Similar presentations:
WEEK 6___Lesson 1-2_FL2
1. WEEK 6 LESSONS 1-2 Module 3: Intelligent, Immersive and Decentralized Technologies
FOREIGN LANGUAGE 2WEEK 6
LESSONS 1-2
Module 3: Intelligent, Immersive
and Decentralized Technologies
2026
School of GED
Astana IT University
2. Outline
ReadingWriting
3. Objectives
• Understand key concepts related to centralised and decentralisedidentity management
• Synthesize causes and effects of technological developments in
identity management
• Practice academic writing skills in a cause–effect structure
• Apply new vocabulary in both discussion and written tasks
4. Warm-up (5 min)
Which platform would you trust with yourdigital identity? Why?
5.
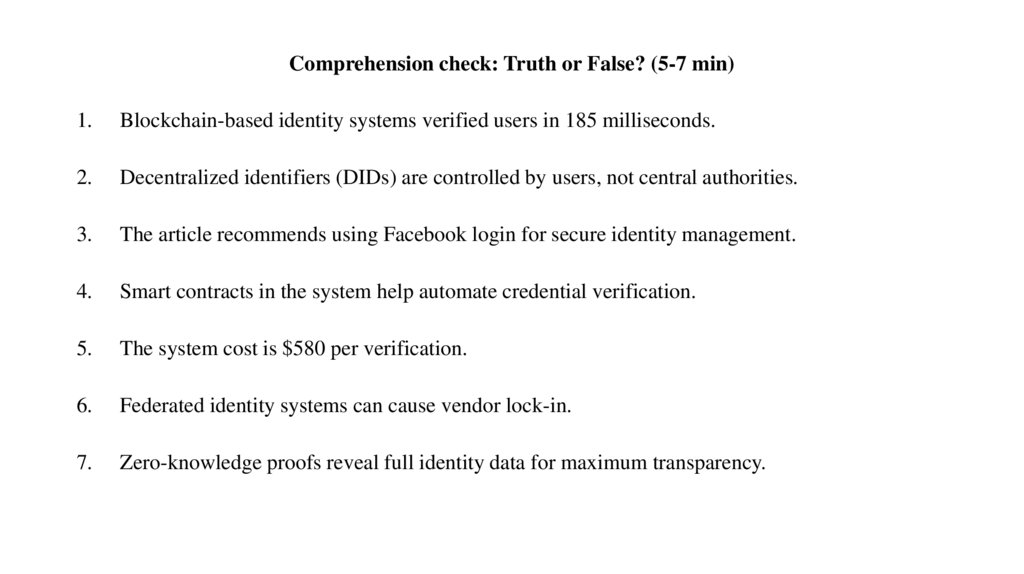
Comprehension check: Truth or False? (5-7 min)1.
Blockchain-based identity systems verified users in 185 milliseconds.
2.
Decentralized identifiers (DIDs) are controlled by users, not central authorities.
3.
The article recommends using Facebook login for secure identity management.
4.
Smart contracts in the system help automate credential verification.
5.
The system cost is $580 per verification.
6.
Federated identity systems can cause vendor lock-in.
7.
Zero-knowledge proofs reveal full identity data for maximum transparency.
6.
Task 1. Complete the summary with the given words in the table (10-13 min)In today's digital world, identity verification is
essential for accessing everything from banking to healthcare.
However, traditional systems of (1) __________ rely heavily
on centralized authorities like governments or tech companies.
This centralization creates (2) __________, meaning that one
breach can compromise millions of users. It also tends to (3)
__________ outdated models where users lack control over
their data.
Another challenge with existing models such as (4)
__________ is their reliance on third-party providers. This
often leads to (5) __________, where users are locked into
specific platforms and cannot move their credentials easily.
Additionally, these systems frequently (6) __________,
making it difficult to create seamless digital experiences across
platforms or regions. Because of these issues, many experts are
advocating for (7) __________, also known as SSI. This
approach empowers users to control their own identities
through (8) __________ that are anchored on blockchains.
These identifiers, stored on (9) __________, are secure,
private, and cannot be tampered with.
Distributed ledgers
Perpetuate
Decentralized identifiers
Operate in silos
Centralized identity management
Decentralized identity management
Single points of failure
Vendor lock-in
Federated identity
SSI (self-sovereign identity)
7.
