Similar presentations:
Understanding Dark Web and facilitates organized crime
1.
Understanding Dark Web and facilitatesorganized crime
Done by:
Tenizov I.
Baikhonov E.
Rakhymbekov B.
Teacher: Rozaque A.
Almaty 2023
2.
ContentIntroduction
Research Contribution:
Releated work
Problem Identification and Significance
Conclusion
References
03
3.
IntroductionThe Dark Web is used for more
than just criminal activity, though. It
can be used to safeguard privacy,
particularly in nations where the
government restricts access to
information and freedom of speech.
Additionally, those who worry about
government persecution or repression
can communicate with one another
using it.
Abstract
Abstract - The development of cybercrime was
sparked by the fact that Internet resources aren't
always employed for legal ones. According to the
Internet's infrastructure, the terms "Dark Web"
(which includes dark web and darknet) are
becoming more and more popular.
03
4.
Research Contribution:The dark web is a part of the internet
that can only be accessed with special
software, and it's often associated with
illegal activities such as cybercrime.
03
5.
RELEATED WORK03
6.
Problem Identification and SignificanceThe issue is the growing risk that
the dark web poses to people's
personal, social, and political safety.
For criminal activities like drug
trafficking, human trafficking, the
trafficking of weapons, cyberattacks,
and terrorism, the dark web serves as
a platform [18]. These activities can
have serious negative effects on
public safety, national security, and
international stability
PROPOSED PLAN and SVM web
Structures on the dark web that are predictable For
structure
huge data platforms (dynamic change and uncertain) based
on the Mapper Reduce model, mining techniques for crime
activity information extraction and classification utilizing
neural network algorithm (much like a backpropagation
neural network) are not suitable. Furthermore, this
algorithm works very slowly and cannot fully generate
output when the data measure is large (usually occurring at
the size of terabytes).
03
7.
Proposed Plan ans SVM webstructure
03
8.
Constructive Semisupervised Classification (CSSL)Algorithm 2 is the Constructive Semisupervised
Classification (CSSL) algorithm, which is used for
classification tasks where there is a limited amount of
labeled data available. The algorithm aims to
iteratively improve the classifier's performance by
actively selecting the most informative unlabeled data
points and adding them to the labeled dataset for
retraining
9.
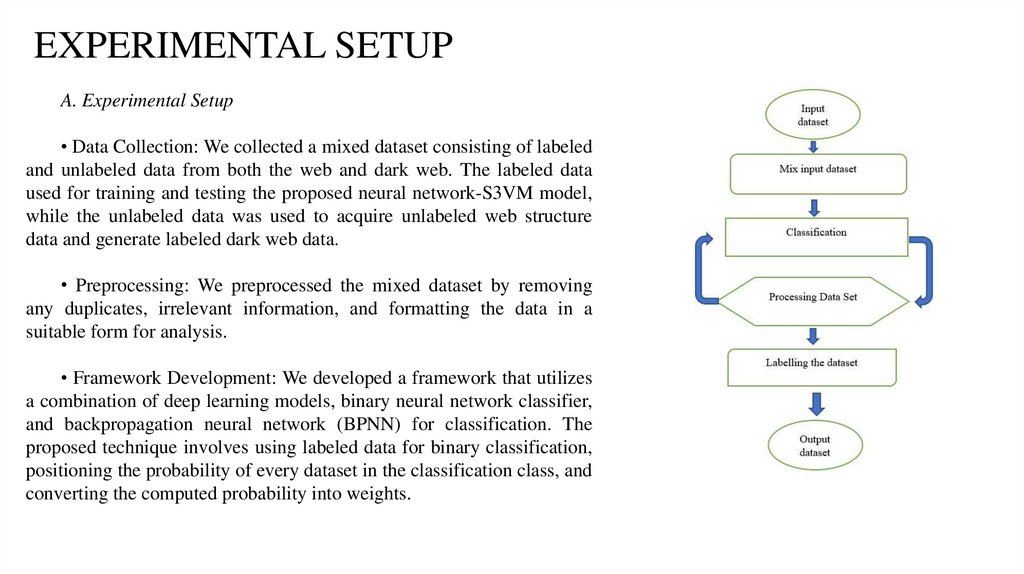
EXPERIMENTAL SETUPA. Experimental Setup
• Data Collection: We collected a mixed dataset consisting of labeled
and unlabeled data from both the web and dark web. The labeled data
used for training and testing the proposed neural network-S3VM model,
while the unlabeled data was used to acquire unlabeled web structure
data and generate labeled dark web data.
• Preprocessing: We preprocessed the mixed dataset by removing
any duplicates, irrelevant information, and formatting the data in a
suitable form for analysis.
• Framework Development: We developed a framework that utilizes
a combination of deep learning models, binary neural network classifier,
and backpropagation neural network (BPNN) for classification. The
proposed technique involves using labeled data for binary classification,
positioning the probability of every dataset in the classification class, and
converting the computed probability into weights.
