Similar presentations:
Constructivism
1.
Constructivism2.
Final Exam12.17 – Same Classroom
4-5 Short answer essays
-2 Pages notes
Makeup Class: FRIDAY, 6:00pm
◦ Classroom TBD, will post on LMS
◦ Reivew
◦ If you cannot come on Friday Assignment on LMS
3.
Topics on the TestInternational Institutions
International Trade
◦ Sovereignty
◦ Membership, Scope of Issues, Centralization, Rules of
Control, Flexibility
◦ The United Nations
◦ Suasion game
◦ Production = Land+Labor+Capital
◦ Mercantilism v. Liberalism
◦ Comparative Advantage
◦ Flying Geese Model
◦ ISI v. EOI
International Law
Negotiation
◦ Sovereignty
◦ Differences between domestic and international law
◦ UNCLOS
◦ International Humanitarian Law (*4 principles)
◦ Negotiation Theory
◦ ZOPA, BANTA, Win Sets,
◦ Two Level Games
◦ Principal Agent Problems
Constructivism
◦ Norms
◦ Security Communities
◦ Securitization theory?
4.
Today’s LessonReview:
◦ Negotiation
◦ Two Level games
◦ IR Theory
Constructivism
◦ Assumptions of Constructivism
◦ Norms: The Norm Lifecycle
◦ Security Communities
◦ Securitization
5.
Review: NegotiationWhat is a win set?
What is a BANTA?
What is a ZOPA?
What were some of the
advantages/disadvantages in
negotiation?
What are Principal-Agent Problems
What are two level games?
6.
Review: International Relations TheoryREALISM
LIBERALISM
Humans/States are Selfish
Humans/States are cooperative
States are unitary Actors
States are made up of political and social
groups
States seek Power to secure Survival
International system is Anarchy
Incentives based on Domestic and
International Institutions
7.
How would aRealist understand
this dispute?
A Liberal?
8.
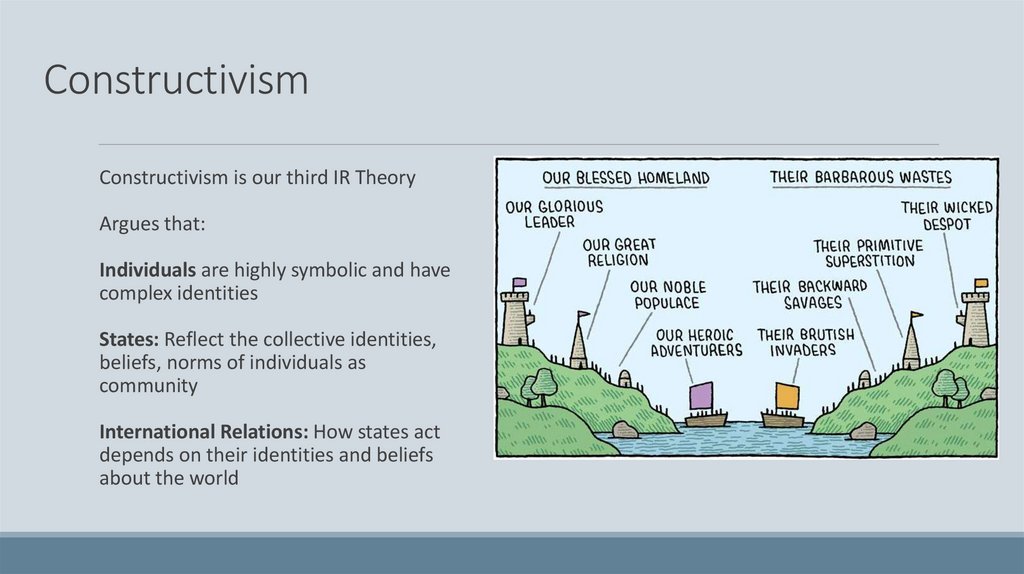
ConstructivismConstructivism is our third IR Theory
Argues that:
Individuals are highly symbolic and have
complex identities
States: Reflect the collective identities,
beliefs, norms of individuals as
community
International Relations: How states act
depends on their identities and beliefs
about the world
9.
Assumptions about Human NatureHuman beings are highly social and symbolic
(stories)
Their identities as individual and community are
created socially
◦ Norms, values, shared realities
◦ Belonging to a group, tribe, country, ethic group,
religion…
These identities are not fixed, and can change
10.