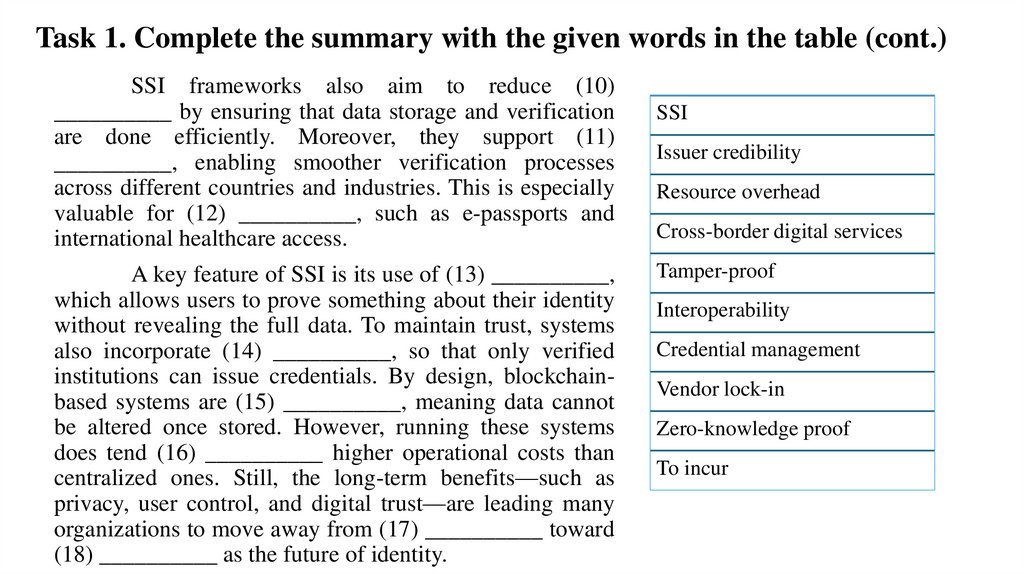
Task 1. Complete the summary with the given words in the table (cont.)SSI frameworks also aim to reduce (10)
__________ by ensuring that data storage and verification
are done efficiently. Moreover, they support (11)
__________, enabling smoother verification processes
across different countries and industries. This is especially
valuable for (12) __________, such as e-passports and
international healthcare access.
A key feature of SSI is its use of (13) __________,
which allows users to prove something about their identity
without revealing the full data. To maintain trust, systems
also incorporate (14) __________, so that only verified
institutions can issue credentials. By design, blockchainbased systems are (15) __________, meaning data cannot
be altered once stored. However, running these systems
does tend (16) __________ higher operational costs than
centralized ones. Still, the long-term benefits—such as
privacy, user control, and digital trust—are leading many
organizations to move away from (17) __________ toward
(18) __________ as the future of identity.
SSI
Issuer credibility
Resource overhead
Cross-border digital services
Tamper-proof
Interoperability
Credential management
Vendor lock-in
Zero-knowledge proof
To incur
8. Task 2. Cause and Effect Hunt (10 min)
1. Distribute handouts with excerpts from the article to eachpair/group.
2. In pairs/groups, students underline cause-effect sentences and
rewrite them with arrows (→).
Example: The use of blockchain’s DLT → makes the process more
transparent.
Students then discuss:
1. Which causes are technological (e.g., encryption, DLT)?
2. Which effects are social or ethical (e.g., privacy, user control)?
9. Task 3. Writing: critical synthesis (20 min)
Analyse author’s perspective with in-text citations following thesandwich method:
Step 1: Identify how the authors explain the cause for the rise of
decentralised identity management.
Step 2: Summarise what effects they predict decentralised systems
might have in the future.
Step 3: Do you agree with the authors’ stance/perspective? Why / why
not? Share your responses/thoughts in pairs.
Source: K. Samunnisa, 2Sunil Vijaya Kumar Gaddam, Synth. Multidiscip. Res. J., 1(2) 22-29, 2023
10. Cause → Effect (Showing reasons and results)
• The main reason for this is…• One factor that explains this is…
• This can be explained by…
• This is due to…
• Due to this,…
• Consequently,…
• For this reason,…
• In consequence,…
• This arises from…
• This may lead to…
• This can contribute to…
• This might cause…
• This may play a role in…
• This could potentially result in…
• As a result of X, Y occurs, which
in turn leads to Z.
• X influences Y, and this
subsequently affects Z.
• X is a determining factor in…
11. Task 4. TBA: real-world identity systems analysis (50 min)
Step 1. Each group chooses one real system or technology that involves identitymanagement: China RealDID, Moodle, e-Estonia, Digital Tenge etc. (5 min)
Step 2. Using what they learned from the reading on decentralised identity
management and in the Internet (Google Scholar or official sources), students
fill in the table on slide 14 (20 min).