10.
EXPERIMENTAL RESULTB. Experimental Methods
• Performance Evaluation: To evaluate the performance of the proposed
neural network-S3VM model, we compared its performance to existing
classification techniques. We measured the accuracy, precision, recall, and F1
score of the proposed model using labeled data.
• Hyper-parameter Tuning: We conducted hyper-parameter tuning to
optimize the performance of the proposed model. We adjusted the learning rate,
the number of hidden layers, and the number of neurons in each layer to find the
optimal configuration.
• Cross-validation: We conducted cross-validation to evaluate the
generalization performance of the proposed model. We used k-fold crossvalidation with different values of k to ensure the robustness of the proposed
model.
• Performance Comparison: We compared the performance of the proposed
neural network-S3VM model to other state-of-the-art classification techniques,
such as SVM, Random Forest, and Neural Networks, using different
performance metrics. This allowed us to determine the effectiveness of the
proposed model in improving the performance of existing classification
techniques.
Scenario 1: Improving data classification accuracy
Scenario 2: Analyzing dark web data
Scenario 3: Improving performance of SVM
11.
EXPERIMENTAL RESULTS AND SETUP03
12.
DISCUSSION OF RESULTS13.
CONCLUSIONThe proposed article for improving SVM performance
through the fusion of deep learning models and expanding the
backpropagation neural network shows promising results. By
enhancing the RBF kernel function and utilizing machine
learning for data classification and analysis, the technique
offers an effective and precise approach for analyzing mixed
datasets.
03
14.
ReferencesReferences:
[1] "What is the Deep and Dark Web?" by Kaspersky(2021)https://www.kaspersky.com/resource-center/threats/deep-web
[2] Andrey B. (2022). What Is the Dark Web and Should You Access It? https://www.investopedia.com/terms/d/dark-web.asp
[3] The Dark Web: what is it and why do people use it?https://www.thinkuknow.co.uk/professionals/our-views/the-dark-web/
[4] Aditi K., Eric R.(2019): THE TRUTH ABOUT THE DARK WEB : https://www.imf.org/en/Publications/fandd/issues/2019/09/the-truth-about-the-dark-webkumar
[5] Holt, T. J., & Holt, K. (2017). Exploring the Dark Web: A Look into the Internet's Hidden Side. Journal of Crime and Justice
[6] Selby, J. (2017). The Dark Web: Threats and Opportunities for Governments. Journal of Cyber Policy
[7] Bharat B. (2020). : The Dark Web: A Dive Into the Darkest Side of the Internet Link:https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3598902
[8] Srinjoy S., Sanhita K., Chayantika R.Dark Web: The Hub of Crime https://www.ijraset.com/research-paper/dark-web-the-hub-of-crime
[9] M. Lim, A. Abdullah, and N. Jhanjhi, “Performance optimization of criminal network hidden link prediction model with deep reinforcement learning,” Journal
of King Saud University - Computer and Information Sciences, vol. 33, 2019.
https://www.sciencedirect.com/science/article/pii/S1319157819308584
[10] Sukhchandan Randhawa Dark Web: A Web of Crimes
[11] Mosquera, D., Díaz, D., & Urueña, Á. (2020). Investigating the dark web: challenges and future directions. In Handbook of Research on Applied Cybernetics
and Systems Science (pp. 22-41). IGI Global. https://doi.org/10.4018/978-1-7998-4742-7.ch002
[12]
P.
William
“Systematic
Approach
for
Detection
and
Assessment
of
Dark
Web
Threat
Evolution
https://www.igiglobal.com/gateway/chapter/307882#pnlRecommendationForm
[13] Vincenzo Ciancaglini et al Deep Web and Cybercrime: It’s Not All About Tor https://www.trendmicro.com/vinfo/pl/security/news/cybercrime-and-digitalthreats/deep-web-and-cybercrime-its-not-all-about-tor
[14] Michael Chertoff et al “A public policy perspective of the Dark Web”
https://www.tandfonline.com/doi/full/10.1080/23738871.2017.1298643
[15] Kristin Finklea “Dark Web” https://a51.nl/sites/default/files/pdf/R44101%20(1).pdf
[16] IEEE “Evolution of Dark Web Threat Analysis and Detection: A Systematic Approach” https://ieeexplore.ieee.org/abstract/document/9197590
[17] Gabriel Weimann “Terrorist Migration to the Dark Web” https://www.jstor.org/stable/26297596?seq=1
[18] Abhineet G., Sean B. M. The Dark Web Phenomenon: A Review and Research Agenda. https://arxiv.org/ftp/arxiv/papers/2104/2104.07138.pdf
03
15.
THANK YOUFOR ATTENTION














 internet
internet law
law