Who are you? What Identities do youhold?
11.
Assumptions about Communities andStates
Shared norms, values, and identities create
communities
Communities may “tight”/”loose” depending on their
shared identities, norms, values
◦ “Tight” communities share more
◦ “Loose” communities share less
States reflect their communities and are a socially
constructed and act in accordance to their identities
https://www.youtube.com/watch?v=i7-w7goKdGI
12.
The International SystemThe nature of “anarchy” depends on what sates
(and communities and individuals) think about
anarchy
International norms are shaped by norms, beliefs,
and identities, not just power/institutions
◦ Who are our “friends?”
◦ Who are our “Enemies?”
◦ What is our role in the world?
◦ What is the world like? Anarchy? Cooperation?
Expectations, trust, relationships, history change
over time
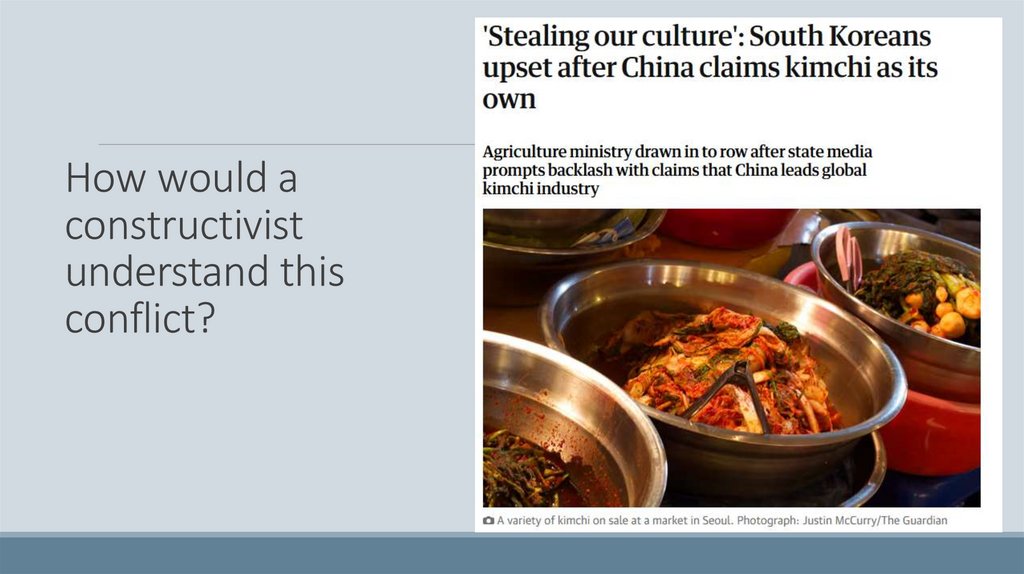
13.
How would aconstructivist
understand this
conflict?
14.
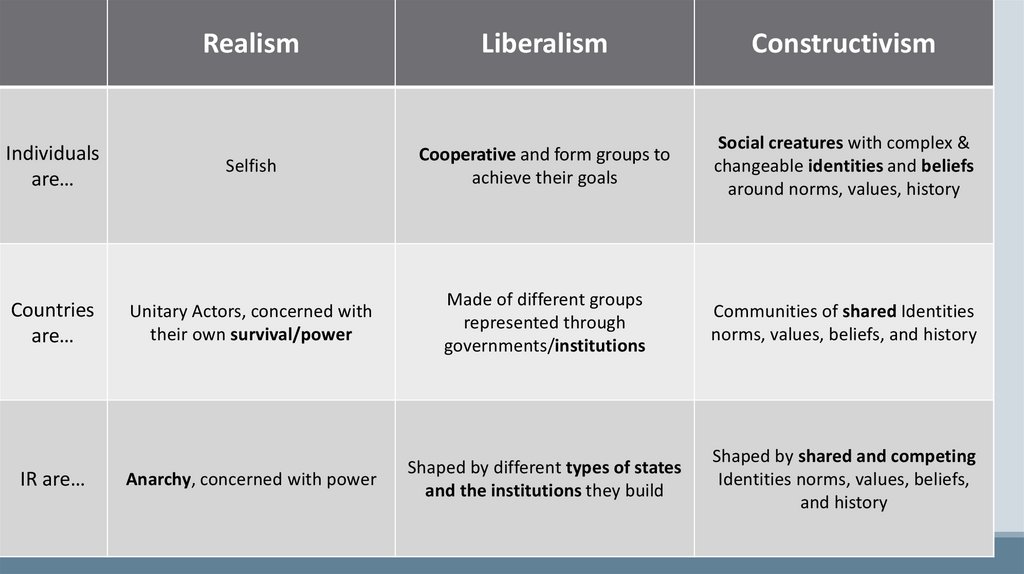
RealismLiberalism
Constructivism
Individuals
are…
Selfish
Cooperative and form groups to
achieve their goals
Social creatures with complex &
changeable identities and beliefs
around norms, values, history
Countries
are…
Unitary Actors, concerned with
their own survival/power
Made of different groups
represented through
governments/institutions
Communities of shared Identities
norms, values, beliefs, and history
Anarchy, concerned with power
Shaped by different types of states
and the institutions they build
Shaped by shared and competing
Identities norms, values, beliefs,
and history
IR are…
15.
