Similar presentations:
Hacking Lab
1.
Hacking LabDr Bishwajeet Pandey, SMIEEE
Professor-Department of Intelligent System and Cyber
Security, Astana IT University, Kazakhstan
PhD (Gran Sasso Science Institute, L'Aquila, Italy)
Visiting Professor at
L.N. Gumilyov Eurasian National University, Kazakhstan
UCSI UNIVERSITY-Malaysia
2.
ABOUT COURSE TEACHERPhD from Gran Sasso Science Institute, Italy
PhD Supervisor Prof Paolo Prinetto from Politecnico Di Torino
MTech from Indian Institute of Information Technology, Gwalior, India
Visited 47 Countries Across The Globe
Written 200+ Research paper with 212 Researcher from 93 Universities
Scopus Profile: https://www.scopus.com/authid/detail.uri?authorId=57203239026
Google Scholar: https://scholar.google.com/citations?user=UZ_8yAMAAAAJ&hl=hi
IBM Certified Solution Designer
EC-Council Certified Ethical Hacker
AWS Certified Cloud Practitioner
Email: bishwajeet.pandey@gssi.it, dr.pandey@ieee.org, bk.pandey@astanait.edu.kz
3.
Syllabus of Ethical Hacking• THEORY
• Week 1-2: Introduction to Ethical Hacking
• Week 3-4: Scanning and Enumeration
• Week 5-6: Sniffing and Social Engineering
• Week 7-8: DOS and Session hijacking
• Week 9-10: Webserver and Applications
• Lab Experiments 1-16 Based on All ABOVE UNIT
4.
My Certification5.
6.
My Research Publication7.
8.
9.
10.
11.
My Research Areas12.
CYBER RANGE AND CYBERSECURITY OF CYBER PHYSICAL
SYSTEM
13.
Ethical Hacking CONCEPTS• What
is
Ethical
Hacking?
• Ethical hacking is the process where a professional hacker
legally and deliberately tries to break into the computers
and devices of an organisation. In doing so, ethical
hackers can test the organisation's defences,
highlighting any vulnerabilities in their systems and
networks.
14.
Ethical Hacking CONCEPTS• What are the 5 steps of ethical hacking?
Five Phases of Ethical Hacking
● Phase 1: Reconnaissance.
● Phase 2: Scanning.
● Phase 3: Gaining Access.
● Phase 4: Maintaining Access.
● Phase 5: Clearing Tracks
15.
Ethical Hacking CONCEPTS: Types of HackerHackers can be classified into different categories such as white hat, black
hat, and grey hat, based on their intent of hacking a system.
White Hat hackers are also known as Ethical Hackers. They never intent to
harm a system, rather they try to find out weaknesses in a computer or a
network system as a part of penetration testing and vulnerability assessments.
Black Hat hackers, also known as crackers, are those who hack in order to
gain unauthorized access to a system and harm its operations or steal
sensitive
information.
Grey hat hackers are a blend of both black hat and white hat hackers. They
act without malicious intent but for their fun, they exploit a security weakness
in a computer system or network without the owner’s permission or
knowledge.
16.
Ethical Hacking CONCEPTS• What
is
reconnaissance
in
hacking?
• In the context of cybersecurity, reconnaissance is the
practice of covertly discovering and collecting
information about a system. This method is often used
in ethical hacking or penetration testing.
17.
Ethical Hacking CONCEPTS• What is hacker full form?
• Full form of HACKER is "Hardcore Programmer"
18.
Ethical Hacking CONCEPTS• Who was the first hacker?
• The first major hacking came in 1971, by a vietnam vet
named John Draper. He figured out a way to make free
phone calls. This was later called "Phreaking".
19.
Ethical Hacking CONCEPTS• Why
do
people
hack?
• Some common reasons for hacking include basic
bragging rights, curiosity, revenge, boredom,
challenge, theft for financial gain, sabotage, vandalism,
corporate espionage, blackmail, and extortion. Hackers
are known to regularly cite these reasons to explain their
behavior.
20.
Ethical Hacking CONCEPTS• Who was the youngest hacker?
• Kristoffer
von
Hassel
• At the age of five, Hassel exposed security lapses in
the Microsoft Live Xbox system, prompting wide media
coverage, with some journalists highlighting the
dropping age of hackers and their technology mastery.
21.
Ethical Hacking CONCEPTS• Who Hacked NASA in 1999?
• Jonathan James
• Between August and October of 1999, Jonathan
James used his skills as a hacker to intercept data
from the Defense Threat Reduction Agency or DTRA
(a division of the US department Of defense). He had
access to over 3,000 messages, usernames and
passwords of DTRA employees.
22.
Ethical Hacking CONCEPTS• Why do hackers use Linux?
• Although it is true that most hackers prefer Linux
operating systems, many advanced attacks occur in
Microsoft Windows in plain sight. Linux is an easy
target for hackers because it is an open-source
system. This means that millions of lines of code can
viewed publicly and can easily be modified.
23.
Ethical Hacking CONCEPTS• Who
is
the
best
hacker
in
the
world
2022?
• Today, he is a trusted, highly sought-after security
consultant to Fortune 500 and governments worldwide.
Kevin Mitnick is the world's authority on hacking,
social engineering, and security awareness training. In
fact, the world's most used computer-based end-user
security awareness training suite bears his name.
24.
Ethical Hacking CONCEPTS• What
is
Kali
Linux?
• Kali Linux is a Debian-derived Linux distribution
designed for digital forensics and penetration testing.
It is maintained and funded by Offensive Security.
25.
Ethical Hacking CONCEPTSRules for Ethical Hacking
● Before hacking the network or computer system, first, you must
receive written permission from the system owner.
● Place top priority on protecting the privacy of the owner of the
hacked system.
● Report all the revealed vulnerabilities in a transparent way to the
owner of the hacked system.
● Software and Hardware vendors using that system or product
must also be informed about the system’s vulnerabilities.
26.
Ethical Hacking CONCEPTSEthical Hacking: Legal or Illegal?
Ethical Hacking is a legal action only if the hacker follows all the
rules defined in the Previous slide. The International Council of ECommerce provides certification programs for ethical hacker skills
testing. These certificates must be renewed after a period of time.
There are other ethical hacking certificates that will also suffice,
such as the RHC Red Hat and Kali InfoSec certifications.
27.
Ethical Hacking TERMINOLOGY• Adware − Adware is software designed to force pre-chosen
ads
to
display
on
your
system.
• Attack − An attack is an action that is done on a system to
get
its
access
and
extract
sensitive
data.
• Back door − A back door, or trap door, is a hidden entry to a
computing device or software that bypasses security
measures, such as logins and password protections.
28.
Ethical Hacking TERMINOLOGYBot − A bot is a program that automates an action so that it can be
done repeatedly at a much higher rate for a more sustained period
than a human operator could do it. For example, sending HTTP, FTP
or Telnet at a higher rate or calling script to create objects at a higher
rate.
Botnet − A botnet, also known as zombie army, is a group of
computers controlled without their owners’ knowledge. Botnets are
used to send spam or make denial of service attacks.
29.
Ethical Hacking TERMINOLOGY• Brute force attack − A brute force attack is an automated and
the simplest kind of method to gain access to a system or
website. It tries different combination of usernames and
passwords, over and over again, until it gets in.
• Buffer Overflow − Buffer Overflow is a flaw that occurs when
more data is written to a block of memory, or buffer, than the
buffer is allocated to hold.
30.
Ethical Hacking TERMINOLOGYClone phishing − Clone phishing is the modification of an existing, legitimate email with
a false link to trick the recipient into providing personal information.
Cracker − A cracker is one who modifies the software to access the features which are
considered undesirable by the person cracking the software, especially copy protection
features.
Denial of service attack (DoS) − A denial of service (DoS) attack is a malicious attempt
to make a server or a network resource unavailable to users, usually by temporarily
interrupting or suspending the services of a host connected to the Internet.
DDoS − Distributed denial of service attack.
31.
Ethical Hacking TERMINOLOGYExploit Kit − An exploit kit is software system designed to run on
web servers, with the purpose of identifying software vulnerabilities
in client machines communicating with it and exploiting discovered
vulnerabilities to upload and execute malicious code on the client.
Exploit − Exploit is a piece of software, a chunk of data, or a
sequence of commands that takes advantage of a bug or
vulnerability to compromise the security of a computer or network
system.
32.
Ethical Hacking TERMINOLOGYFirewall − A firewall is a filter designed to keep unwanted intruders
outside a computer system or network while allowing safe communication
between systems and users on the inside of the firewall.
Keystroke logging − Keystroke logging is the process of tracking the keys
which are pressed on a computer (and which touchscreen points are
used). It is simply the map of a computer/human interface. It is used by
gray and black hat hackers to record login IDs and passwords.
Keyloggers are usually secreted onto a device using a Trojan delivered
by a phishing email.
33.
Ethical Hacking TERMINOLOGYLogic bomb − A virus secreted into a system that triggers a malicious
action when certain conditions are met. The most common version is the
time bomb.
Malware − Malware is an umbrella term used to refer to a variety of forms
of hostile or intrusive software, including computer viruses, worms, Trojan
horses, ransomware, spyware, adware, scareware, and other malicious
programs.
Master Program − A master program is the program a black hat hacker
uses to remotely transmit commands to infected zombie drones, normally
to carry out Denial of Service attacks or spam attacks.
34.
Ethical Hacking TERMINOLOGY• Phishing − Phishing is an e-mail fraud method in which the
perpetrator sends out legitimate-looking emails, in an
attempt to gather personal and financial information from
recipients.
• Phreaker − Phreakers are considered the original
computer hackers and they are those who break into the
telephone network illegally, typically to make free
longdistance phone calls or to tap phone lines.
35.
Ethical Hacking TERMINOLOGYRootkit − Rootkit is a stealthy type of software, typically malicious,
designed to hide the existence of certain processes or programs from
normal methods of detection and enable continued privileged access
to
a
computer.
Shrink Wrap code − A Shrink Wrap code attack is an act of exploiting
holes
in
unpatched
or
poorly
configured
software.
Social engineering − Social engineering implies deceiving someone
with the purpose of acquiring sensitive and personal information, like
credit card details or user names and passwords.
36.
Ethical Hacking TERMINOLOGYSpam − A Spam is simply an unsolicited email, also known as junk email,
sent to a large number of recipients without their consent.
Spoofing − Spoofing is a technique used to gain unauthorized access to
computers, whereby the intruder sends messages to a computer with an
IP address indicating that the message is coming from a trusted host.
Spyware − Spyware is software that aims to gather information about a
person or organization without their knowledge and that may send such
information to another entity without the consumer's consent, or that
asserts control over a computer without the consumer's knowledge.
37.
Ethical Hacking TERMINOLOGYSQL Injection − SQL injection is an SQL code injection technique,
used to attack data-driven applications, in which malicious SQL
statements are inserted into an entry field for execution (e.g. to dump
the database contents to the attacker).
Threat − A threat is a possible danger that can exploit an existing bug
or vulnerability to compromise the security of a computer or network
system.
38.
Ethical Hacking TERMINOLOGYTrojan − A Trojan, or Trojan Horse, is a malicious program disguised to look
like a valid program, making it difficult to distinguish from programs that are
supposed to be there designed with an intention to destroy files, alter
information, steal passwords or other information.
Virus − A virus is a malicious program or a piece of code which is capable of
copying itself and typically has a detrimental effect, such as corrupting the
system or destroying data.
39.
Ethical Hacking TERMINOLOGY• Vulnerability − A vulnerability is a weakness which allows
a hacker to compromise the security of a computer or
network system.
• Worms − A worm is a self-replicating virus that does not
alter files but resides in active memory and duplicates
itself.
40.
