a review of its seriousness, and creation of plans to address
the underlying vulnerability (perhaps by sinkholing or redirecting it). Finally, a
followup assessment and plans for mitigation. In the last phase, if threats are
both credible and likely, security and risk teams use R-S-I-F indicators in their
viability determination: Recency-Severity-Intensity-Frequency.
• Threat assessments are normally done for predatory threats, ones that are
offensive or targeted ones. This differs from a vulnerability assessment, which
deals with affective threats, or ones that measure a target’s own defensive ability
to respond to threats against it.
8.
Vulnerability Assessment• Vulnerabilities are those things that can be exploited in order to breach security
properties.
• Vulnerabilities may be in:
1. Technology
2. Processes
3. People
* Vulnerabilities need to be known to be exploitable
9.
Technical Vulnerabilities• Vulnerabilities listed in various places
1. NIST National Vulnerability Database (https://nvd.nist.gov/)
2. Open Source Vulnerability Database
3. US-CERT Vulnerability database
4. UK-CERT / NCSC CiSP (https://www.ncsc.gov.uk/cisp)
• Most vulnerabilities specified as a Common Vulnerability and Exposures format
(CVE)
1. http://cve.mitre.org/
2. Common Vulnerability Scoring System - https://www.first.org/cvss/
10.
Application Vulnerabilities• This is where hackers are going
• Applications are the most vulnerable
• Web and Mobile applications are the most fertile ground
• Applications get poorly patched
11.
Social Engineering• Vulnerabilities exist in people and processes
• Helpdesks are there to assist people
• People don’t really care about what happens to their corporate information
• Social Engineering Toolkit
12.
Qualitative Risk Assessment• Discourse analysis useful
• Language dependent on the
environment and context
• Language used can be
enlightening
• Discourse and data analysis used
in other disciplines
13.
Qualitative Risk Assessment14.
Qualitative Risk Assessment• Qualitative probabilities (likelihoods)
• Qualitative/Quantitative Impact
• Risk = Threat x Vulnerability x Impact
Likelihood
15.
OWASP Risk Rating Methodology16.
Quantitative Risk Assessment17.
Quantitative Risk Assessment18.
Annual Rate of Occurrence19.
Single loss Expectancy20.
Risk Treatment• Considering the impact and frequency dimensions of risks, we can
sort the usual treatment decisions into four categories:
21.
Risk monitoringThe final stage of risk management, after risk treatment, is risk monitoring.
This is where we monitor the results of the risk treatment plan.
The frequency of monitoring may vary according to the type of threat:
• some threats may change very quickly and will require monitoring at
frequent intervals
• others, however, will change little over long periods of time and will
only need occasional monitoring.
The whole risk management cycle should be repeated over time, as some
threats might disappear completely and new threats might emerge. The
interval will depend largely upon the risk appetite of the organisation and
may well be documented in a risk management strategy or policy document.
22.
ComplianceWhether something is working in accordance with
defined policies, processes and procedures.
Checking
compliance
This could:
cover a major operation such as a whole organisation being compliant
with a recognised international standard for Information Security like
ISO27000-series
be much more limited with just certain aspects of the operation, or
individual users of a specific system, being assessed for compliance.
It also includes evaluating whether an organisation is meeting
the requirements of local laws and regulation (recall the
section on externally imposed requirements from the previous
lesson).
23.
How do we check compliance?Risk management
Documentation of results and
evidence of threat,
vulnerability, impact, and risk
assessments.
Creation of a risk register to
highlight identified risks (so
that the organisation is aware
of the risks and has an outline
of how they will be managed).
Security policies and control
Maintenance of an up-to-date set of security
policies and controls with a review process,
including review of whether all security policies are
compliant with existing laws.
A register of ‘exempts’ from security policies: what
is not covered by policy and a good justification of
why it is not (eg perhaps a personal computer that
does not connect to the network is not covered).
Reports of breaches/incidents
As well as:
plans to address these breaches
evidence of what has gone wrong and what corrective actions are needed.
23
24.