Norms16.
Constructivism and NormsNorms are shared expectations and standards of
appropriate behavior of what states should
(prescriptive) and should not (proscriptive) do
Norms are socially constructed and change over time
◦ Norm Lifecycle
◦ Institutionalized: treaties, international organizations
Norms Shape Behavior
◦ Socialization and shared expectations
◦ Reputation and legitimacy
17.
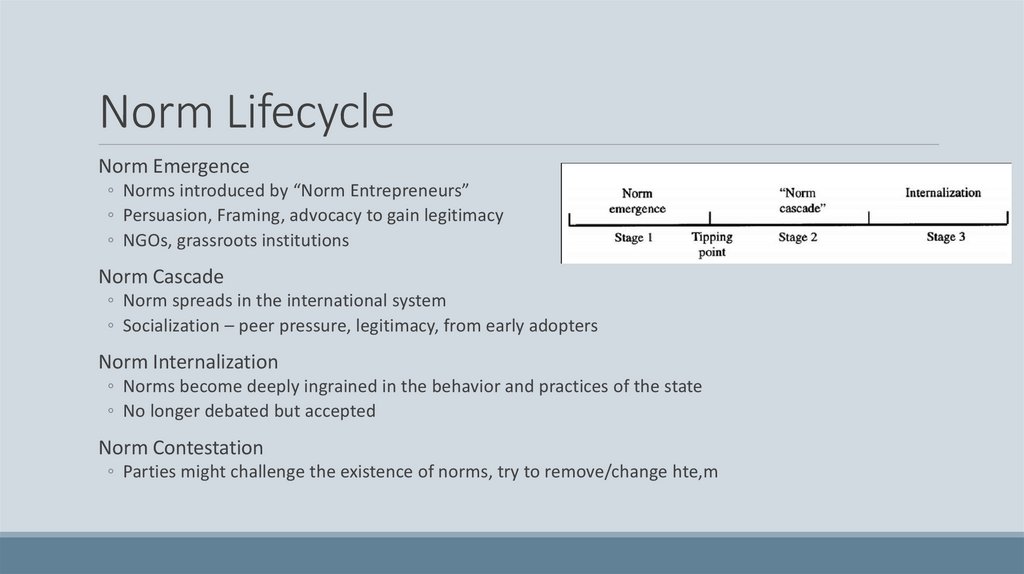
Norm LifecycleNorm Emergence
◦ Norms introduced by “Norm Entrepreneurs”
◦ Persuasion, Framing, advocacy to gain legitimacy
◦ NGOs, grassroots institutions
Norm Cascade
◦ Norm spreads in the international system
◦ Socialization – peer pressure, legitimacy, from early adopters
Norm Internalization
◦ Norms become deeply ingrained in the behavior and practices of the state
◦ No longer debated but accepted
Norm Contestation
◦ Parties might challenge the existence of norms, try to remove/change hte,m
18.
