Similar presentations:
TD – 3. C4I enabling technologies
1.
TD – 3C4I ENABLING
TECHNOLOGIES
2.
QUESTION NO 1What do you understand of C4I enabling
technologies? Why it is important to
have the basic understanding of these
technologies?
3.
C4I ENABLING TECHNOLOGIESC4I enabling technologies are computer hardware,
software and their standards, specifications and
fabrication methodologies used in building C4I
architectures / systems.
Previous generations of C4I Systems were built
using enabling technologies either owned by
government known as GOTS (Government Off The
Shelf) or belonged to specialized vendors termed
as proprietary.
4.
C4I ENABLING TECHNOLOGIESDetails of such technologies were not shared in
open / disclosed to public. This made it difficult to
integrate such disparate (dissimilar) systems with
each other. As a result, those systems were less
effective
during
combined
operations.
High
maintenance cost was also an issue with them.
5.
C4I ENABLING TECHNOLOGIESComputers
and
other
gadgetry
commercially
available now a days in the open market, known as
COTS (Commercial Off The Shelf), have gone so
advanced that these can effectively be used in
building potent C4I systems. Such systems cost
less and can easily be customised to make them
inter-operable. The contemporary armies have
successfully improved their C4I systems based on
these technologies.
6.
C4I ENABLING TECHNOLOGIESCareful
selection
of
available
C4I
enabling
technologies, both COTS and GOTS, can bring
about the desired interoperability between C4I sub
systems. In addition, this apch is expected to
reduce the existing large inventory of eqpt to
maintain. We, being in the stage of catching up
with other contemporary armies, should also use
these technologies in an org manner and dev such
systems to sp our C2 effectively and indigenously.
7.
C4I ENABLING TECHNOLOGIESConcentrating on these technologies will also
enable us to further improve our systems to
survive in the future environments of Network
Centric Warfare (NCW). Therefore, it is important
to have basic understanding of C4I enabling
technologies.
8.
QUESTION NO 2Briefly describe the C4I
Architecture Framework?
What is the main purpose of
its introduction?
9.
C4I ARCHITECTURE FRAMEWORKC4I Architecture Framework is enforced at national
level to ensure that C4I Systems / Architectures being
developed are compatible with in Army echelons and
across joint services. The Framework provides the
rules
and
guidance
for
developing
unified
C4I
Architecture Products (graphical, textual and tabular
applications those are developed in the course of
building a requisite C4I System).
10.
C4I ARCHITECTURE FRAMEWORKC4I Sub Systems developed prior to the year 2000 were
inefficiently interfaced with each other. Besides, many
common functions (writing orders and marking overlays
using digital maps etc) built in them were in different
formats. It was due to the absence of a defined coord apch
in their dev. This was complicating the overall C2
processing. That is why such systems were mostly
proprietary and extremely expensive. The application of
C4I Architecture Framework, afterwards, streamlined the
production and enabled building of interoperable and costeffective military systems
11.
C4I ARCHITECTURE FRAMEWORK12.
PURPOSE OF ARCHITECTURE FRAMEWORKIntroduction
enabled
the
of
C4I
Architecture
Framework
efficient
engineering
of
warrior
systems. The ultimate purpose of the framework is
to
improve
C4I
capabilities
with
sound
investments leading to rapid employment of
improved operational capabilities.
13.
QUESTION NO 3What are the guiding principles for
building C4I Systems compliant with
C4I Architecture Framework? Give
their brief description.
14.
GUIDING PRINCIPLESArchitectures should be built with a purpose in
mind
Architectures
should
facilitate,
not
impede,
communication among humans
Architectures should be relatable, comparable and
integrate-able (within Army and between all TriServices)
Architectures should be modular, reusable and
recompose-able
15.
GUIDING PRINCIPLESArchitectures should be Built with a Purpose in Mind.
Having a specific and commonly understood purpose
before starting to build architecture greatly increases
the efficiency of the effort and the utility of the
resulting architecture. The purpose determines how
wide the scope needs to be, which characteristics
need to be captured and what timeframes need to be
considered.
16.
GUIDING PRINCIPLESArchitectures should Facilitate, not Impede, Comm
among Humans. Architectures must be structured in a
way that allows humans to understand them quickly
and that guides the human thinking process in
discovering, analyzing and resolving issues. This
means
that
unnecessary
information
must
be
excluded and common terms / definitions be used in
an appropriate format.