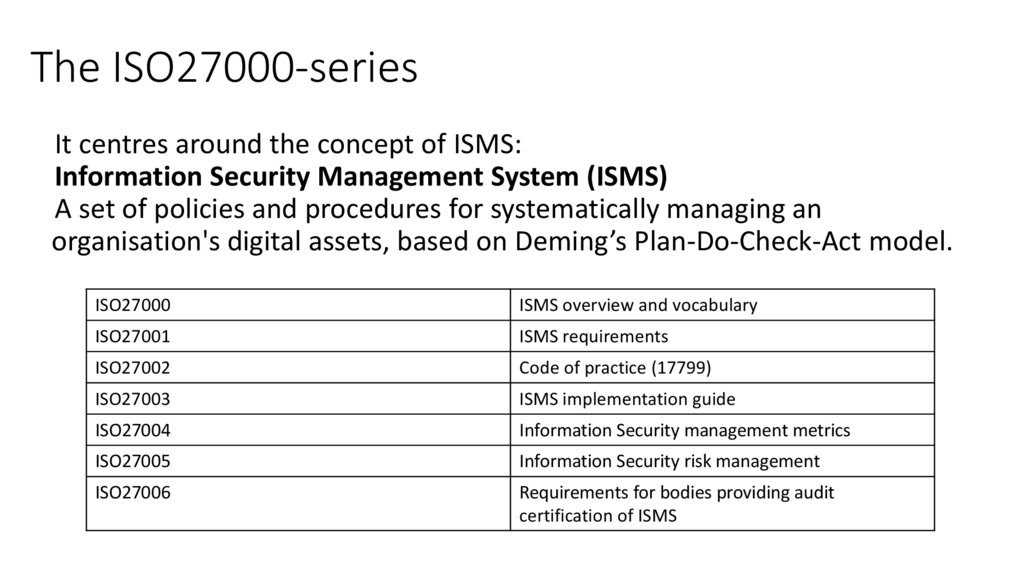
The ISO27000seriesThe ISO/IEC 27000 standard series (which you may
also see referred to as the ISO27K series) provides a
family of standards for implementing Information
Security management, including risk management and
security control implementation.
The series provides organisations with some
guidance regarding compliance legal requirements
and covers the following areas:
❑intellectual property rights
❑protection of organisational records
❑data protection and privacy of personal information
❑prevention of misuse of information processing
facilities
❑regulation of cryptographic controls.
24
25.
The ISO27000-seriesIt centres around the concept of ISMS:
Information Security Management System (ISMS)
A set of policies and procedures for systematically managing an
organisation's digital assets, based on Deming’s Plan-Do-Check-Act model.
ISO27000
ISMS overview and vocabulary
ISO27001
ISMS requirements
ISO27002
Code of practice (17799)
ISO27003
ISMS implementation guide
ISO27004
Information Security management metrics
ISO27005
Information Security risk management
ISO27006
Requirements for bodies providing audit
certification of ISMS
26.
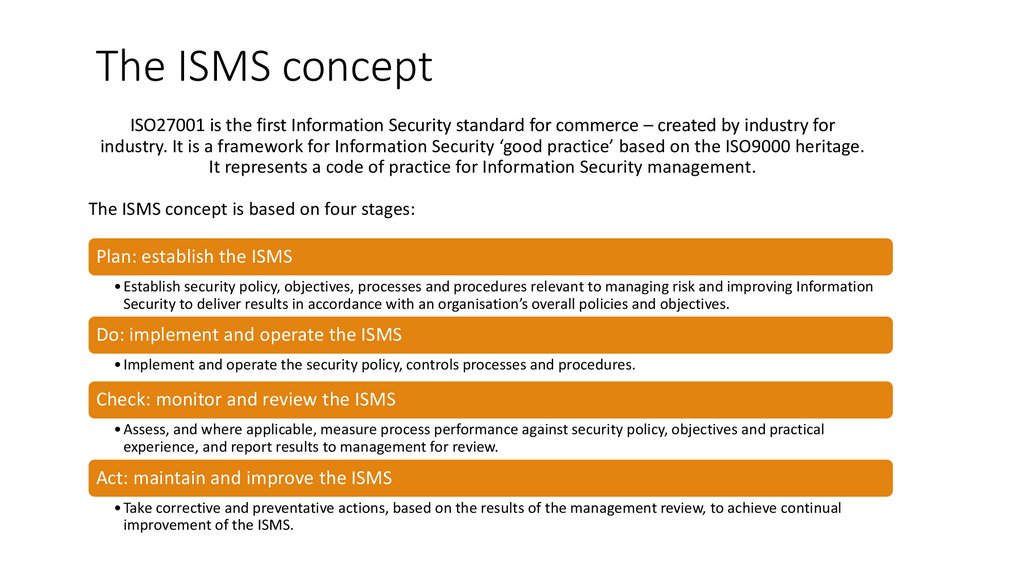
The ISMS conceptISO27001 is the first Information Security standard for commerce – created by industry for
industry. It is a framework for Information Security ‘good practice’ based on the ISO9000 heritage.