Ethical Hacking TERMINOLOGY• Cross-site Scripting − Cross-site scripting (XSS) is a type of
computer security vulnerability typically found in web
applications. XSS enables attackers to inject client-side script
into web pages viewed by other users.
• Zombie Drone − A Zombie Drone is defined as a hijacked
computer that is being used anonymously as a soldier or
'drone' for malicious activity, for example, distributing
unwanted spam emails.
41.
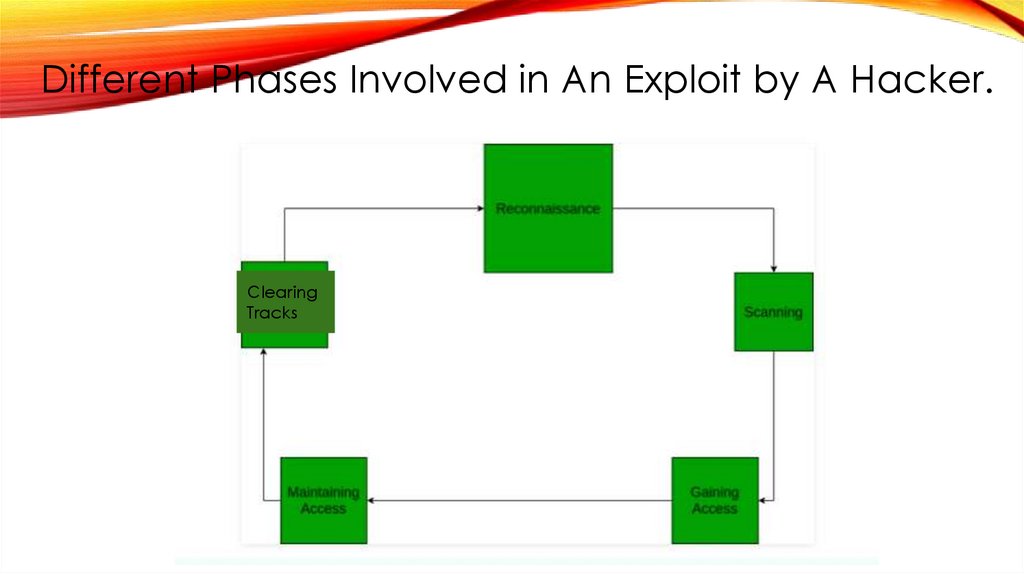
Different Phases Involved in An Exploit by A Hacker.Clearing
Tracks
42.
Different phases involved in an exploit by a Hacker.Five Phases of Ethical Hacking
● Phase 1: Reconnaissance.
● Phase 2: Scanning.
● Phase 3: Gaining Access.
● Phase 4: Maintaining Access.
● Phase 5: Clearing Tracks
43.
Different phases involved in an exploit by a HackerReconnaissance
This is the first step of Hacking. It is also called as
Footprinting and information gathering Phase. This is the
preparatory phase where we collect as much information as
possible about the target. We usually collect information
about three groups,
1. Network
2. Host
3. People involved
44.
Different phases involved in an exploit by a HackerReconnaissance
There are two types of Footprinting:
● Active: Directly interacting with the target to gather
information about the target. Eg Using Nmap tool to scan
the target
● Passive: Trying to collect the information about the target
without directly accessing the target. This involves
collecting information from social media, public websites
etc.
45.
Different phases involved in an exploit by a Hacker.Scanning:
● Port scanning: This phase involves scanning the target for the information
like open ports, Live systems, various services running on the host.
● Vulnerability Scanning: Checking the target for weaknesses or
vulnerabilities which can be exploited. Usually done with help of
automated tools
● Network Mapping: Finding the topology of network, routers, firewalls
servers if any, and host information and drawing a network diagram with
the available information. This map may serve as a valuable piece of
information throughout the hacking process.
46.
Different phases involved in an exploit by a Hacker.Scanning
Three types of scanning are involved:
Port scanning: This phase involves scanning the target for the information like open ports,
Live systems, various services running on the host.
Vulnerability Scanning: Checking the target for weaknesses or vulnerabilities which can be
exploited. Usually done with help of automated tools
Network Mapping: Finding the topology of network, routers, firewalls servers if any, and host
information and drawing a network diagram with the available information. This map may
serve as a valuable piece of information throughout the haking process.
47.
Different phases involved in an exploit by a HackerGaining Access
• This phase is where an attacker breaks into the
system/network using various tools or methods.
• After entering into a system, he has to increase his
privilege to administrator level so he can install an
application he needs or modify data or hide data.
48.
Different Phases Involved in An exploit by A HackerMaintaining Access
• Hacker may just hack the system to show it was vulnerable or
he can be so mischievous that he wants to maintain or persist
the connection in the background without the knowledge of
the user.
• This can be done using Trojans, Rootkits or other malicious
files.
• The aim is to maintain the access to the target until he finishes
the tasks he planned to accomplish in that target.
49.
Different Phases Involved in An exploit by A HackerClearing Tracks
• No thief wants to get caught. An intelligent hacker always
clears all evidence so that in the later point of time, no
one will find any traces leading to him.
• This involves modifying/corrupting/deleting the values of
Logs, modifying registry values and uninstalling all
applications he used and deleting all folders he created.
50.
Different Phases Involved in An exploit by A HackerClearing Tracks
• No thief wants to get caught. An intelligent hacker always
clears all evidence so that in the later point of time, no
one will find any traces leading to him.
• This involves modifying/corrupting/deleting the values of
Logs, modifying registry values and uninstalling all
applications he used and deleting all folders he created.
51.
Overview of Attacks• A cyberattack is a malicious and deliberate attempt by an
individual or organization to breach the information system
of
another
individual
or
organization.
• Usually, the attacker seeks some type of benefit from
disrupting the victim’s network.
52.
Overview of Attacks• A cyberattack is a malicious and deliberate attempt by an
individual or organization to breach the information system
of
another
individual
or
organization.
• Usually, the attacker seeks some type of benefit from
disrupting the victim’s network.
53.
MalwareMalware is a term used to describe malicious software, including
spyware, ransomware, viruses, and worms. Malware breaches a
network through a vulnerability, typically when a user clicks a
dangerous link or email attachment that then installs risky software.
Once inside the system, malware can do the following:
● Blocks access to key components of the network
(ransomware)
● Installs malware or additional harmful software
● Covertly obtains information by transmitting data from the hard
drive (spyware)
● Disrupts certain components and renders the system
inoperable
54.
Phishing• Phishing is the practice of sending fraudulent
communications that appear to come from a reputable
source, usually through email.
• The goal is to steal sensitive data like credit card and login
information or to install malware on the victim’s machine.
Phishing is an increasingly common cyberthreat.
55.
Man-in-the-middle attack• Man-in-the-middle
(MitM)
attacks,
also
known
as
eavesdropping attacks, occur when attackers insert themselves
into a two-party transaction. Once the attackers interrupt the
traffic, they can filter and steal data.
• Two common points of entry for MitM attacks:
1. On unsecure public Wi-Fi, attackers can insert themselves
between a visitor’s device and the network. Without knowing,
the visitor passes all information through the attacker.
2. Once malware has breached a device, an attacker can install
software to process all of the victim’s information.
56.
Denial-of-service attack• A denial-of-service attack floods systems, servers, or
networks with traffic to exhaust resources and bandwidth.
• As a result, the system is unable to fulfill legitimate
requests.
• Attackers can also use multiple compromised devices to
launch
this
attack.
• This is known as a distributed-denial-of-service (DDoS)
attack.
57.
SQL injection• A Structured Query Language (SQL) injection occurs
when an attacker inserts malicious code into a server that
uses SQL and forces the server to reveal information it
normally
would
not.
• An attacker could carry out a SQL injection simply by
submitting malicious code into a vulnerable website
search box.
58.
REPORTED INCIDENT OF CYBERTERRORISM RELATED TO WATER
SOURCE: THESIS OF GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
59.
ATTACKS ON HARRISBURGWATER TREATMENT PLANT
• IT IS ONE OF THE MOST FAMOUS CYBER-
ATTACKS ON WATER SCADA SYSTEM.
• IN 2006, A HACKER COMPROMISED REMOTE
ACCESS OF EMPLOYEE’S LAPTOP AND USED
COMPROMISED LAPTOP AS AN ENTRY POINT
INTO TREATMENT PLANT OF WATER AT
HARRISBURG AND INSTALL A COMPUTER
VIRUS AND SPYWARE.
• AFTER THE INCIDENT OF THE INTRUSION, THE
PLANT CHANGED ALL SYSTEM PASSWORDS
AND ALSO ELIMINATED HOME ACCESS TO THE
NETWORK.
60.
60ATTACKS ON TEHAMA
COLUSA CANAL AUTHORITY
• MICHAEL KEEHN WAS THE MAIN PERPETRATOR
BEHIND THIS ATTACK. HE WAS AN OLD
EMPLOYEE AT TCCA.
• HE
DELIBERATELY ENTERS AND DESTRUCTS
COMPUTER
SYSTEM
AND
INSTALLED
ILLEGITIMATE SOFTWARE IN SCADA SYSTEM OF
TCAA.
• HE WAS ARRESTED FOLLOWING A GRAND
JURY INDICTMENT ON NOVEMBER 15, 2007. HE
GOT
A
SENTENCE
OF
10
YEARS
IMPRISONMENT. THE INTRUSION COST THE
TCCA MORE THAN $5,000 IN DAMAGES.
61.
ATTACKS ON OUR EMULATOR:TOOLS USED & ATTACKER
SECURITY ATTACKS→TOOLS
USED
1. INFORMATION DISCLOSURE
→ FIREFOX ANALYZER,
WAPPALYZER
2. SCANNING : ACCESSIBLE
FOLDER → DIRBUSTER
3. EXPLOITATION: SQL
INJECTION → SQLMAP
4. EXPLOITATION: DOS →
SOURCE: THESIS OF GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
SQLMAP
62.
ATTACKS ON OUREMULATOR: SUMMARY
SOURCE: THESIS OF GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
63.
STEPS TAKEN TO ENHANCE SECURITY• WE TAKE FOLLOWING STEPS
• INPUT VALIDATION,
• PARAMETERIZED QUERIES AND
• USAGE OF STORED PROCEDURES
• TO REDUCE THE POSSIBILITY OF
EXPLOITATION: SQL INJECTION AND DOS.
• WE MAKE IMAGES FOLDER NO MORE
REACHABLE TO REDUCE THE ATTACKS OF
FORCED BROWSING - ACCESSIBLE FOLDER.
• WE INTEGRATE SECUBE IN OUR EMULATOR.
64.
64SECUBE
• SECUBE IS DEVELOPED BY BLU5 GROUP.
• BLU5 GROUP IS A GLOBAL ALLIANCE OF BLU5
LABS LTD MALTA, CINI ITALY, LERO IRELAND,
LIRMM FRANCE AND TU DORTMUND GERMANY.
• THE CORE OF SECUBE IS A 3-D SYSTEM ON CHIP
(SOC).
• THIS SOC CONSISTS OF
HARDWARE COMPONENTS:
THE
FOLLOWING
• STM32F4 PROCESSOR
• LATTICE MACHXO2-7000 FPGA
• EAL5+ CERTIFIED SMART CARD
SOURCE: THESIS OF GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
65.
SECUBE IN BETWEEN SLAVE ANDMASTER CONTROLLER
• WE INSERT SECUBE IN
BETWEEN
SLAVE
AND
MASTER RASPBERRY PI.
• SECUBE ENCRYPTS AND
DECRYPTS
MESSAGE
TO/FROM MASTER/SLAVE
USING AES.
SOURCE: THESIS OF GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
66.
WEB-INTERFACE OF OUREMULATOR
GRAN SASSO SCIENCE INSTITUTE L'AQUILA, ITALY
67.