17.
GUIDING PRINCIPLESArchitectures should be Relatable, Comparable and
Integrate-able. This principle requires that a common
set of architectural “building blocks” is used as the
basis for architecture descriptions. It applies equally
to the development of the architecture as a whole or
its portion and even to the groups of architectures
(within Army and between all Tri-Services). It also
requires the use of common terms and definitions.
18.
GUIDING PRINCIPLESArchitectures should be Modular, Reusable and
Recompose-able. Architecture representations should
consist of separate but related pieces that can be
recombined with a minimum amount of tailoring so
that they can be used for multiple purposes.
19.
QUESTION NO 4Briefly describe the C4I Core
Architecture Data Model
(CADM)?
20.
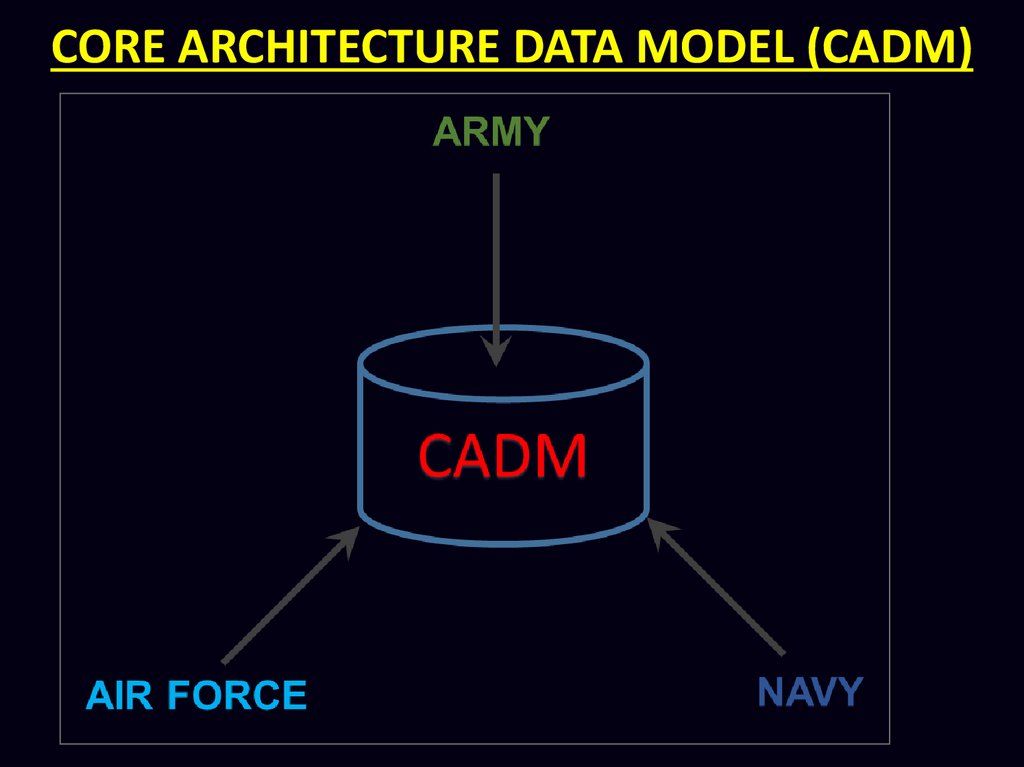
CORE ARCHITECTURE DATA MODEL (CADM)Gen. CADM is a guide to organizing and storing info in
C4I systems. It is aimed at providing a common
database
structure
for
repositories
(storage)
architecture products across the entire DoD.
of
21.
CORE ARCHITECTURE DATA MODEL (CADM)Backgr. Prior to
adopting
the
C4I Architecture
framework as guidance for creating C4I products,
each sub sys had its own data structure to store info.
Similarly, mil svcs and other def agencies have been
using different methodologies for dev and describing
their respective info storages. This made it difficult for
the architects / sys developers to exchange info within
and between such isolated architectures. As a result,
requisite interoperability was still missing between
those systems.
22.
CORE ARCHITECTURE DATA MODEL (CADM)Common Approach. With the growing emphasis on
combined / joint operations, interoperability between
C4I Systems became highly desirable. For which, in
addition to adopting unified enabling technologies,
some common approach was also required for
organizing the structure of information. This led to the
bases of developing a unified design of database;
named as CADM – The Core Architecture Data Model.
23.