It represents a code of practice for Information Security management.
The ISMS concept is based on four stages:
Plan: establish the ISMS
• Establish security policy, objectives, processes and procedures relevant to managing risk and improving Information
Security to deliver results in accordance with an organisation’s overall policies and objectives.
Do: implement and operate the ISMS
• Implement and operate the security policy, controls processes and procedures.
Check: monitor and review the ISMS
• Assess, and where applicable, measure process performance against security policy, objectives and practical
experience, and report results to management for review.
Act: maintain and improve the ISMS
• Take corrective and preventative actions, based on the results of the management review, to achieve continual
improvement of the ISMS.
27.
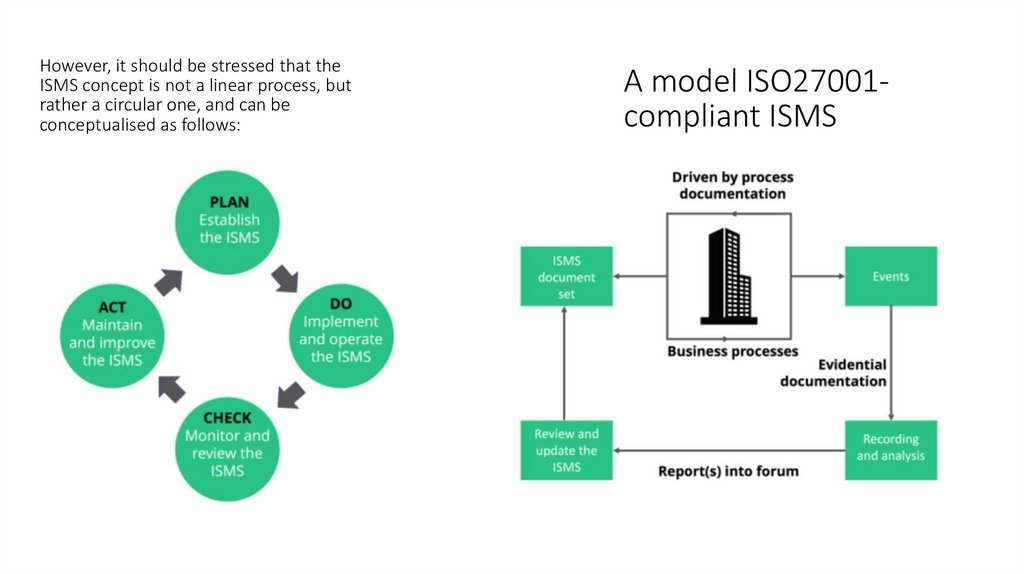
However, it should be stressed that theISMS concept is not a linear process, but
rather a circular one, and can be
conceptualised as follows:
A model ISO27001compliant ISMS
28.
The ISMS document set and the events referred to in the above graphic are explained in more detailbelow:
ISMS document set
Events
organisation security policy
risk management documents
statement of applicability
asset registers
policies, procedures and
standards applicable to scope
● SLAs, contracts and other
evidence.
security incidents
suspected weaknesses
malfunctions.
audit observations
testing findings
spot check findings.
29.
ISO27005 (risk management)ISO27005, published in 2008, provides guidance on implementing a
risk management system to specifically support the creation and
maintenance of ISO27001’s ISMS.
Implementing ISO/IEC 27005 helps organizations proactively manage
information security risks, ensuring the confidentiality, integrity, and
availability of sensitive information assets.
30.
Information Security Risk ManagementProcess:
ISO/IEC 27005 provides guidance on the following aspects of risk management:
1.Risk Assessment: It outlines methodologies for identifying and assessing information security risks within the
context of the organization's overall risk management process.
2.Risk Evaluation: The standard helps in evaluating the identified risks by considering the potential consequences
and the likelihood of occurrence. This evaluation aids in prioritizing risks for further treatment.