Identification of Exploit Categories• Software and networks come with built-in protection against
hackers, sort of like locks that keep unwanted guests from
sneaking
inside.
• A vulnerability, then, is like an accidental open window that a
thief
can
climb
through.
• In the case of a computer or network, thieves can install
malicious software through these vulnerabilities (open windows)
in order to control (infect) the system for their own nefarious
ends.
68.
Identification of Exploit Categories• Vulnerabilities are weaknesses or security flaws in a system or
network that can allow malicious actors or hackers a way in.
• So if a vulnerability is the open window into the system, an
exploit is the rope or ladder the thief uses to reach the open
window.
• An exploit is simply a tool created to leverage a specific
vulnerability — without vulnerabilities, there’s nothing to
exploit.
69.
Identification of Exploit Categories● In the illustration above, the window on the left is locked, so there’s no
vulnerability.
● The window on the right is open and vulnerable, but too high up to exploit.
● The window in the middle is open and vulnerable and, crucially, close
enough to the ground to exploit.
70.
Identification of Exploit Categories• Exploits are commonly classified as one of two types:
known
or
unknown.
• Known exploits have already been discovered by
cybersecurity
researchers.
• Whether the known exploit is due to a vulnerability in the
software, OS, or even hardware, developers can code
patches to plug the hole.
71.
Identification of Exploit Categories• Unknown exploits or zero-day exploits, in contrast, are created
by cybercriminals as soon as they discover a vulnerability, and
they use the exploit to attack victims on the same day.
• When a zero-day exploit attack happens, software developers
and cybersecurity researchers have to scramble to figure out how
the exploit works and how to patch the vulnerability.
72.
Identification of Exploit Categories• Unknown exploits or zero-day exploits, in contrast, are created
by cybercriminals as soon as they discover a vulnerability, and
they use the exploit to attack victims on the same day.
• When a zero-day exploit attack happens, software developers
and cybersecurity researchers have to scramble to figure out how
the exploit works and how to patch the vulnerability.
73.
Some Famous Exploit: EternalBlue• EternalBlue is one of the most famous — and most damaging —
exploits
out
there.
• Originally developed by the NSA, EternalBlue was stolen by the
Shadow Brokers hacking group and then leaked in March 2017.
• Although Microsoft discovered the leak and issued a security
update to patch the vulnerability, many people and organizations
failed
to
apply
the
patch
in
time.
• This allowed hackers to proceed with some of the most damaging
cyberattacks in history, including WannaCry and NotPetya.
74.
Some Famous Exploit: WannaCry• WannaCry was the stuff of nightmares: a wormable attack that used
the EternalBlue exploit to spread exponentially across computer
networks, infecting 10,000 machines per hour in 150 countries.
• As ransomware, WannaCry encrypted computers, rendering them
inaccessible — a huge issue for the national health services,
governments, universities, and large corporations that WannaCry hit.
• Although WannaCry is no longer active, other exploits can still take
advantage of EternalBlue to attack Windows users running outdated
software — so make sure yours is updated.
75.
Legal implications of Hacking• Is Ethical Hacking legal in India?
• Hacking is a wrongful act under Indian legal system.
• Although Indian laws do not specifically deal with ethical
hacking yet hacking is a punishable offense in India.
• The act of Hacking contravenes the underlying principles of
India legal system.
• The subject of ethical hacking has not been dealt with
explicitly in Indian laws, therefore, it enjoyed neutral status
under Indian legal system.
76.
Legal implications of HackingInformation Technology Act, 2000
Information technology (IT) Act, 2000 is a watershed
movement in Indian legal system and a landmark in the
cyber
law
arena.
If we look at the provisions of IT act cautiously, we can
deduce that it covers almost all the wrongs that emerge from
hacking because hacking is such offence which is very wide
and covers a lot of other offenses
77.
Legal implications of Hacking• Chapter XI Section 66 of IT Act, 2000 particularly deals with the act
of
hacking.
• Section 66(1) defines a hack as, any person, dishonestly or
fraudulently, does any act referred to in Section 43 is called hacking,
• Section
66(2)
prescribes
the
punishment
for
it.
• Hacking is a punishable offense in India with imprisonment up to 3
years, or with fine up to two lakh rupees, or with both.
78.
Legal implications of Hacking• Chapter IX Section 43 of IT act, 2000 prescribes a penalty for the
damage
to
computer
or
computer
system.
• It is a common thing which happens whenever a computer system is
hacked.
• Black hats damage the system that they hack and steal the
information.
• This enumerative provision includes a lot of activities.
79.
Legal implications of Hacking• Chapter XI Section 65 of the said act makes tampering with
computer
source
documents
an
offense.
• Section 72 of the same chapter makes the breach of
confidentiality
and
privacy,
a
punishable
offense.
• This is the most common aftermath of hacking.
80.
What is Reverse Engineering?• Reverse engineering refers
to the duplication of another
producer’s
product
following
a
thorough
examination
of
its
construction or composition.
81.
Reverse Engineering• Benefits:
• Examining the structures and processes of an
application can lead to product innovation.
• Knowledge gain by other researcher’s work
• Reconstructing a product that is outdated
• The discovery of software vulnerabilities
• The development of applications that are more efficient
and cheap.
82.
Reverse Engineering in Hacking• In the security world, researchers use reverse engineering
to find security risks in programs, to understand malicious
applications,
etc.
• Cyber-criminals can also use this technique to exploit
security bugs in applications, the difference with the
security researchers is what they do with that vulnerability
information.
83.
Reverse Engineering in HackingIn a report conducted on April 2019, found that 97% of the 30
mobile financial apps that were tested, were lacking binary
protection, making decompiling and review of the source code
possible.
Upon decompiling an app all kinds of sensitive information can be
exposed, API URLs API keys hardcoded into the apps.
The URLs can lead attackers to nonstandard port numbers,
development servers, private keys, application file directories that
were used for testing by developers, quality assurance engineers
and can lead an attacker to compromise entire applications.
84.
Reverse Engineering: Exploit, Vulnerabilities• The more obfuscated the code is, the more often it’s true that the
code in question is rich in vulnerabilities.
• We can use our expertise to examine our environment and
develop exploits for our red teams to test our blue team's or
company's defenses.
• We won’t understand the true impact of vulnerabilities in your
environment unless you can measure impact.
85.
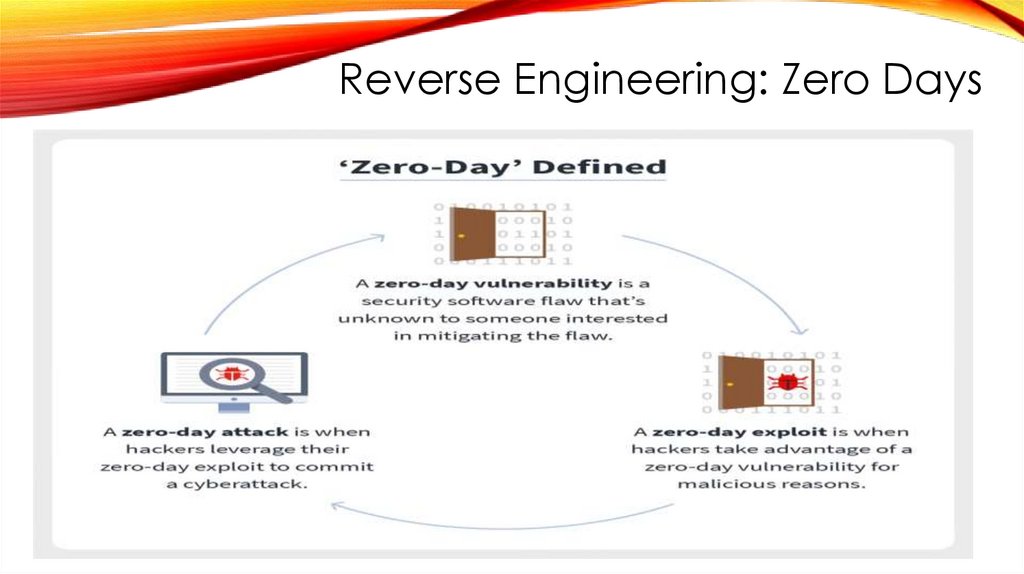
Reverse Engineering: Zero Days86.
Methodology:Reverse Engineering & Exploit DevelopmentDiscover functionality, in order to determine how to undermine it
Use targeted fuzzing to identify behavior which can be abused
Reverse engineer proprietary protocols
Find vulnerabilities
Build attack chains for exploits
Provide exploit proof of concepts or packaged exploit modules
87.
Reverse Engineering and manual PT• What
is
Penetration
Testing?
• Penetration Testing has been evolving throughout the year with
a robust increase in highly sophisticated attacks.
• Every organization is now aware of the damage caused by
cyber-attacks.
• Private and Government organizations are now conducting
scheduled penetration tests for every three months or less than
that.
88.
Reverse Engineering and manual PT• The attacks are increasing day by day and now almost every
device is vulnerable to an unpatched zero-day vulnerability.
• Attacks like Meltdown and Spectre have gone too deep that it
exploits
a
vulnerability
at
the
processor
level.
• Likeways, the firmware is also one of the important attack
vectors. This paper discusses multiple methods for reverse
engineering a router firmware and the process of backdooring it.
89.
Manual Penetration TestingManual penetration testing is the testing that is done by human
beings. In such type of testing, vulnerability and risk of a machine
is tested by an expert engineer.
Generally, testing engineers perform the following methods −
● Data Collection − Data collection plays a key role for testing.
One can either collect data manually or can use tool services
(such as webpage source code analysis technique, etc.) freely
available online. These tools help to collect information like
table names, DB versions, database, software, hardware, or
even about different third party plugins, etc
90.
Manual Penetration Testing● Vulnerability Assessment − Once the data is collected, it helps
the testers to identify the security weakness and take
preventive steps accordingly.
● Actual Exploit − This is a typical method that an expert tester
uses to launch an attack on a target system and likewise,
reduces the risk of attack.
● Report Preparation − Once the penetration is done, the tester
prepares a final report that describes everything about the
system. Finally the report is analyzed to take corrective steps to
protect the target system.
91.
Manual Penetration Testing92.
Manual Penetration TestingManual penetration testing is normally categorized in two following ways:
● Focused Manual Penetration Testing − It is a much focused method that
tests specific vulnerabilities and risks. Automated penetration testing
cannot perform this testing; it is done only by human experts who
examine specific application vulnerabilities within the given domains.
● Comprehensive Manual Penetration Testing − It is through testing of
whole systems connected with each other to identify all sorts of risk and
vulnerability. However, the function of this testing is more situational, such
as investigating whether multiple lower-risk faults can bring more
vulnerable attack scenario, etc
93.
Pro's and Con's of Manual Penetration TestingRead more at: https://www.appknox.com/blog/automated-penetration-testing-vs.-manual-penetration-testing
94.
Reverse Engineering Hacking Tools• Binwalk – is an inbuilt Linux utility that allows us to carve
and analyze binary files.
• Unsquashfs – is a tool to decompress or extract the
squashfs file system.
• Hexdump – allows the users to view the hexadecimal view of
the specific input data with ability to extract file contents into
multiple formats like decimal, octal, and ASCII.
• Objdump – displays information about the object files and
used to disassemble executable files.
• Strings – extracts the strings embedded inside the binary
files and other executable files
95.
Reverse Engineering Hacking Tools• GDB – the GNU Debugger helps in decompiling executables
and binary files that are written in embedded C, C++, etc.
• Radare2 – is a framework built for reverse engineering and
analyzing binaries.
• Ghidra – consists of a set of reverse engineering tools and
licensed open source by NSA.
• IDA – is commercial software that allows debugging and
decompiling the source code from executables.