CORE ARCHITECTURE DATA MODEL (CADM)24.
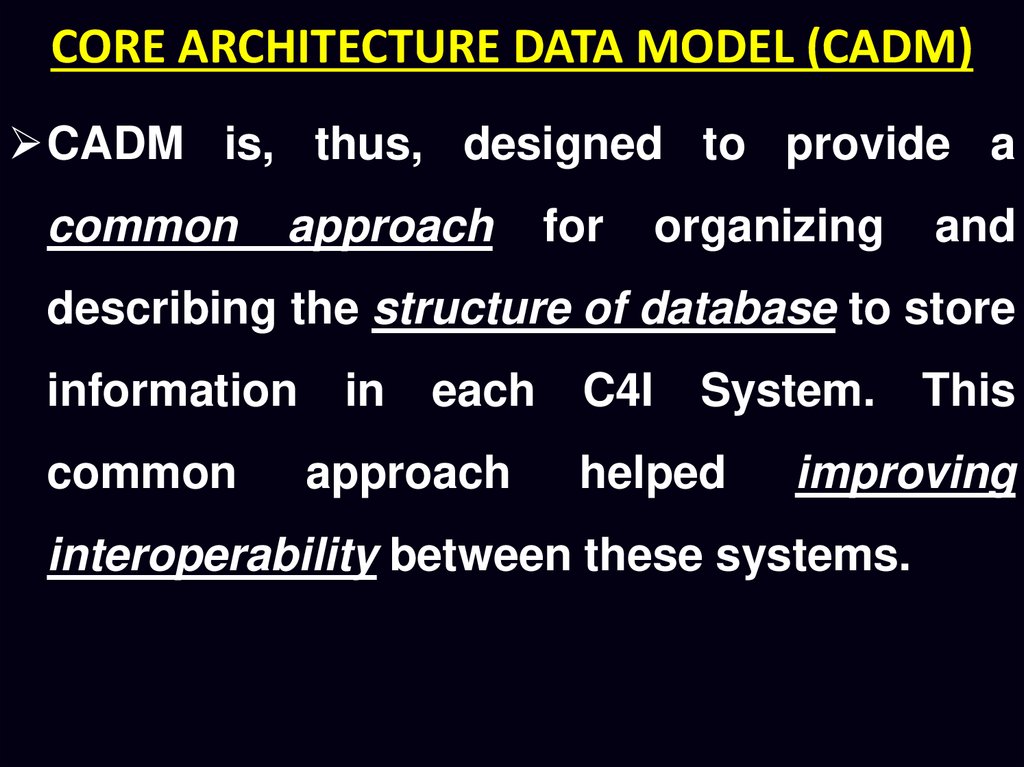
CORE ARCHITECTURE DATA MODEL (CADM)CADM is, thus, designed to provide a
common
approach
for
organizing
and
describing the structure of database to store
information
common
in
each
approach
C4I
System.
helped
This
improving
interoperability between these systems.
25.
QUESTION NO 5What are the Mission
Environments? Also describe
the Computing Environments in
relationship with the Mission
Environments?
26.
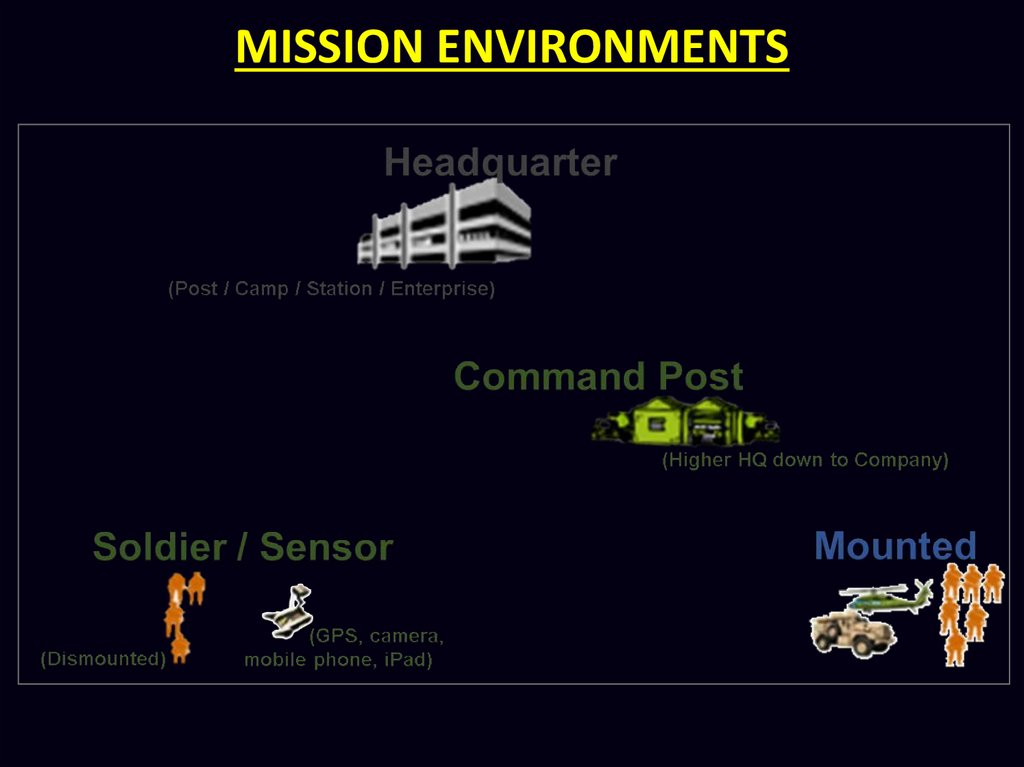
MISSION ENVIRONMENTSMsn Environments are those in which the soldiers
op. These may be a HQ (in case of US Army a Post
/ Camp / Station / Enterprise) loc at depth or inside
a cantt, a CP (of a higher HQ down to Coy) estb in
the fd, soldiers Mounted in some veh like jeep / hel
and a Soldier / Sensor either dismounted or depl
in the fd. Each msn environment has different req
of network bandwidth, hardware size / wt, electric