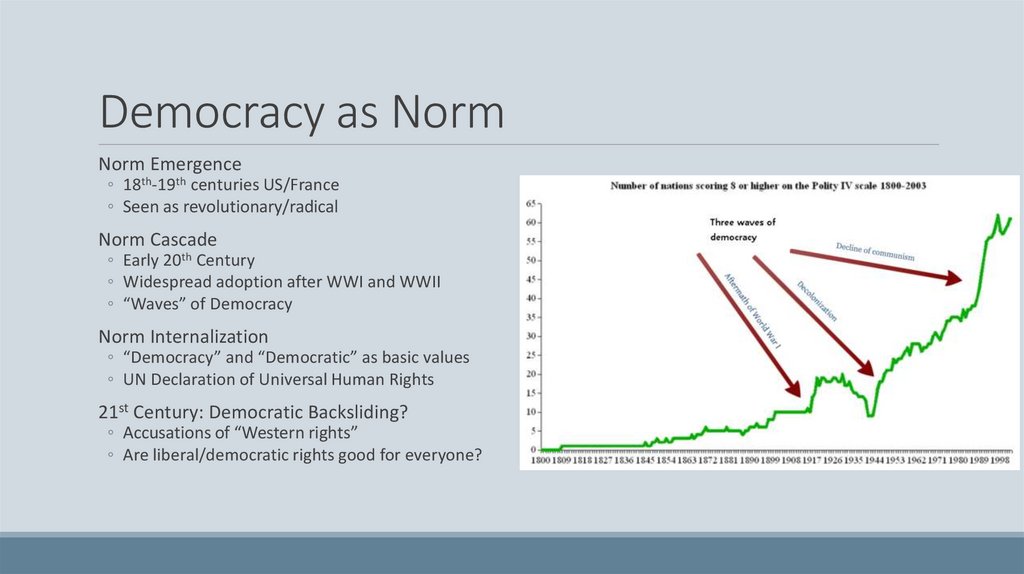
Democracy as NormNorm Emergence
◦ 18th-19th centuries US/France
◦ Seen as revolutionary/radical
Norm Cascade
◦ Early 20th Century
◦ Widespread adoption after WWI and WWII
◦ “Waves” of Democracy
Norm Internalization
◦ “Democracy” and “Democratic” as basic values
◦ UN Declaration of Universal Human Rights
21st Century: Democratic Backsliding?
◦ Accusations of “Western rights”
◦ Are liberal/democratic rights good for everyone?
19.
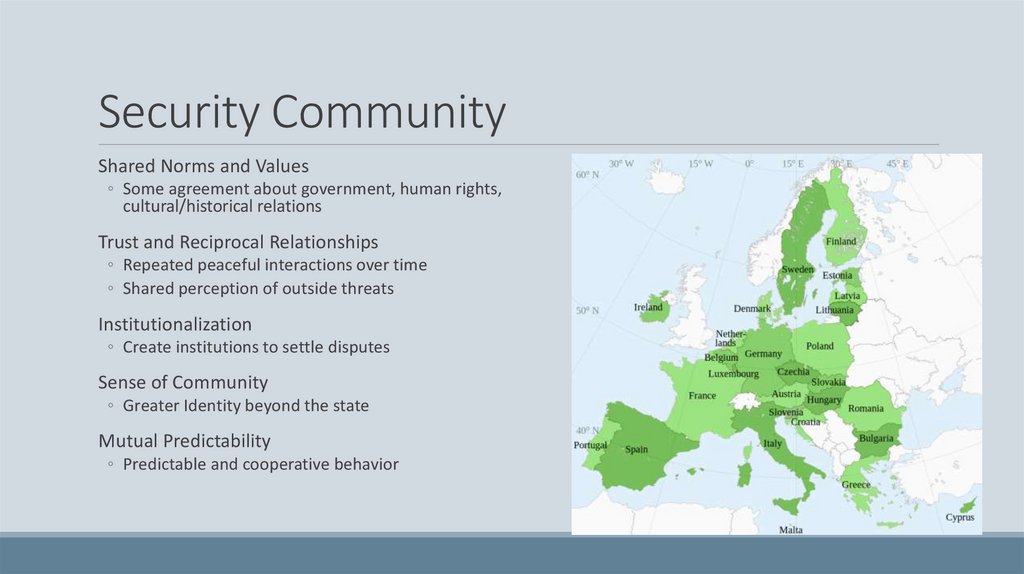
Security Communities20.