• Firmware mod kit – allows decompression of various firmware
in embedded devices. It supports various file systems and
versions such as SquashFS 2.0, 3.0 and 4.0.
96.
What is Banner Grabbing?Banner grabbing is the process of obtaining a target company’s
application names and versions, regardless of manner—manually or
automatically by using an open-source tool—in preparation for an attack.
All connected systems and devices often expose confidential information
that includes software names and operating systems (OSs), along with
their
versions,
collectively
known
as
“banner
data.”
Knowing these data points allows threat actors to find exploitable
vulnerabilities in target networks
97.
What is Banner Grabbing?Banner
Penetration testers also perform the act when an organization hires
them
to
determine
all
its
weak
spots.
The process is also useful for IT teams performing security audits
to know which systems and applications require stronger
cyberdefense.
Think of banner grabbing as sending a spy to work for a competitor
so he or she can report the company’s weaknesses to his or her
real employer.
grabbing
is
not
always
bad.
98.
Banner Grabbing Tools and Techniques• Telnet: this classic cross-platform client allows hackers and
pentesters to interact with remote services for banner
grabbing.
• Pen-testers and attackers can telnet to hosts on the default
telnet port (TCP port 23) to discover relevant information.
• Attacks can telnet other commonly used ports like SMTP,
HTTP, and POP3. Most operating systems can establish
Telnet sessions, allowing users to perform banner grabbing
99.
Banner Grabbing Tools and Techniques• Whatweb: the tool recognizes websites, helping hackers
and security analysts to grab the web-applications banner
by disclosing the server information such as the IP
address, version, webpage title, and running operating
system
• cURL: the tool has a command that includes the
functionality for retrieving banner details from HTTP
servers
100.
Banner Grabbing Tools and Techniques• Wget: the banner grabbing tool can lead users to
remote or local servers’ banner.
• Wget uses a simple script to suppress the expected
output and print the headers sent by the HTTP
server
• Netcat: the tool is one of the oldest and popular
network utilities for Unix and Linux.
101.
Banner Grabbing Tools and TechniquesDMitry: The Deepmagic Information Gathering Tool can gather as
much host information as possible.
DMitry allows attackers to get all the data from a remote host,
including DNS enumeration, subdomain mapping, open ports, and
much more.
Nmap: this simple banner grabber connects to an open TCP port and
prints out details sent by the listening service within a few seconds
102.
How Does Banner Grabbing Work?• A banner grabbing attack has three necessary steps.
• First, the attacker chooses the service he or she wants to
target.
• He or she then launches a request to the target application
or
system.
• When the software or device responds, he or she inspects
the response to determine what exploit to use for the
attack.
103.
NMAP for Banner Grabbing• sudo nmap -Pn -F --script banner scanme.nmap.org
104.
NMAP for Banner Grabbing• sudo nmap -Pn -p22,80 --script banner scanme.nmap.org
105.
Two Types of Banner Grabbing Attacks• There
are
• Active
• Passive
two
kinds
of
banner
grabbing
106.
Two Types of Banner Grabbing AttacksWhat Is Active Banner Grabbing?
• Specially crafted packets are sent to remote OS and the
responses are noted.
• The responses are then compared with a database to
determine the OS.
• Response from different OSes varies due to differences in
TCP/IP stack implementation.
107.
Two Types of Banner Grabbing AttacksWhat
Passive banner grabbing allows users to get the same information
while avoiding exposure.
Banner grabbing from error messages: Error messages provide
information such as type of server, type of OS, and SSL tool used by
the target remote system.
Sniffing the network traffic: Capturing and analyzing packets from the
target enables an attacker to determine OS used by the remote
system.
Banner grabbing from page extensions: Looking for an extension in
the URL may assist in determining the application version. Example:
.aspx => IIS server and Windows platform.
Is
Passive
Banner
Grabbing?
108.
Banner Grabbing from Page ExtensionsLooking for an extension in the URL may assist in determining
the application version.
• Example: .aspx => IIS server and Windows platform.
• Example: .jsp => Apache Tomcat and Java Virtual Machine
• Example: .php => LAMP server and Linux platform.
109.
Preventing Banner GrabbingWe can follow these tips to prevent banner grabbing:
● Restrict access to services on the network
● Shut down unused or unnecessary services running on network hosts
● We can override our server’s default banner behavior to hide version
information. System administrators can customize default banners,
configure the network host’s application or operating system to disable
the banners, or remove information from the banners that could give an
attacker a leg up.
● Keep our server and systems up to date to secure our applications
against known server exploits
110.
Preventing Banner GrabbingDisabling or Changing Banner
● Display false banners to misguide attackers.
● Turn off unnecessary services on the network host to limit the
information disclosure.
● Use ServerMask tools to disable or change banner information.
● Apache 2.x with mod_headers module - use a directive in
httpd.conf file to change banner information Header set
Server "New Server Name".
● Alternatively,
change
the
ServerSignature
line
to
111.
Preventing Banner GrabbingHiding File Extensions from Web Pages
● File extensions reveal information about the underlying server
technology that an attacker can utilize to launch attacks.
● Hide file extensions to mask the web technology.
● Change application mappings such as .asp with .htm or .foo, etc. to
disguise the identify of the servers.
● Apache users can use mod_negotiation directives.
● IIS users use tools such as PageXchanger to manage the file
extensions.
● It is even better if the file extensions are not at all used.
112.
SHODAN• Shodan is a search engine that lets users search for
various types of servers (webcams, routers, servers, etc.)
connected to the internet using a variety of filters.
• The website scans the Internet for publicly accessible
devices.[12]
• The primary users of Shodan are cybersecurity
professionals, researchers and law enforcement agencies.
• While cybercriminals can also use the website, some have
access to botnets that could accomplish the same task
without detection.
113.
https://www.shodan.io/search/examplesSHODAN
114.
TELNET115.
What's that site running?• https://www.netcraft.com
• Using results from our internet data mining, find out the
technologies and infrastructure of any site.
116.
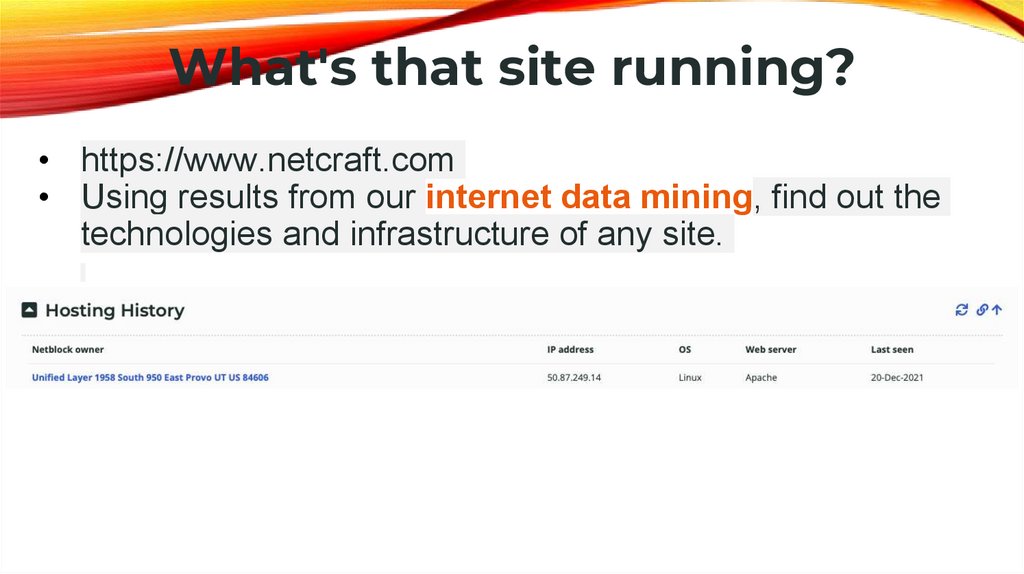
What's that site running?• https://www.netcraft.com
• Using results from our internet data mining, find out the
technologies and infrastructure of any site.
117.
What's that site running?• https://www.netcraft.com
• Using results from our internet data mining, find out the
technologies and infrastructure of any site.
118.
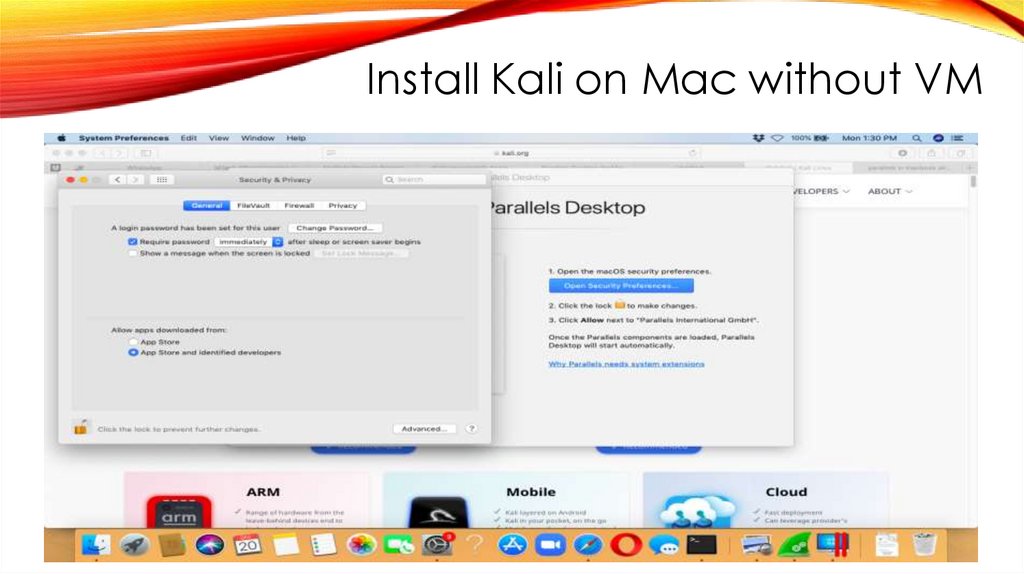
Install Kali on Mac without VM119.
Install Kali on Mac without VM120.
Install Kali on Mac without VM121.
Install Kali on Mac without VM122.
Install Kali on Mac without VM123.
Banner grabbing using Kali LinuxCommon Way to Banner Grabbing Against Your Target:
● whatweb
● wget
● cURL
● Wappalyzer
● dmitry
124.
Vulnerability Scanning in Human Life• Taking chances that might lead to rejection
• Talking about mistakes you have made
• Sharing personal information that you normally
keep private
• Feeling difficult emotions such as shame, grief, or
fear
• Reconnecting with someone you have fallen out with
• Being honest about what you need in a relationship,
including your boundaries and expectations
125.
Vulnerability Scanning in Hacking• An Approved Scanning Vendor (ASV), for example, is a
service provider that is certified and authorized by the
Payment Card Industry (PCI) to scan payment card
networks.
• Vulnerability scans are also used by attackers looking for
points of entry.
126.
Vulnerability Scanning in Hacking• A vulnerability scanner runs from the end point of the
person inspecting the attack surface in question.
• The software compares details about the target attack
surface to a database of information about known security
holes in services and ports, anomalies in packet
construction, and potential paths to exploitable programs
or
scripts.
• The
scanner
software
attempts
to
exploit
each
127.
Vulnerability Scanning in Hacking• Running a vulnerability scan can pose its own risks as it is
inherently intrusive on the target machine’s running code.
• As a result, the scan can cause issues such as errors and
reboots, reducing productivity.
128.
Types of Vulnerability ScanningThere are two approaches to vulnerability scanning,
authenticated
and
unauthenticated
scans.
• In the unauthenticated method, the tester performs the scan
as an intruder would, without trusted access to the network.
Such a scan reveals vulnerabilities that can be accessed
without
logging
into
the
network.