power, environmental con and loc permanence.
27.
MISSION ENVIRONMENTS28.
COMPUTING ENVIRONMENTSAre the server(s), clients, mobiles, sensors and
platforms that provide needed cap to the soldiers
to op in their respective Mission Environments.
Each Computing Environment comprises different
hardware and applications (e-mail, chat, browser,
document viewer or presentation editor etc) to
comply with the requisite capability associated
with it.
29.
COMPUTING ENVIRONMENTS30.
QUESTION NO 6Describe the characteristics of
each Computing Environment?
31.
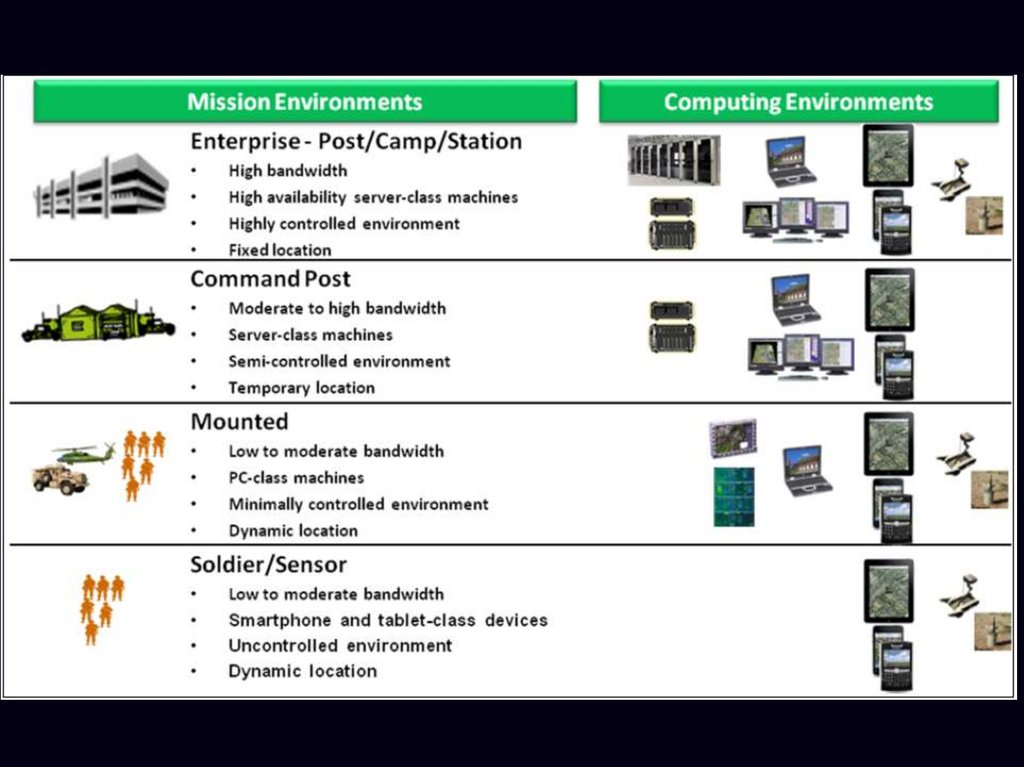
CHARACTERISTICS OF COMPUTING ENVIRONMENTEnterprise Server. The Enterprise Server environment
is
a
high-bandwidth
networked
server-class
computing and environmental support which is
capable of operating enterprise-scale applications and
data center services. Higher headquarters / stations
generally operate in these environments.