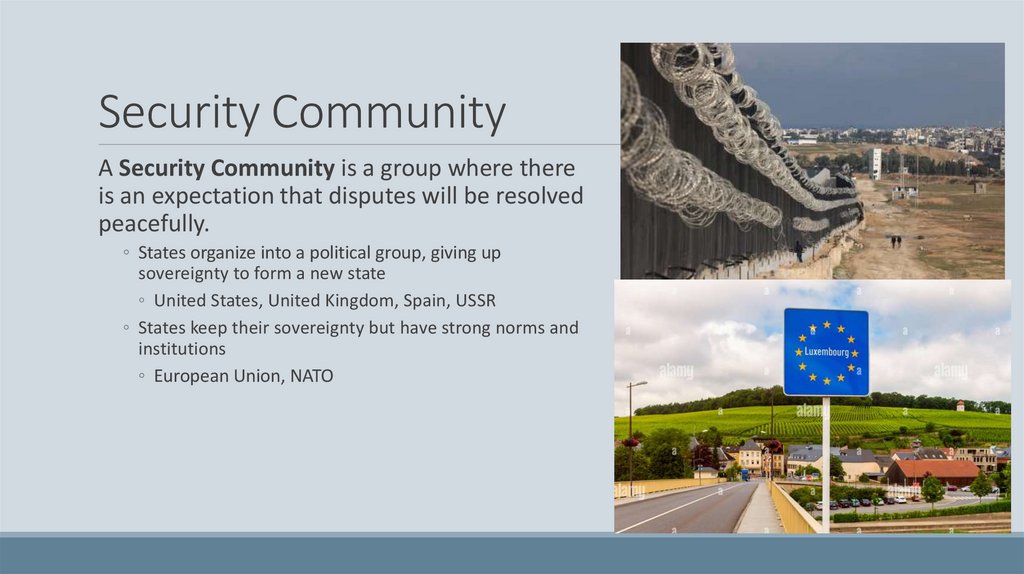
Security CommunityA Security Community is a group where there
is an expectation that disputes will be resolved
peacefully.
◦ States organize into a political group, giving up
sovereignty to form a new state
◦ United States, United Kingdom, Spain, USSR
◦ States keep their sovereignty but have strong norms and
institutions
◦ European Union, NATO
21.
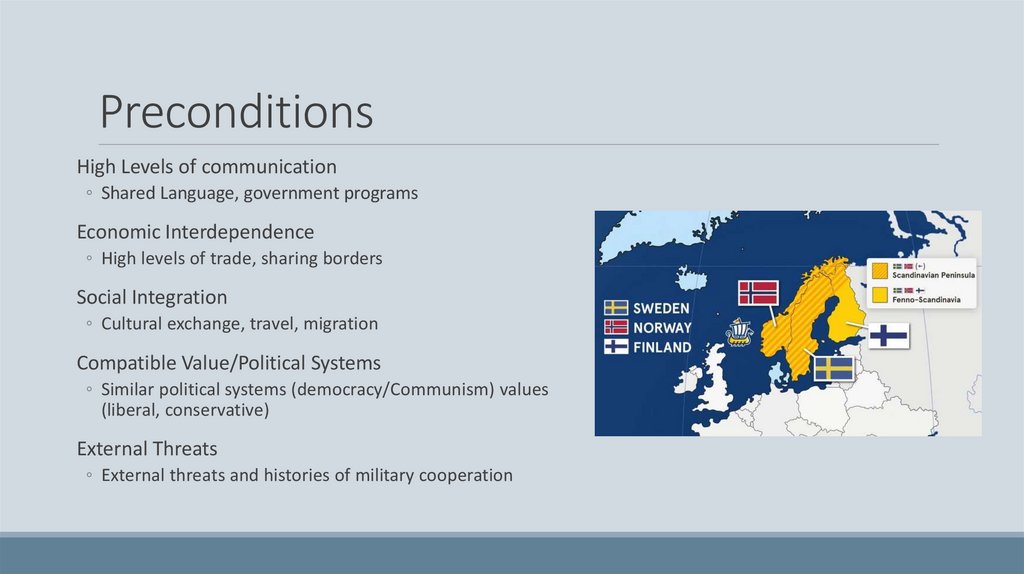
PreconditionsHigh Levels of communication
◦ Shared Language, government programs
Economic Interdependence
◦ High levels of trade, sharing borders
Social Integration
◦ Cultural exchange, travel, migration
Compatible Value/Political Systems
◦ Similar political systems (democracy/Communism) values
(liberal, conservative)
External Threats
◦ External threats and histories of military cooperation
22.