• In an authenticated scan, the tester logs in as a network
user, revealing the vulnerabilities that are accessible to a
trusted user, or an intruder that has gained access as a
trusted user.
129.
Types of Vulnerability Scanning• An external vulnerability scan can help organizations to
identify and fix security vulnerabilities that an adversary can
use to gain access to its network. External vulnerability scan
is performed from outside an organization’s network,
targeting IT infrastructure that is exposed to the internet
including web applications, ports, networks etc..
An external scan can detect vulnerabilities in the perimeter
defenses such as:● Open ports in the network firewall
● Specialized web application firewall.
130.
Types of Vulnerability ScanningAn internal vulnerability scan is carried out from inside an
enterprise network. These scans allow you to harden and protect
applications and systems that are not covered by external scans.
An internal vulnerability scan can detect issues such as: –
• Vulnerabilities that can be exploited by an adversary who has
penetrated the perimeter defenses
• Threat posed by malware that has made it to inside the network
• Identify “insider threats” posed by disgruntled employees or
contractors
131.
Vulnerability Scanner• Many organizations use multiple vulnerability scanners to
ensure they’re getting full coverage of every asset,
creating
a
complete
picture.
• Over the years, many different scanners have been
developed, providing a lot of different options and
features.
• Here’s a list of ones favored by Core Security experts, in
alphabetical order:
132.
Vulnerability ScannerLeading vulnerability scanners provide users with information
about:
• Weaknesses in their environment
• Insights into degrees of risk from each vulnerability
• Recommendations on how to mitigate the vulnerability
133.
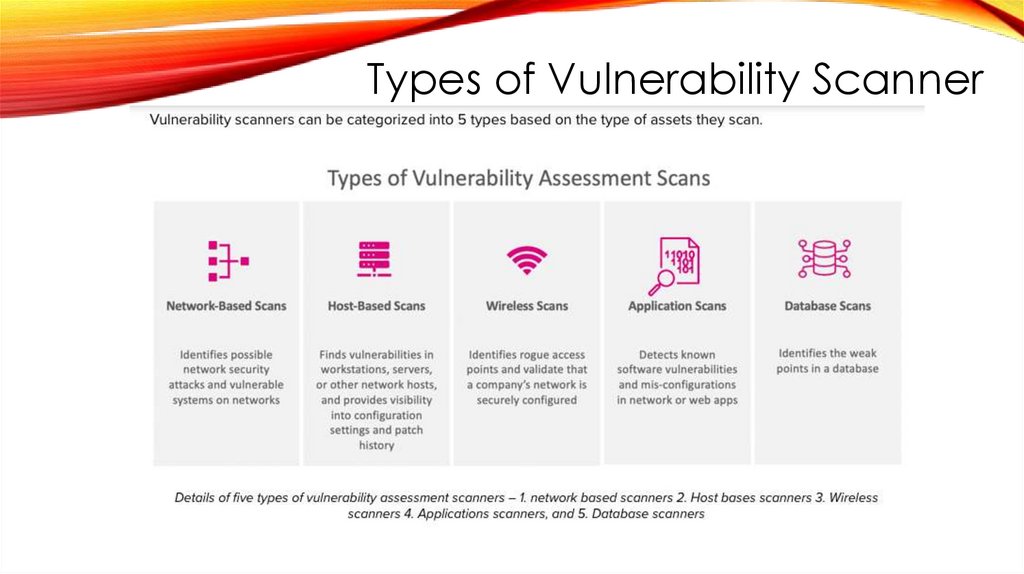
Types of Vulnerability Scanner134.
Network-based scanners• Network based vulnerability scanners identify possible network
security attacks and vulnerable systems on wired or wireless
networks.
• Network-based scanners discover unknown or unauthorized
devices and systems on a network, help determine if there are
unknown perimeter points on the network, such as unauthorized
remote access servers, or connections to insecure networks of
business partners.
135.
Host-based scanners• Host based vulnerability scanners are used to locate and
identify vulnerabilities in servers, workstations, or other
network hosts, and provide greater visibility into the
configuration settings and patch history of scanned
systems.
• Host-based vulnerability assessment tools can also
provide an insight into the potential damage that can be
done by insiders and outsiders once some level of access
is granted or taken on a system.
136.
Wireless scanners• Wireless vulnerability scanners are used to identify rogue
access points and also validate that a company’s network
is securely configured.
137.
Application scanners• Applications vulnerability scanners test websites in order
to detect known software vulnerabilities and erroneous
configurations in network or web applications.
138.
Database scanners• Database vulnerability scanners identify the weak points in
a database so as to prevent malicious attacks
139.
Vulnerability Scanner1. Acunetix
Acunetix is a web vulnerability scanner that features advanced
crawling technology to find vulnerabilities to search every type of web
page—even those that are password protected.
2. beSECURE
beSECURE is a self-service vulnerability scanner from Beyond
Security that can be deployed on-premise, in the cloud, or in hybrid
environments. This solution offers both network and web application
scanning and has a vulnerability database that is updated daily.
140.
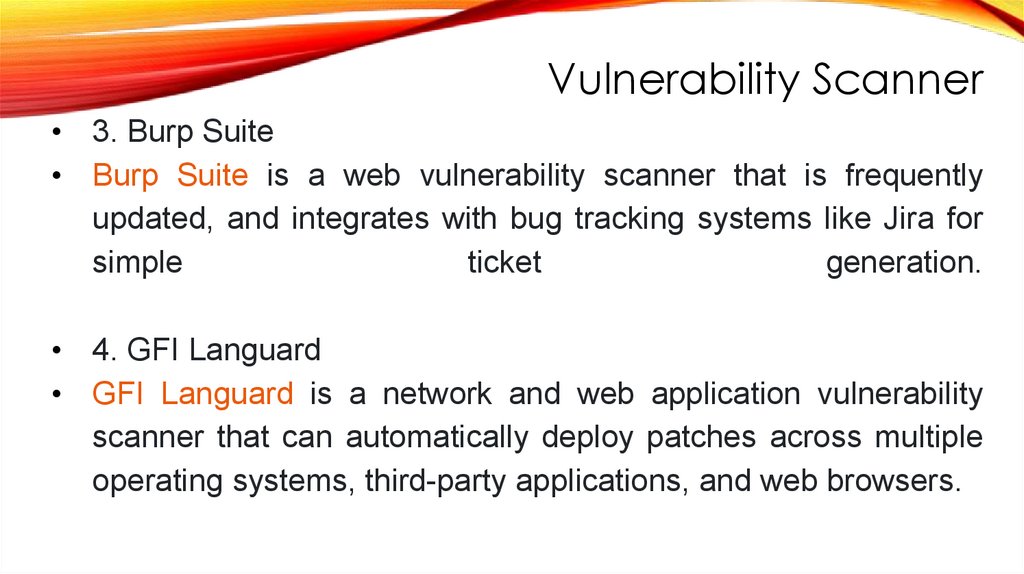
Vulnerability Scanner• 3. Burp Suite
• Burp Suite is a web vulnerability scanner that is frequently
updated, and integrates with bug tracking systems like Jira for
simple
ticket
generation.
• 4. GFI Languard
• GFI Languard is a network and web application vulnerability
scanner that can automatically deploy patches across multiple
operating systems, third-party applications, and web browsers.
141.
Vulnerability Scanner• 5. Frontline is a patented network vulnerability scanner
that is a part of Frontline.Cloud, a cloud-native SaaS
security platform from Digital Defense. This security
platform also offers web application scanning as well as
other vulnerability management and threat assessment
technology.
• 6. Nessus is one of the most popular vulnerability
scanners, with over two million downloads across the
globe. Additionally, Nessus provides comprehensive
coverage, scanning for over 59,000 CVEs.
142.
Vulnerability Scanner7. Nexpose by Rapid7 collects data in real-time in order to
constantly provide a live view of an organization’s shifting network.
Since the CVSS risk score scale is 1-10, this vulnerability scanner
developed its own risk score scale of 1-1000 in order to provide
more nuance. It takes factors like vulnerability age and public
exploits/malware
kits
into
account.
8. Nmap is an open source, free security scanner that is also used
by organizations for network discovery, inventory, managing
service upgrade schedules, and monitoring host or service uptime.
143.
Vulnerability Scanner• 9. OpenVAS is an open source vulnerability scanner
maintained by Greenbone Networks. The scanner also has a
regularly updated community feed, which includes over
50,000
vulnerability
tests.
• 10. Qualys Guard is a hub for Qualys’ IT, security, and
compliance cloud apps. It features a robust vulnerability
scanner that helps centralize vulnerability management.
144.
Vulnerability Scanner• 11. Qualys Web Application Scanner is a cloud-based
application that both finds official and “unofficial” apps
throughout an environment, and also detects OWASP top
ten risks, along with other web application vulnerabilities.
• 12. SAINT is a holistic scanner that identifies all of the
critical assets in an environment, creating asset tags and
tracking them to provide faster remediation for the highest
priority assets.
145.
Vulnerability Scanner• 13. Tenable provide network and web vulnerability
assessments using Nessus technology. They use
Predictive Prioritization, which combines vulnerability data,
threat intelligence and data science to create a detailed
risk
score.
• 14. Tripwire IP360 is a scalable vulnerability scanner that
can scan everything in an organization’s environment,
including previously-undetected assets using both
agentless and agent-based scans.
146.
What is the difference between vulnerabilityscanning and penetration testing?
• Vulnerability scanning detects known flaws, lack of security
controls, and typical misconfigurations in network and operating
systems.
• Penetration testing is a technique for demonstrating the security
of your network by simulating an attack to exploit flaws.
• Vulnerability scanning is used for defensive and offensive
cybersecurity methods, while penetration testing is used for
offensive cybersecurity methods.
147.
What is the difference between vulnerabilityscanning and penetration testing?
• Vulnerability scanning and pen testing are essential
security measures and vulnerability management tools
used by businesses to stay ahead of today’s security
issues.
• Vulnerability scanning and penetration testing may both be
used in the cyber risk assessment process to assist
identify which measures are appropriate for the company,
department,
or
profession.
• To mitigate cybersecurity risk, they must all work together.
148.
How Often Should You Get A Vulnerability Scan?• While each company’s needs are unique, it’s a good idea
to do network vulnerability checks at least once a quarter.
• On the other hand, vulnerability scans may be necessary
on a monthly or weekly basis, depending on compliance,
major infrastructure upgrades, and internal network
security capabilities.
149.
How long does it take to perform a vulnerability scan?• A vulnerability scan can take anywhere from 20 to 60 minutes,
depending on the number of IPs needing to be checked,
whereas web scans might take anywhere from 2 to 4 hours.
• A network administrator or an internal security team can
automate and manage scans. Scanning frequency is
determined by the extent of the site to be scanned, network
latency
and
system
services
to
be
evaluated.
• Vulnerability scans are often performed monthly, quarterly, or
yearly unless there are unique compliance, regulation, legal, or
industry considerations.
150.
How Much do Vulnerability Scans Cost?• The cost of a vulnerability scan is affected by various
elements, including the infrastructure being examined,
such as an internal network or online application.
• Vulnerability assessments can cost anywhere from $2,000
to $2,500, depending on the amount of IP addresses,
servers,
or
apps
analyzed.
• Vulnerability scans are priced using a variety of methods.
151.
Framework Requirements for Vulnerability ScanningISO 27001: Requires quarterly external and internal vulnerability
scans
HIPAA: Requires a thorough risk assessment and vulnerability
process, which can be identified with vulnerability scanning
PCI DSS: Requires quarterly external and internal scans
conducted by an ASV (Approved Scanning Vendor)
FISMA: Requires documentation and implementation of a
vulnerability program to protect the availability, confidentiality, and
integrity of IT systems
NIST: Requires either quarterly or monthly vulnerability scans
depending on the particular NIST framework (8001-171, 800-53,
etc.)