Step 3. Students take the role of advisors to Kazakhstan’s Ministry of AI and
Digital Development. Using the article, they write a 3-paragraph policy memo
recommending how the country should approach identity management in the
next 5 years. Students then post their policy memo in MS Teams (20 min).
Step 4. Share your analysis results with the class (one speaker/presenter). (5 min
per group)
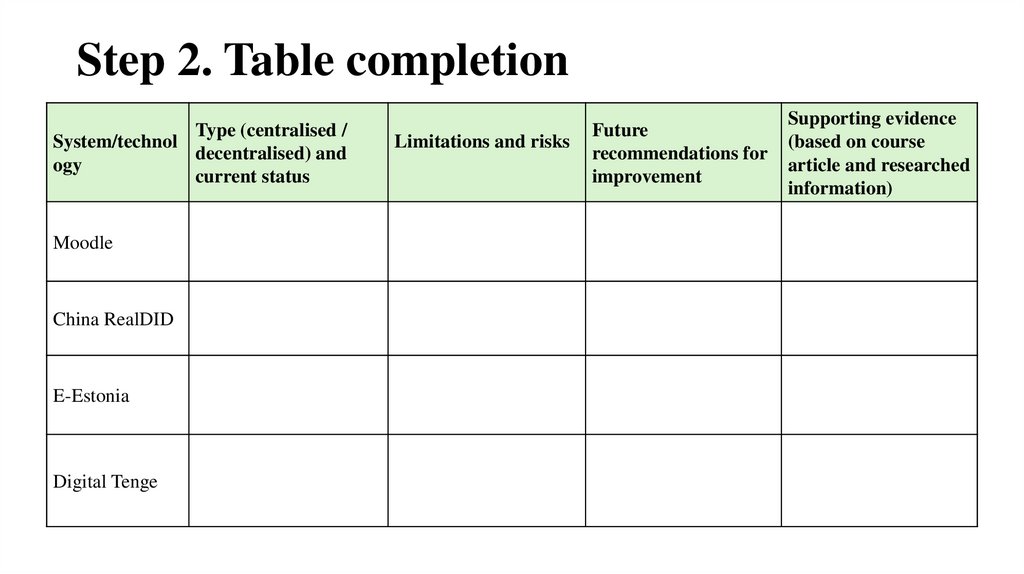
12. Step 2. Table completion
Type (centralised /System/technol
decentralised) and
ogy
current status
Moodle
China RealDID
E-Estonia
Digital Tenge
Limitations and risks
Future
recommendations for
improvement
Supporting evidence
(based on course
article and researched
information)
13.
Step 3. Policy memo recommendationsPolicy memo template
To: Ministry of AI and Digital Development
Subject: Future of Identity Management in Kazakhstan
Dear …,
Paragraph 1 - Current status of system/technology
Paragraph 2 - Limitations and risks to consider: cost, regulatory complexity, etc.
Paragraph 3 - Recommendation for improvement: (Based on evidence from the article, we
recommend...)
NB: Students must include supporting arguments in each paragraph above.
Kind regards,
…..
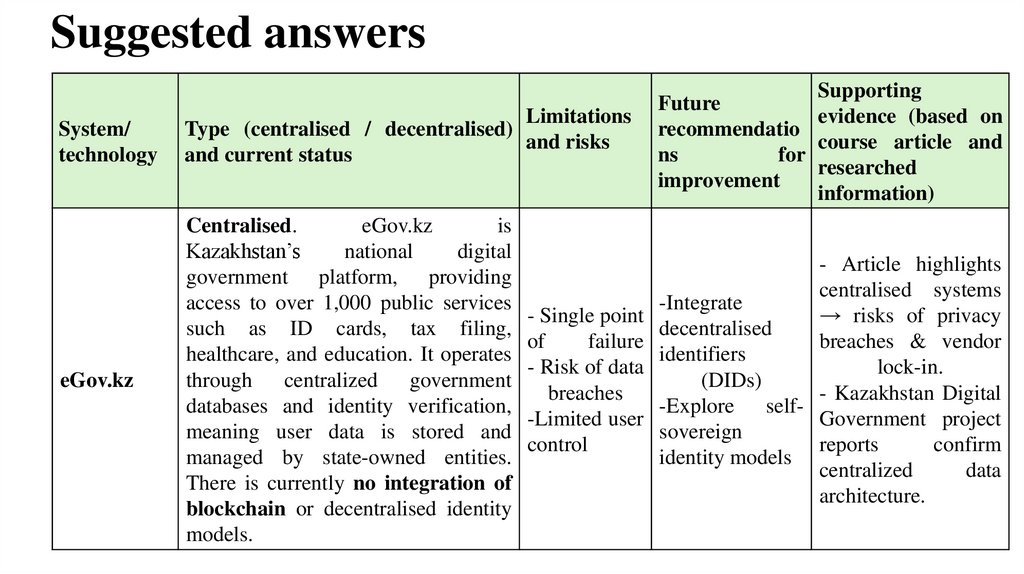
14. Suggested answers
System/technology
Limitations
Type (centralised / decentralised)
and risks
and current status
Supporting
Future
evidence (based on
recommendatio
course article and
ns
for
researched
improvement
information)
eGov.kz
Centralised.
