Similar presentations:
Design of Web Application for Text Encryption and Decryption Using Blowfish Algorithm CS-2103
1.
Astana IT UniversityDesign of Web Application for
Text Encryption and
Decryption Using Blowfish
Algorithm
CS-2103
Aytzhan Araylym
Zhanaidarova Zhanel
Supervisor:
Gulnara Abitova
2.
Astana IT UniversityOutline
01 Aim
04 Relevance
02 Objective
05 Methodology
03 Novelty
06 Literature Review
3.
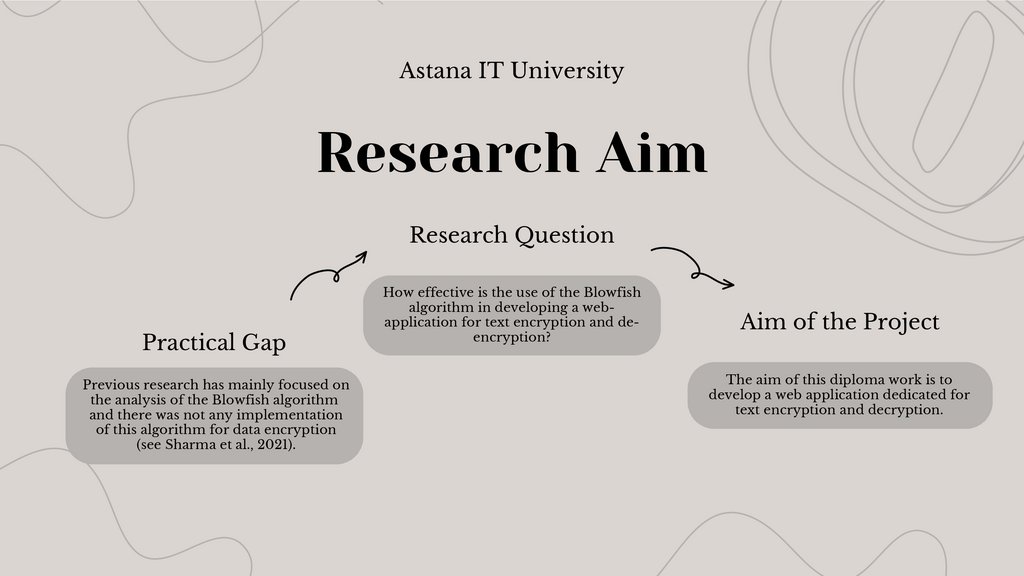
Astana IT UniversityResearch Aim
Research Question
Practical Gap
Previous research has mainly focused on
the analysis of the Blowfish algorithm
and there was not any implementation
of this algorithm for data encryption
(see Sharma et al., 2021).
How effective is the use of the Blowfish
algorithm in developing a webapplication for text encryption and deencryption?
Aim of the Project
The aim of this diploma work is to
develop a web application dedicated for
text encryption and decryption.
4.
Astana IT UniversityObjectives
In depth study of Blowfish algorithm
Development of User-Friendly Interface
Implement the Blowfish algorithm within the web
application
Perform comprehensive testing to evaluate the security
and efficiency of the application
5.
Astana IT UniversityNovelty
The novelty of this work lies in the development of the
web application to encrypt and decrypt text with the
Blowfish algorithm. The study will also implement a realtime encryption and decryption of text information which
is a unique feature and allows users to understand the
cryptographic processes.
6.
Astana IT UniversityRelevance
The importance of this diploma work lies in using the
Blowfish algorithm which is known for its security and speed
in encryption and decryption processes. Additionally, the
project offers educational significance by demonstrating
cryptography principles and the application of algorithms
like Blowfish. Students in the fields of cryptography and
information security can use it as a learning resource.
7.
Astana IT UniversityMethodology
Quantitative
1. Literature Review: A comprehensive
review of relevant literature, books,
research papers, and relevant
theoretical frameworks will be
conducted to determine the current
state of knowledge regarding the
Blowfish algorithm.
2. Analysis: Based on the literature review,
we will analyze the findings and
programming code of the Blowfish.
Qualitative
In order to assess the public's
awareness and understanding of
cryptographic methods, particularly
the Blowfish algorithm, a quantitative
survey will be conducted using Google
Forms. This method aimed to collect
structured data and numerical
measures regarding participants'
familiarity with various cryptographic
techniques.
8.
Astana IT UniversityLiterature Review
The insights from various researchers underscore the strengths and
weaknesses of the Blowfish algorithm in comparison to other
symmetric encryption methods. Its performance, as highlighted in
various studies, positions it favorably among its peers, especially in
terms of efficiency and security.
9.
Astana IT UniversityConclusion
In conclusion, this diploma work has aimed to create a web
application focused on text encryption and decryption. Focused
on the Blowfish algorithm, known for its secure measures and
efficiency, the project contributes significantly to the
advancement of cryptographic knowledge. In an increasingly
digitized world, where privacy and security are crucial concerns,
the project's objectives centered on developing a user-friendly
interface and integrating the Blowfish algorithm.
10.
Astana IT UniversityThank You For
Your Attention









 software
software