152.
Vulnerability Assessment Methodology• 1. Determine Critical and Attractive Assets
• The first step in vulnerability assessment is gaining an
understanding of your entire ecosystem, and determining
which networks and systems are more critical to your
business
operation.
• 2. Conduct Vulnerability Assessment
• Actively scan your entire network or system either through
automated tools or manual pen-testingto identify security
flaws and weaknesses.
153.
Vulnerability Assessment Methodology3. Vulnerability Analysis and Risk Assessment
The next phase in the vulnerability assessment methodology is
identifying the source as well as the root cause of the security
weakness identified in phase two. This offers a coherent view of
remediation. It involves assigning the severity score or rank to each
susceptibility, based on factors like.
What data are at risk?
Which network or system is affected?
The severity of the possible attacks
Ease of compromise
Potential damage if an attack happens
154.
Vulnerability Assessment Methodology4. Remediation
The main objective of this phase is the closing of security
gaps. For each vulnerability identified, determine the effective
path for mitigation. Certain remediation actions might
include:
● Update all the configuration or operational changes
● Develop and implement vulnerability patches
155.
Vulnerability Assessment Methodology● 5. Re-Evaluate System with Improvements
● Once the security weaknesses are remediated, analyze the
system with the proposed changes or upgrades.
● This phase involves identifying the new estimates for the
probability of neutralization, the probability of interruption,
and the probability of system effectiveness.
● Repeat this entire process until the system satisfactorily
eliminated all security vulnerabilities and increased with
overall effectiveness.
156.
Vulnerability Assessment Methodology● 6.
Report
Results
● The final phase in the security vulnerability assessment
methodology is reporting the assessment result
understandably.
● The main goal of reporting is to offer accurate
information, which clearly defines the system’s
effectiveness and recommends potential solutions if the
current security measure seems ineffective.
157.
Installing Kali Linux in NonCloud Environment
158.
UNINSTALL VIRTUAL BOX159.
UNINSTALL VIRTUAL BOX160.
UNINSTALL VIRTUAL BOX161.
DOWNLOAD VIRTUAL BOX162.
DOWNLOAD VIRTUAL BOX163.
DOWNLOAD VIRTUAL BOX164.
DOWNLOAD VIRTUAL BOX165.
INSTALL VIRTUAL BOX166.
INSTALL VIRTUAL BOX167.
INSTALL VIRTUAL BOX168.
INSTALL VIRTUAL BOX169.
INSTALL VIRTUAL BOX170.
INSTALL VIRTUAL BOX171.
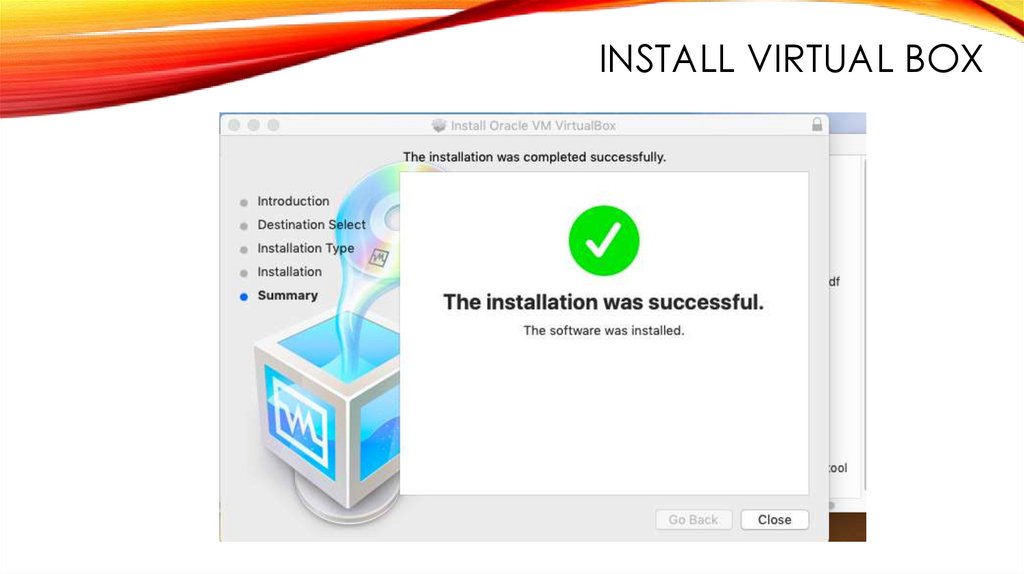
INSTALL VIRTUAL BOX172.
INSTALL VIRTUAL BOX173.
INSTALL VIRTUAL BOX174.
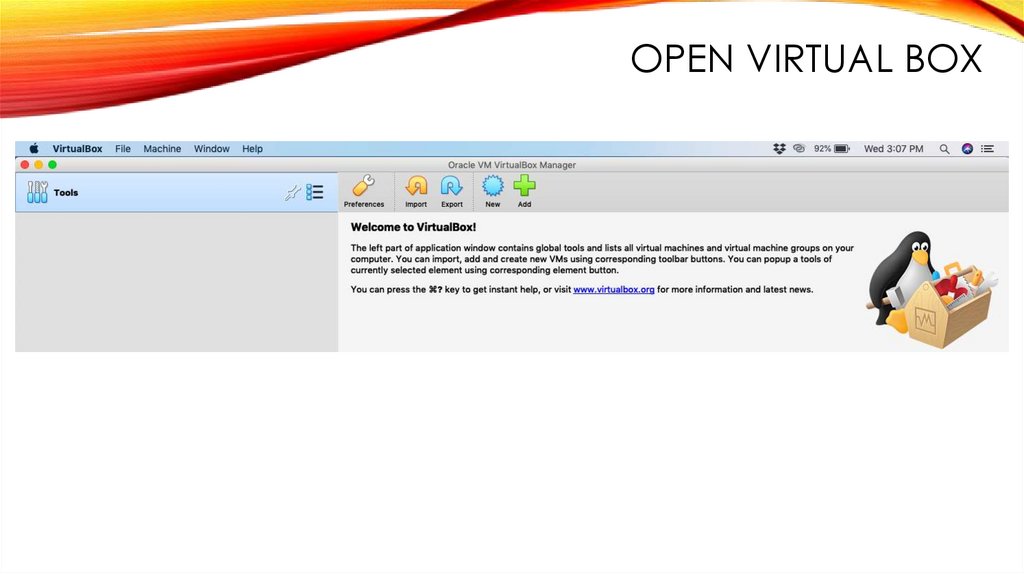
OPEN VIRTUAL BOX175.
OPEN VIRTUAL BOX176.
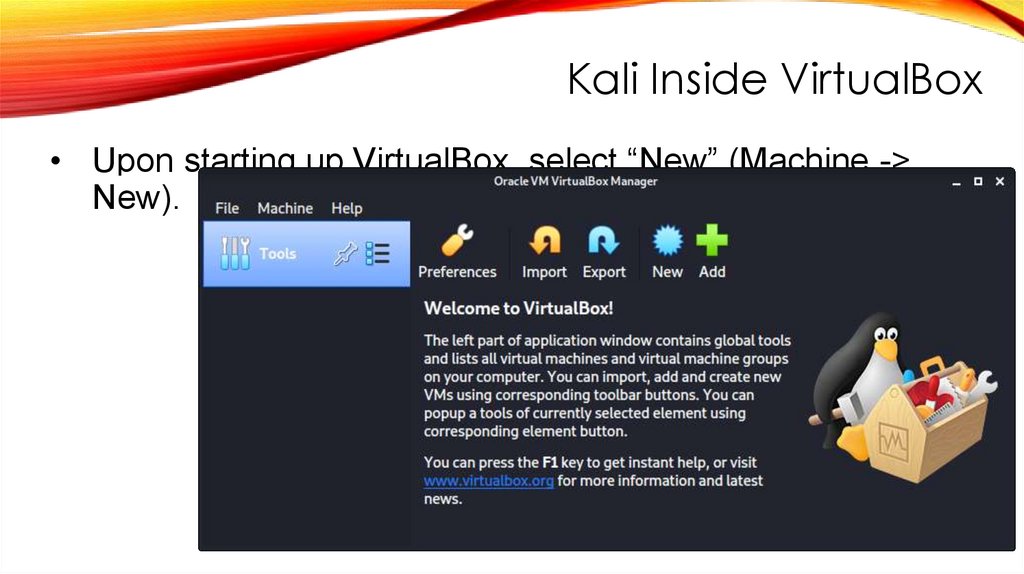
Download Kali177.
Kali Inside VirtualBox• Upon starting up VirtualBox, select “New” (Machine ->
New).
178.
Kali Inside VirtualBoxThe next screen is “Name and operating system” which is where you name the
VM.
179.
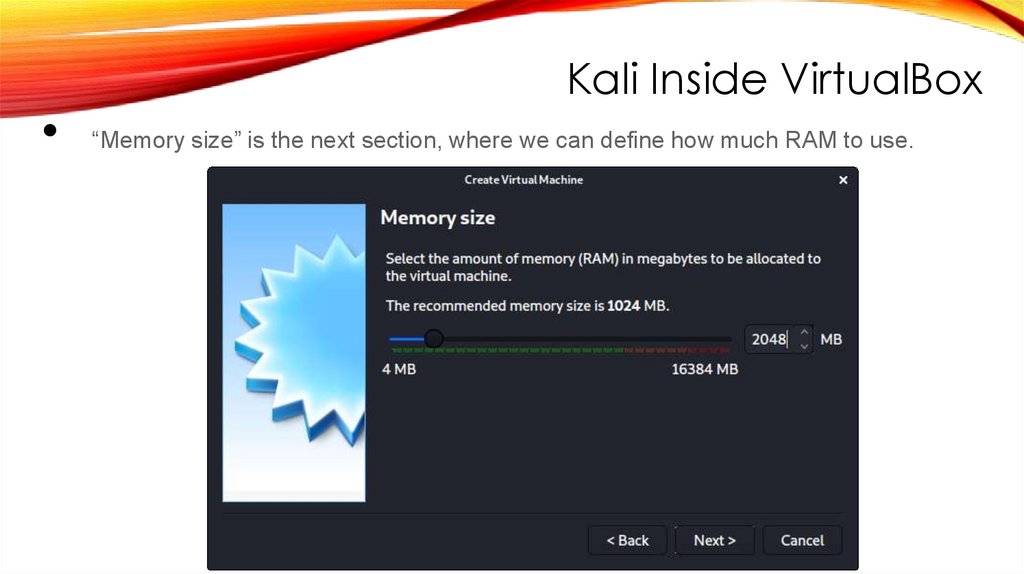
Kali Inside VirtualBox• “Memory size” is the next section, where we can define how much RAM to use.
180.