Security CommunityShared Norms and Values
◦ Some agreement about government, human rights,
cultural/historical relations
Trust and Reciprocal Relationships
◦ Repeated peaceful interactions over time
◦ Shared perception of outside threats
Institutionalization
◦ Create institutions to settle disputes
Sense of Community
◦ Greater Identity beyond the state
Mutual Predictability
◦ Predictable and cooperative behavior
23.
European Security CommunityHigh Levels of communication
◦ Lingua Franca (French, English)
Economic Interdependence
◦ Euro
◦ Eurozone, Low taxes,
Social Integration
◦ Cultural exchange, travel, migration
◦ Right to work
Compatible Value/Political Systems
◦ Democratic values (civil liberties, open societies)
External Threats
◦ USSR/Warsaw Pact
24.
European Security CommunityShared Norms and Values
◦ Democracy, Civil liberties
Trust and Reciprocal Relationships
◦ Cross-Border cooperation
◦ Russia
Institutionalization
◦ ICC, ICJ, European Parliament, NATO, Schengen
Zone
Sense of Community
◦ Greater Identity beyond the state
Mutual Predictability
◦ Predictable and cooperative behavior
25.
Film and StateHunt for Red October:
◦ 1984,1990 (Cold War)
◦ https://www.youtube.com/watch?v=AWPBr4L1eyE
Independence day:
◦ 1996 America as Unipolar hegemon
◦ https://www.youtube.com/watch?v=xqRGx4y4J24
Team America: World Police
◦ 2004 American “War on Terror”
◦ https://www.youtube.com/watch?v=MYECYfY7Gu8
Wolf Warrior
◦ 2015, 2017
◦ https://www.youtube.com/watch?v=SCc0DWSZHCs
26.
SecuritizationHTTPS://WWW.YOUTUBE.COM/WATCH?V=WQ07TWOZE_C
27.
Problems with Security and Threats“Threats” by their very nature are about potential
outcomes in the future.
They have not happened yet and may never happen
Uncertainty about
1.
The nature of the issue and
2.
The damage done if it does occur
Accurately identifying threats, and measuring their
outcomes not a science
What issues are security threats? What issues are normal
political issues? How are they different?
28.
What is Securitization?“The Process whereby issues are
presented as security threats and, if
audiences accept these representations,
emergency measures are enabled to
deal with them”
(Nyman, 2018, p.100)
29.
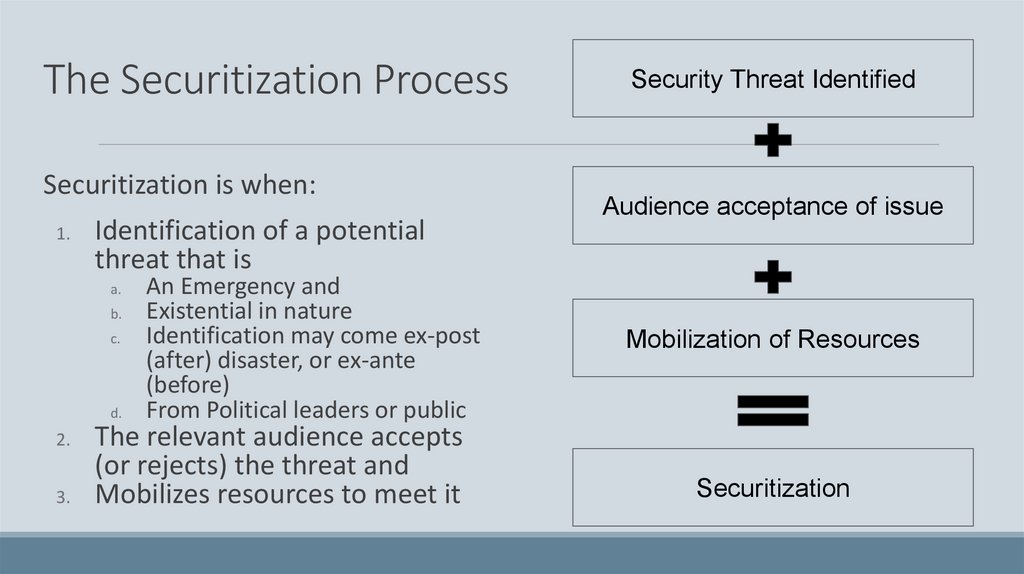
The Securitization ProcessSecuritization is when:
1.