32.
CHARACTERISTICS OF COMPUTING ENVIRONMENTTactical Server and Client. It is an environment of
transportable
server-class
hardware
paired
with
powerful client workstations connected by a generally
reliable network (with moderate to high bandwidth)
located in command posts. It allows command post
mission environment users and systems to leverage
capabilities offered by the enterprise, as well as to
operate robust capabilities locally. The Clients may
comprise computers, laptops or dumb terminals (Thin
Clients) connected to the tactical servers.
33.
CHARACTERISTICS OF COMPUTING ENVIRONMENTMobile.
These
are
small
handheld
devices
(Smartphone, iPad etc) and technologies for the
mobile computing environment. The devices are often
based
on
lightweight
commercial-off-the-shelf
technology.
Sensors. These are specialized, human-controlled or
unattended computing environments. Sensors are
organized
surveillance
by
family
and
(material
radars
characteristics and capabilities.
etc)
detection,
with
video
different
34.
CHARACTERISTICS OF COMPUTING ENVIRONMENTPlatform (Ground and Air).
It is a reduced network
computing environment with reduced equipment in
size,
weight
and
power
tailored
to
meet
the
requirements of supported platform (jeep, tank and
helicopter etc).
35.
36.
QUESTION NO 7What do you understand about
the
Common
Operating
Environment (COE) with reference
to the enabling technologies? Give
an example of COE to include some
of the services and standards for
Clients Computing Environment?
37.
COMMON OPERATING ENVIRONMENT (COE)COE is an approved set of Computing Technologies
and Standards that enable secure and interoperable
applications to be developed and executed rapidly
across a variety of Computing Environments. Each
computing environment has a minimum standard
configuration that supports the Army‘s ability to
produce and deploy quickly high-quality applications.
This also reduces the complexities of configuration,
maintenance
support
and
training
associated with these environments.
requirements
38.
COMMON OPERATING ENVIRONMENT (COE)Before 2010, Army apch to info / IT implementation
and mgmt was cumbersome and inadequate to keep
up with the pace of change. Based on functional reqs,
program managers have been individually choosing &
fielding hardware platforms & software infrastructures
to del cap for a specific cbt or business function.
39.
COMMON OPERATING ENVIRONMENT (COE)Meanwhile, to sp ongoing conflicts where requisite
systems
were
not
aval,
the
Army
combatant
commanders have been independently procuring
commercially aval solutions; often installing and
customizing them in B fd.
As a result, depl units
frequently must plan and execute their ops using
multiple computer systems with different hardware,
operating
systems,
databases
and
security
configurations. This complex integration raised cost,
dec interoperability and inc network security risk.
40.
COMMON OPERATING ENVIRONMENT (COE)The intent of the COE is to normalize the computing
environment and achieve a balance between ongoing
unconstrained innovation and standardization. As a
result, developers will be able to produce high-quality
applications quickly and cheaply, improve security
and reduce maintenance cost by avoiding the existing
complexities of maintaining host of multiple computer
systems.
41.
COMMON OPERATING ENVIRONMENT (COE)42.
COMMON OPERATING ENVIRONMENT (COE)C4I
Systems
developed
using
services
and
standards approved under COE will provide
requisite interoperability within and between all
Computing environments. This in turn will give the
requisite synergy, i.e. every component talking to
every other component in the battlefield, to
operate in future NCW Mission Environments.
43.
QUESTION NO 8What are the principal guidelines
for the selection of COE for the
variety of Computing
Environments?
44.
COE GUIDELINESCOE is Standards-Based. Applications and application
components should adhere to Army / DoD standard
naming conventions, reside in common libraries and
be deployed using standard release-management
processes.