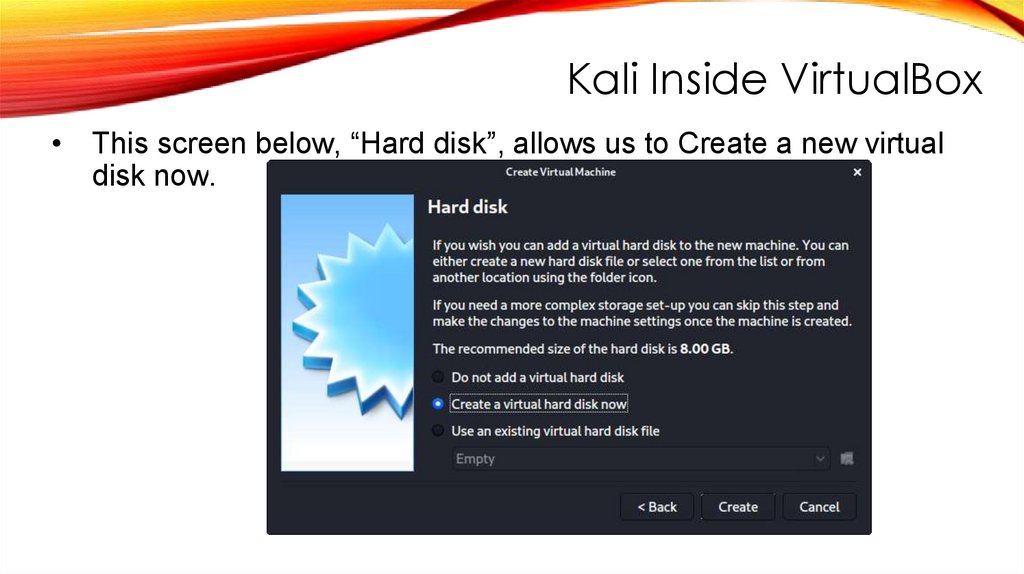
Kali Inside VirtualBoxThis screen below, “Hard disk”, allows us to Create a new virtual
disk now.
181.
Kali Inside VirtualBoxFor the “Hard disk file type”, we select VDI (VirtualBox Disk Image)
182.
Kali Inside VirtualBoxFor the following screen, “Storage on physical hard disk”, we go with the
default option of Dynamically allocated.
183.
Kali Inside VirtualBoxNow with “File location and size”, we can now define how large the virtual hard
disk will be.
184.
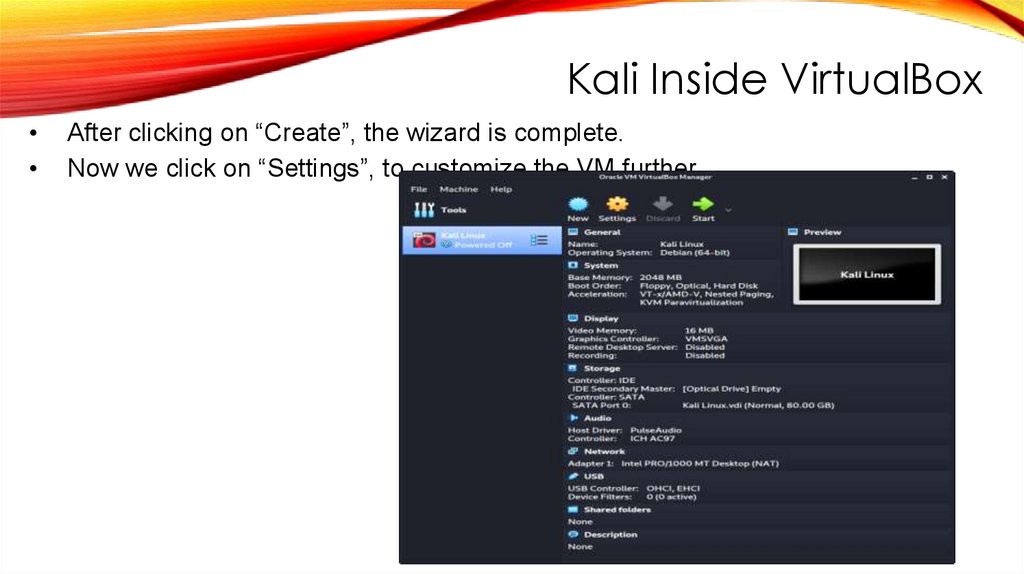
Kali Inside VirtualBoxAfter clicking on “Create”, the wizard is complete.
Now we click on “Settings”, to customize the VM further.
185.
Kali Inside VirtualBoxIn “General” -> “Advanced”, we make sure to set “Shared Clipboard” to
bidirectional, as well as “Drag’n’Drop” to bidirectional
186.
Kali Inside VirtualBoxIn “System” -> “Motherboard”, we change the “Boot Order” to make sure Hard
Disk is top and Optical is the second. Everything else is disabled.
187.
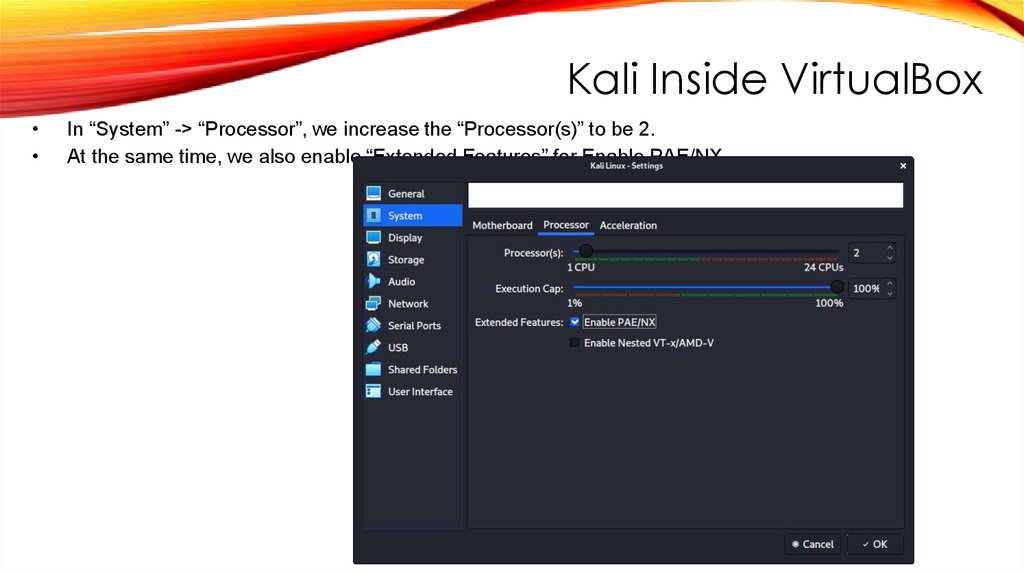
Kali Inside VirtualBoxIn “System” -> “Processor”, we increase the “Processor(s)” to be 2.
At the same time, we also enable “Extended Features” for Enable PAE/NX.
188.
Kali Inside VirtualBoxIn “Display” -> “Screen”, we make sure to have “Video Memory” set to 128 MB
Another item to point out is to make sure that “Accelerated 3D graphics” is disabled, as people have
reported that causes issues.
189.
Kali Inside VirtualBoxWhen we are ready to go, press “Start”.
The first time we run it, we will get a prompt saying do we wish to mount an image to use as a “startup disk”.
190.
Kali Inside VirtualBoxA new pop up will open, “Optical Disk Selector”. We will now press “Add”, then
navigate to where our ISO is located.
191.
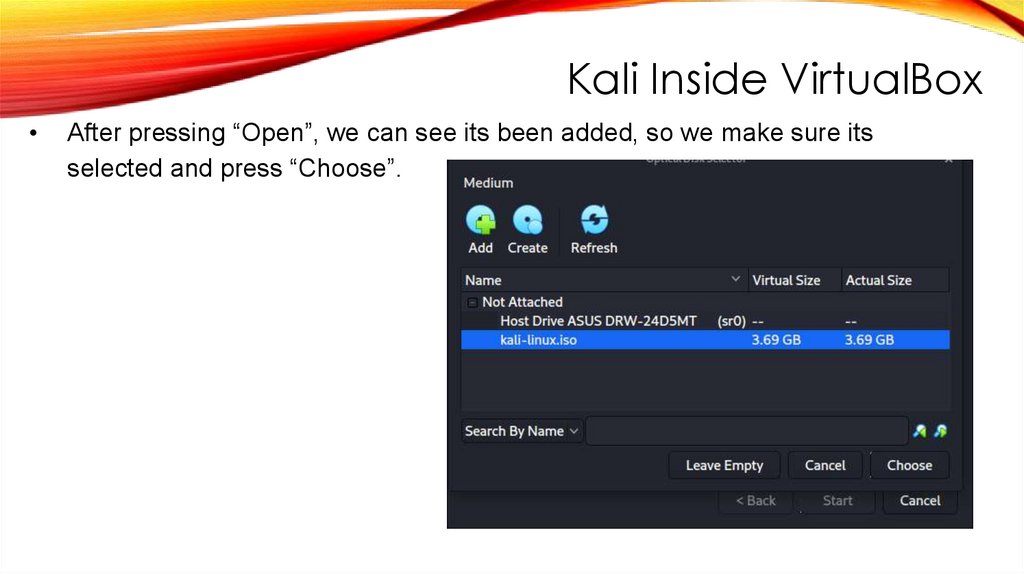
Kali Inside VirtualBoxAfter pressing “Open”, we can see its been added, so we make sure its
selected and press “Choose”.
192.
Kali Inside VirtualBoxAll that is left now to do is press “Start”.
193.
Kali Inside VirtualBox194.
Kali Inside VirtualBox195.
Kali Inside VirtualBox196.
Kali Inside VirtualBox197.
Kali Inside VirtualBox198.
Kali Inside VirtualBox199.
Kali Inside VirtualBox200.
Kali Inside VirtualBox201.
Kali Inside VirtualBox202.
Kali Inside VirtualBox203.
Kali Inside VirtualBox204.
Kali Inside VirtualBox205.
Kali Inside VirtualBox206.
Kali Inside VirtualBox207.
Kali Inside VirtualBox208.
Kali Inside VirtualBox209.
Kali Inside VirtualBox210.
Kali Inside VirtualBox211.
Kali Inside VirtualBox212.
Kali Inside VirtualBox213.