Identification of a potential
threat that is
a.
b.
c.
d.
2.
3.
An Emergency and
Existential in nature
Identification may come ex-post
(after) disaster, or ex-ante
(before)
From Political leaders or public
The relevant audience accepts
(or rejects) the threat and
Mobilizes resources to meet it
Security Threat Identified
Audience acceptance of issue
Mobilization of Resources
Securitization
30.
Identifying ThreatsA political actor (politician, bureaucrat, scientist, media
figure, voting public) declares an issue a threat to
something
◦ State, population, justice, “values”
Threats are extraordinary in nature
◦ Require radical, immediate change outside the normal
bounds of politics
Opportunism: Who does this “threat” benefit? Who is
the political actor and what are their interests?
(Principal-agent problem)
31.
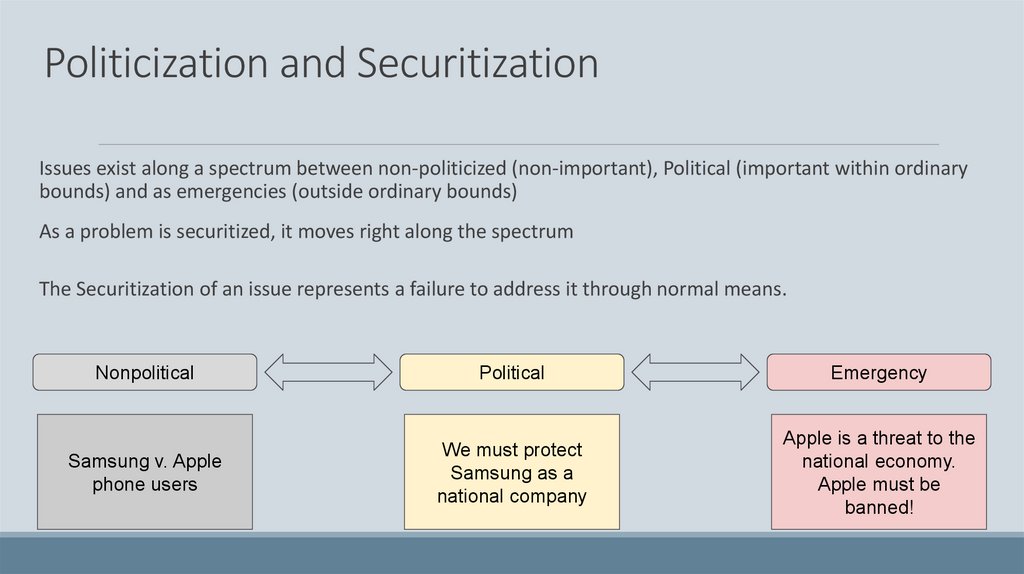
Politicization and SecuritizationIssues exist along a spectrum between non-politicized (non-important), Political (important within ordinary
bounds) and as emergencies (outside ordinary bounds)
As a problem is securitized, it moves right along the spectrum
The Securitization of an issue represents a failure to address it through normal means.
Nonpolitical
Political
Emergency
Samsung v. Apple
phone users
We must protect
Samsung as a
national company
Apple is a threat to the
national economy.
Apple must be
banned!
32.