3.Risk Treatment: ISO/IEC 27005 provides guidelines on selecting appropriate risk treatment options, which can
include risk mitigation, risk transfer, risk acceptance, or a combination of these strategies.
4.Risk Monitoring and Review: The standard offers guidance on monitoring and reviewing the risk management
process, ensuring that it remains effective over time and adapting to changes in the organization's context and risk
landscape.
5.Integration with ISO/IEC 27001: ISO/IEC 27005 aligns with the general concepts specified in ISO/IEC 27001, the
standard for information security management systems. It helps organizations integrate risk management seamlessly
into their overall information security management processes.
31.
Benefits of Implementing ISO/IEC 27005:1.Structured Approach: ISO/IEC 27005 provides a structured approach to information
security risk management, ensuring that risks are identified, assessed, and managed
systematically.
2.Compliance: By following the guidelines in ISO/IEC 27005, organizations can
demonstrate compliance with internationally recognized best practices in information
security risk management.
3.Informed Decision-Making: Effective risk management enables informed decisionmaking regarding the allocation of resources for security measures, helping
organizations prioritize actions based on the most significant risks.
4.Continuous Improvement: The risk management process, as outlined in ISO/IEC
27005, supports continuous improvement by providing a mechanism to monitor, assess,
and adapt to changing risk scenarios and organizational contexts.
5.Enhanced Security Posture: By identifying and addressing vulnerabilities and threats,
organizations can enhance their overall security posture and better protect their
information assets.
32.
More oncompliance
Implementing the ISO/IEC 27000 series of standards, which encompasses various standards
related to information security management systems (ISMS), offers several significant benefits to
organizations. Here are some key advantages:
1. Global Recognition and Credibility:
• Internationally Recognized Standards: ISO/IEC 27000 series standards are globally
recognized and accepted, enhancing the credibility of organizations adhering to these
standards.
2. Improved Information Security:
•Comprehensive Framework: The series provides a comprehensive framework for
establishing, implementing, maintaining, and continually improving information security
management systems, leading to enhanced security practices.
•Risk Management: Standards like ISO/IEC 27001 and 27005 help organizations
effectively identify, assess, and manage information security risks, ensuring a proactive
approach to security.
3. Regulatory Compliance:
•Alignment with Regulations: Adhering to ISO/IEC 27000 series standards helps
organizations align with various legal, regulatory, and contractual requirements related to
information security.
4. Enhanced Business Resilience:
•Business Continuity: The standards emphasize business continuity planning, ensuring
that organizations are prepared to respond to and recover from information security
incidents, maintaining operations during and after disruptions.
5. Customer and Stakeholder Trust:
•Increased Trust: Adherence to international security standards fosters trust among
customers, partners, and stakeholders, demonstrating a commitment to safeguarding
sensitive information.
33.
6. Efficient Resource Utilization:•Optimized Resource Allocation: By following standardized approaches to security management, organizations can optimize
resource allocation and investment in information security measures.
7. Vendor and Partner Relationships:
•Vendor Assurance: Organizations can assure their vendors and partners of their commitment to information security, facilitating
secure collaborations and reducing supply chain risks.
8. Incident Response and Management:
•Effective Incident Response: Standards such as ISO/IEC 27035 provide guidelines for incident response management, ensuring
organizations can effectively respond to and recover from security incidents.
9. Continuous Improvement:
•Performance Monitoring: The series emphasizes the importance of performance monitoring, enabling organizations to measure
the effectiveness of their information security management systems and make continuous improvements.
10. Cost Savings:
•Reduced Security Incidents: Implementing robust security controls and risk management practices can lead to a reduction in
security incidents, thereby potentially saving costs associated with data breaches and remediation efforts.
11. Competitive Advantage:
•Market Differentiation: Certification to ISO/IEC 27001 can serve as a competitive differentiator, especially in industries where
information security is a critical concern for customers.
12. Employee Awareness and Engagement:
•Increased Awareness: Following standardized security practices raises awareness among employees, encouraging a securityconscious culture within the organization.
13. Long-Term Sustainability:
•Sustainability: The systematic approach to security management ensures that information security measures are sustained over
the long term, adapting to evolving threats and technologies.
In summary, implementing the ISO/IEC 27000 series not only strengthens an organization’s security posture but also contributes to
its overall resilience, trustworthiness, and competitiveness in the market.
























 software
software