eGov.kz
is
Kazakhstan’s
national
digital
government platform, providing
access to over 1,000 public services
such as ID cards, tax filing,
healthcare, and education. It operates
through centralized government
databases and identity verification,
meaning user data is stored and
managed by state-owned entities.
There is currently no integration of
blockchain or decentralised identity
models.
- Article highlights
centralised systems
-Integrate
→ risks of privacy
decentralised
breaches & vendor
identifiers
lock-in.
(DIDs)
- Kazakhstan Digital
-Explore selfGovernment project
sovereign
reports
confirm
identity models
centralized
data
architecture.
- Single point
of
failure
- Risk of data
breaches
-Limited user
control
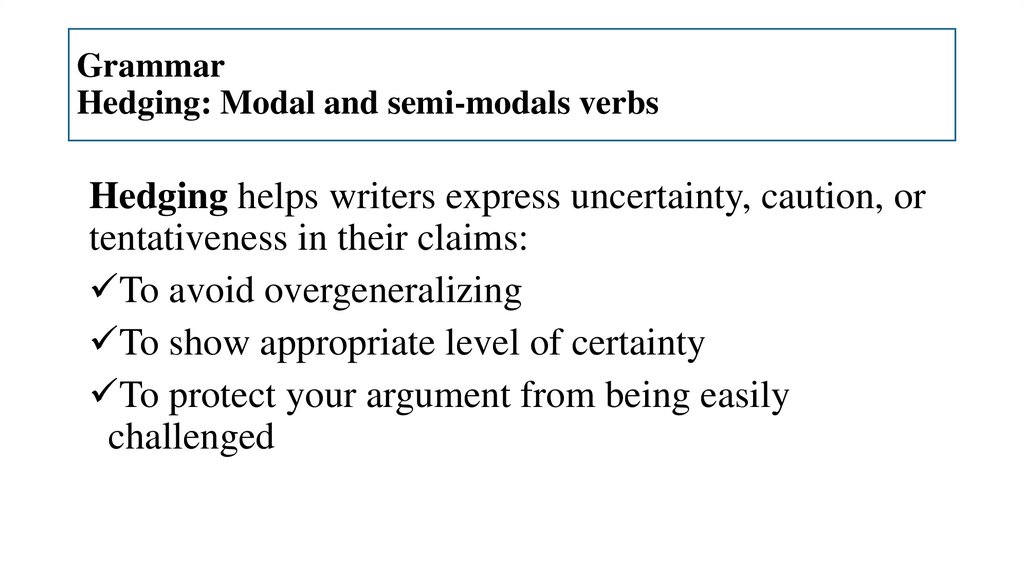
15. Grammar Hedging: Modal and semi-modals verbs
Hedging helps writers express uncertainty, caution, ortentativeness in their claims:
To avoid overgeneralizing
To show appropriate level of certainty
To protect your argument from being easily
challenged
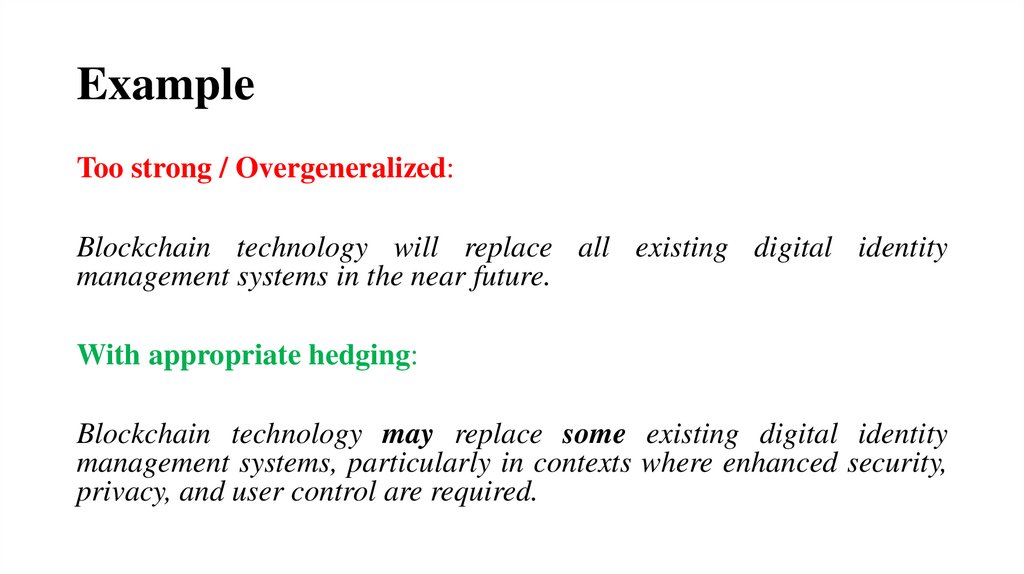
16. Example
Too strong / Overgeneralized:Blockchain technology will replace all existing digital identity
management systems in the near future.
With appropriate hedging:
Blockchain technology may replace some existing digital identity
management systems, particularly in contexts where enhanced security,
privacy, and user control are required.
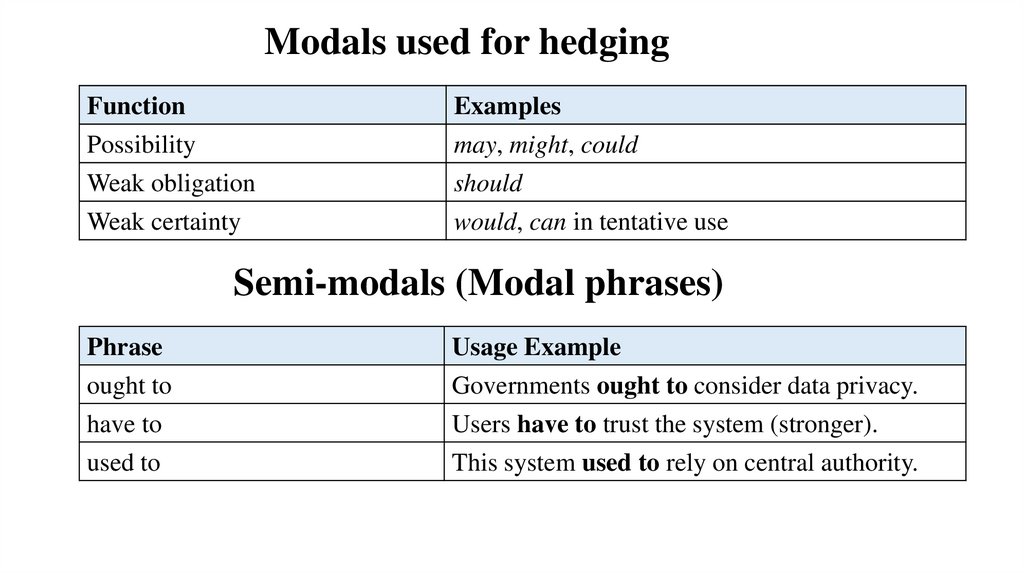
17. Modals used for hedging
FunctionPossibility
Weak obligation
Weak certainty
Examples
may, might, could
should
would, can in tentative use
Semi-modals (Modal phrases)
Phrase
ought to
have to
Usage Example
Governments ought to consider data privacy.
Users have to trust the system (stronger).
used to
This system used to rely on central authority.
18. Task 1
The following statements express ideas too strongly for academic writing.Rewrite each sentence using modal verbs or semi-modals to make the
claims more cautious and hedged.
1. Decentralized identity systems solve all privacy and security issues in
digital environments.
2. Governments will fully adopt blockchain-based identity management
systems within the next few years.
3. Users trust decentralized identity systems more than centralized ones.
19. References
Samunnisa, K., & Gaddam, S. V. K. (2023). Blockchain-baseddecentralized identity management for secure digital transactions.
Synthesis: A Multidisciplinary Research Journal, 1(2), 22–29.