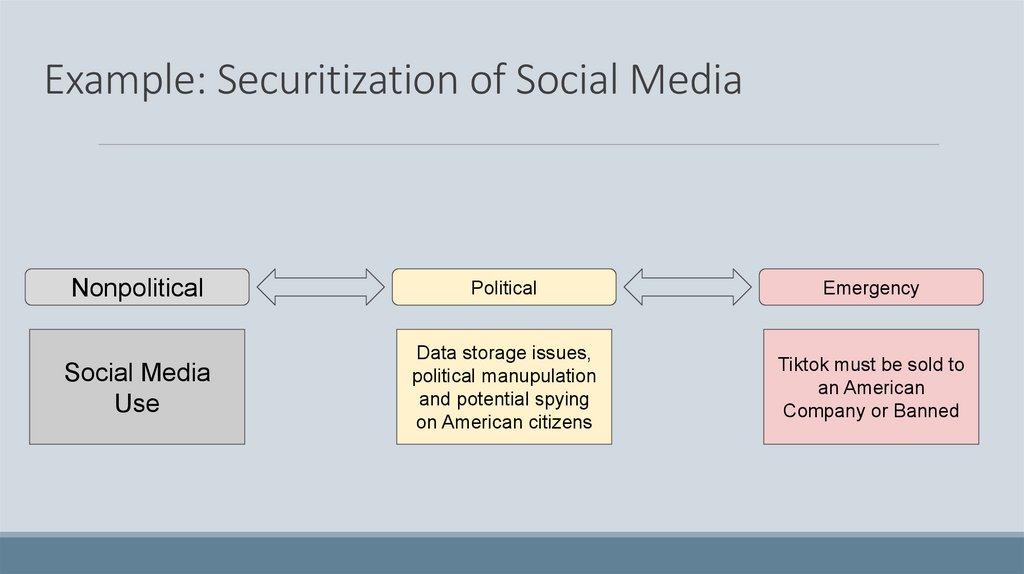
Example: Securitization of Social MediaNonpolitical
Political
Emergency
Social Media
Use
Data storage issues,
political manupulation
and potential spying
on American citizens
Tiktok must be sold to
an American
Company or Banned
33.
Audience AcceptanceAfter an issue is selected for securitization, the threat is
presented to an audience
Audiences will differ depending on the political system
◦ Elites? Political Leaders? Military officials? Voters?
Audience acceptance will also depend on the relevance
of the threat
◦ Does it affect them?
Audiences will be more likely to accept after
demonstration of threat
◦ After a storm, disaster, terrorist attack
◦ Creates political space for false flag (fake) attacks/crises
Audience may reject a security threat if
unconvinced/unconcerned
34.
Extraordinary MeasuresDue to the urgent nature of the threat, extraordinary
measures must be taken
◦ Outside the bounds of “normal” political responses
Bypassing normal procedures
◦ Legislative rules
◦ Civil liberties, property rights
Mobilizing resources
Extra powers to political leaders
Involvement of the military/emergency personnel
Securitization “ends” when problem is no longer
considered a threat, demobilization of resources
◦ Or continued use/abuse of extraordinary measures
35.
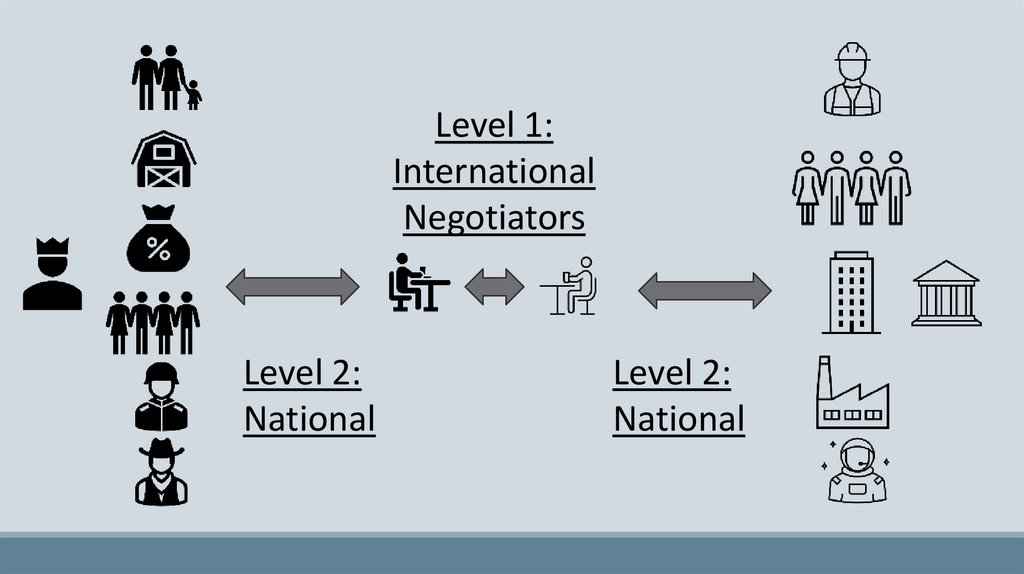
Level 1:International
Negotiators
Level 2:
National
Level 2:
National
















 sociology
sociology