45.
COE GUIDELINESCOE should use DoD/Army-Mandated Applications and
Stds. To inc integration, enterprise-sel applications & stds
should be the default. Non uniformity of software may
cause incompatibility within the computing environment.
COE to leverage DoD and Army-mandated products to the
max extent possible. For example, MS Windows, Office,
Sharepoint, Exch and Active Directory etc are the software
applications and standards offered from MS Microsoft to
provide office functionality. Same may always be used
wherever such functionality is needed.
46.
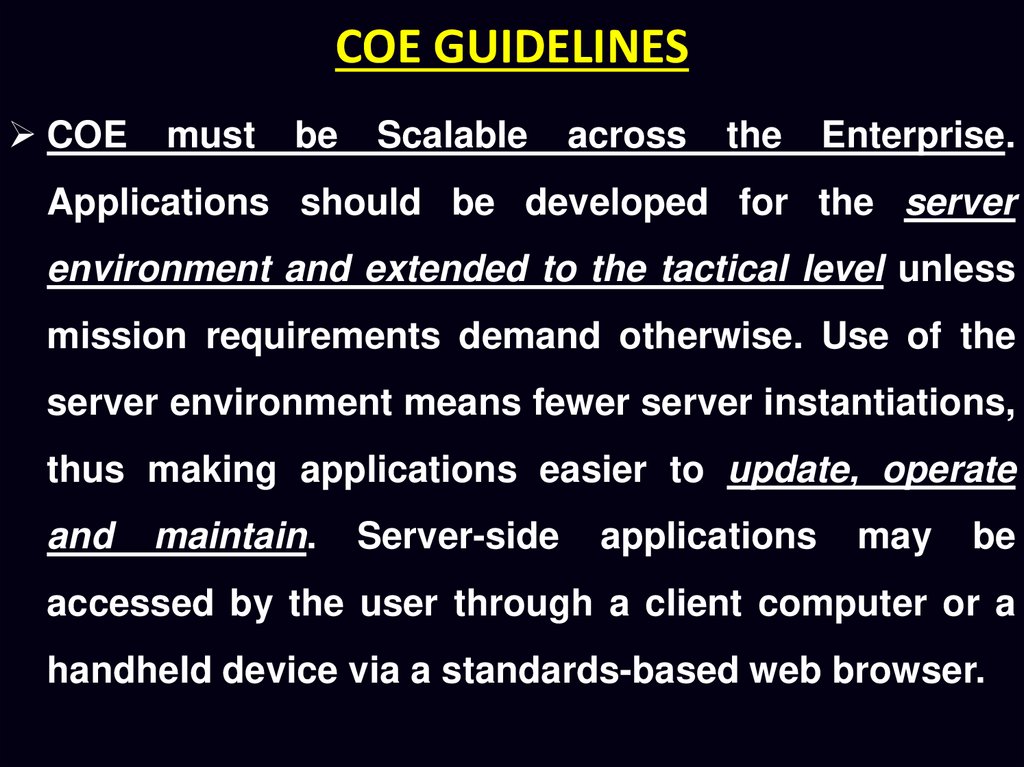
COE GUIDELINESCOE
must
be
Scalable
across
the
Enterprise.
Applications should be developed for the server
environment and extended to the tactical level unless
mission requirements demand otherwise. Use of the
server environment means fewer server instantiations,
thus making applications easier to update, operate
and
maintain.
Server-side
applications
may
be
accessed by the user through a client computer or a
handheld device via a standards-based web browser.
47.
COE GUIDELINESCOE Defaults to COTS Solutions. COE should
leverage Commercial-Off-The-Shelf (COTS) software
(e.g. MS Office, Adobe Reader and ArcGIS etc.) and
other commercial capabilities first, including open
source solutions available in the IT Market. The
objective
is
to
leverage
market-leading
COTS
technologies to the fullest extent possible for militaryspecific needs. Reuse of existing packages should be
exploited where possible.
48.
COE GUIDELINESCOE must Remain Relevant. Emerging commercial
technologies should be continually assessed for
inclusion in the COE. Similarly, current technologies
that are obsolete or no longer relevant should be
retired. The COE may be validated and republished
twice a year.









































 software
software