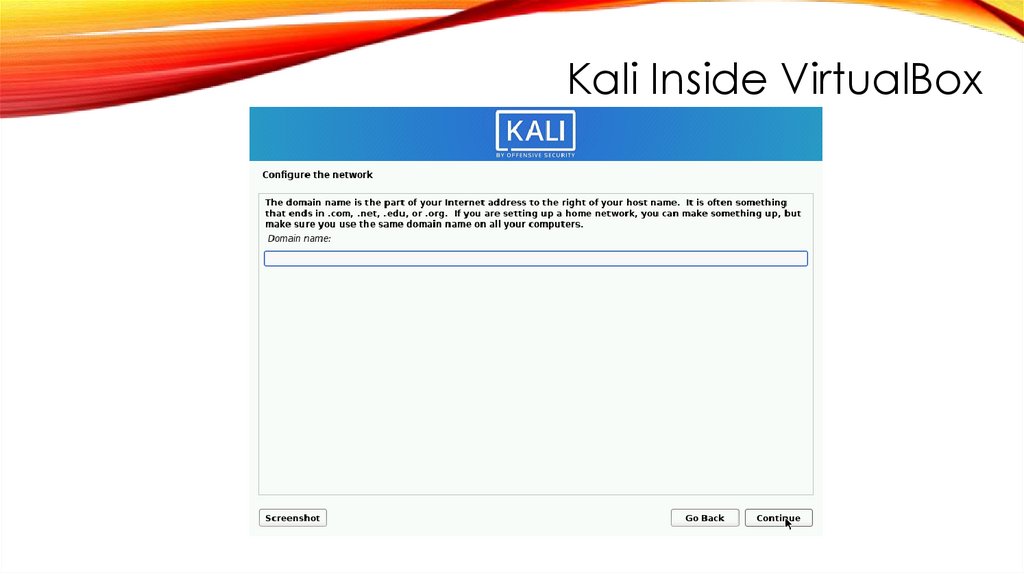
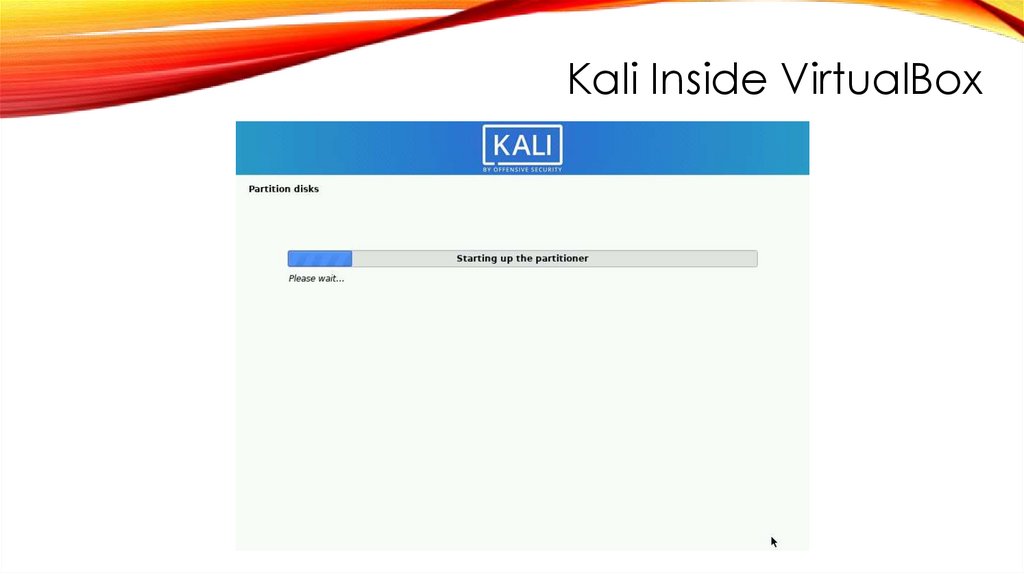
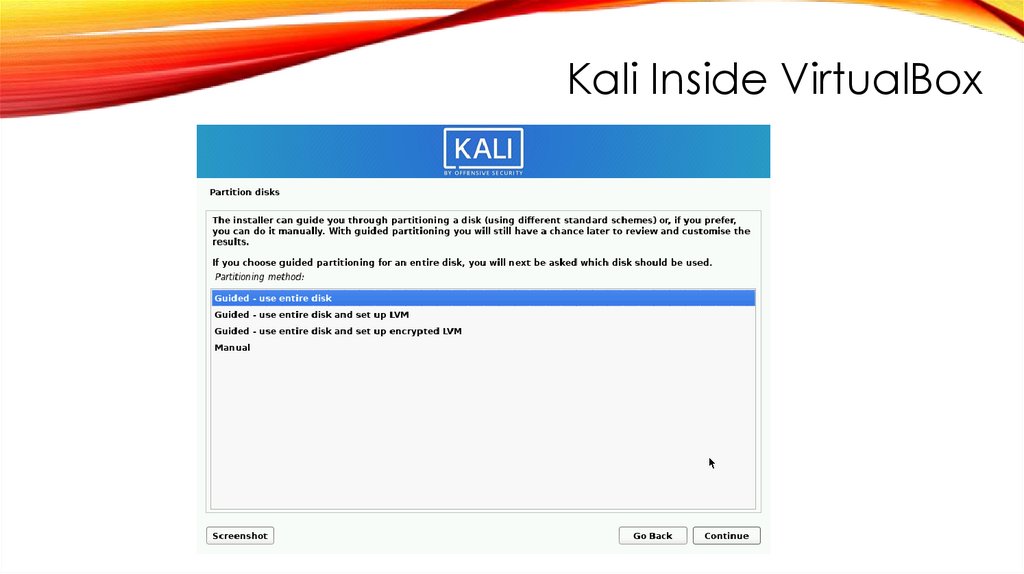
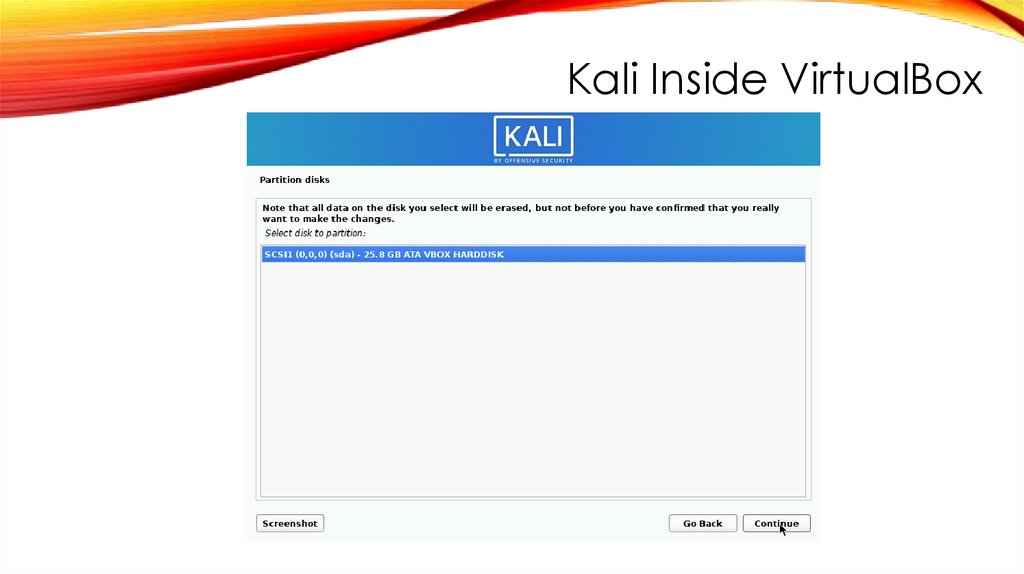
Kali Inside VirtualBox214.
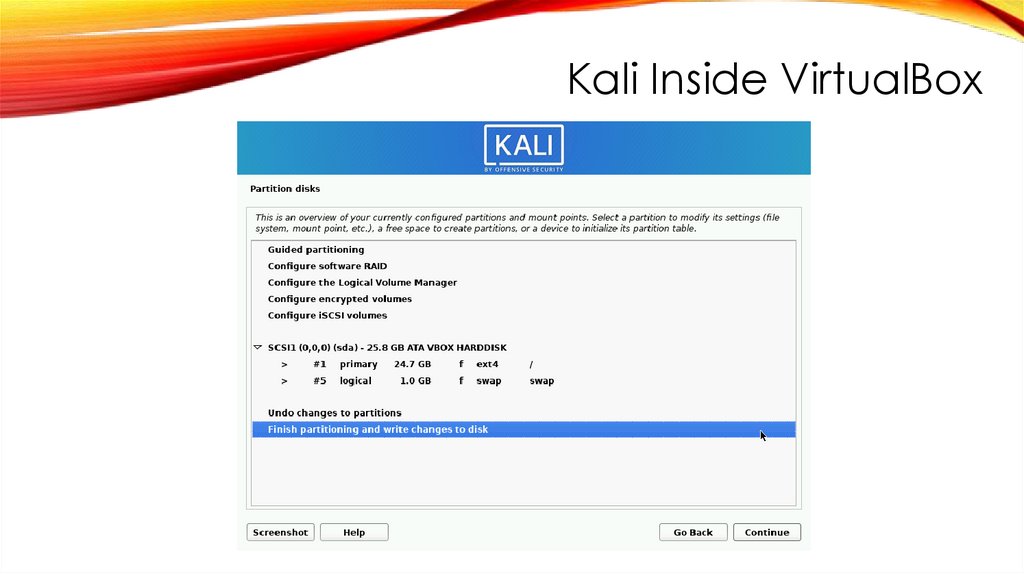
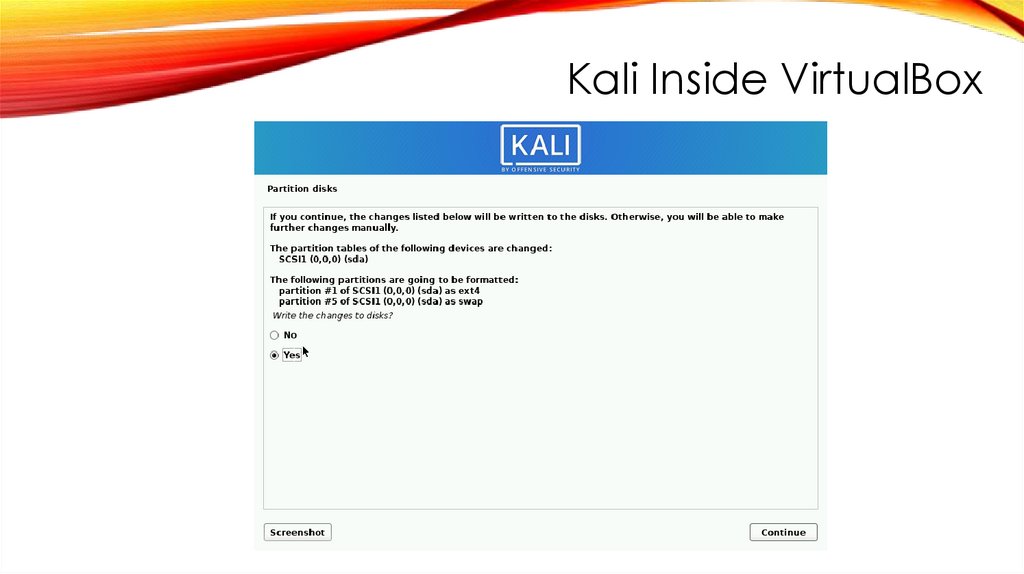
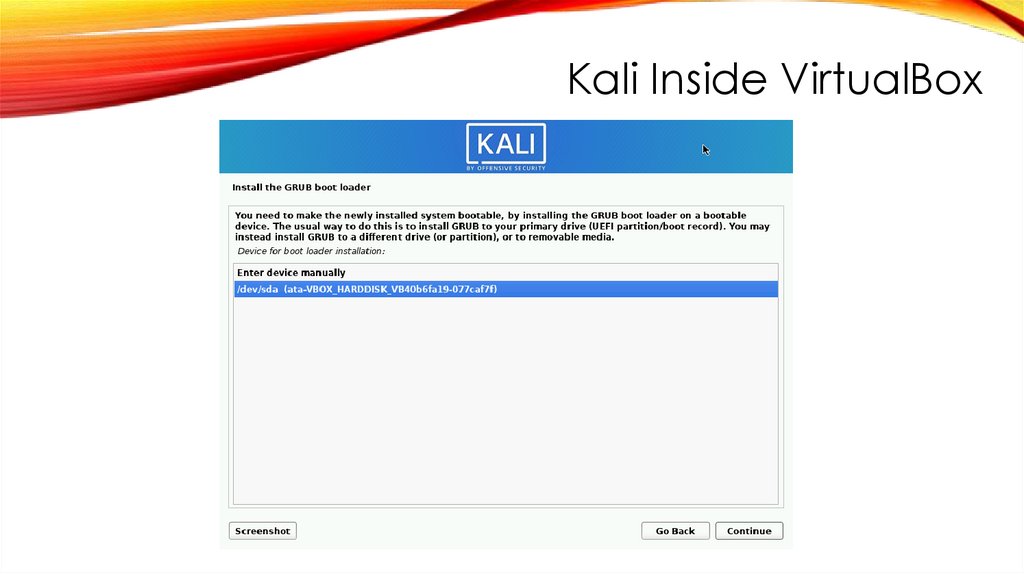
Kali Inside VirtualBoxINSTALL GRUB BOOT LOADER
FINISH INSTALLATION



















































































































































































 informatics
informatics








