Similar presentations:
Network basics and network scanners. Lecture 2
1.
Lecture 2:Network basics and
network scanners
2.
Why we need to learnnetworking?
1. Understanding how networks work
2. Identifying network-based vulnerabilities
3. Testing network security controls
4. Conducting network reconnaissance
5. Exploiting network-based vulnerabilities
3.
Networking BasicsA network is a group of devices connected together for the purpose
of sharing resources and information
1. Local Area Network (LAN)
2. Wide Area Network (WAN)
3. Metropolitan Area Network (MAN)
4.
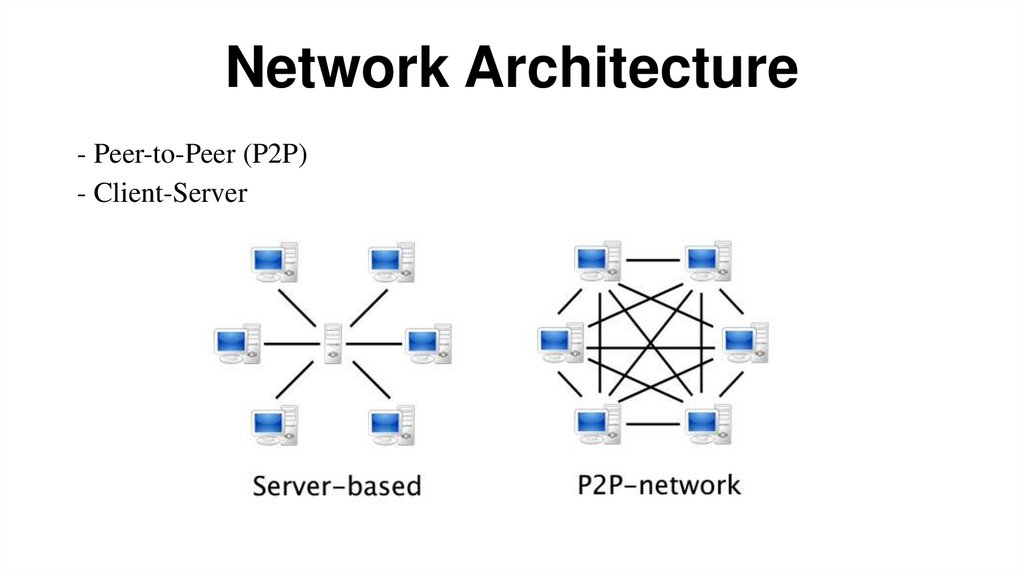
Network Architecture- Peer-to-Peer (P2P)
- Client-Server
5.
Network ProtocolsA network protocol is a set of rules and standards that govern the
communication between devices on a network.
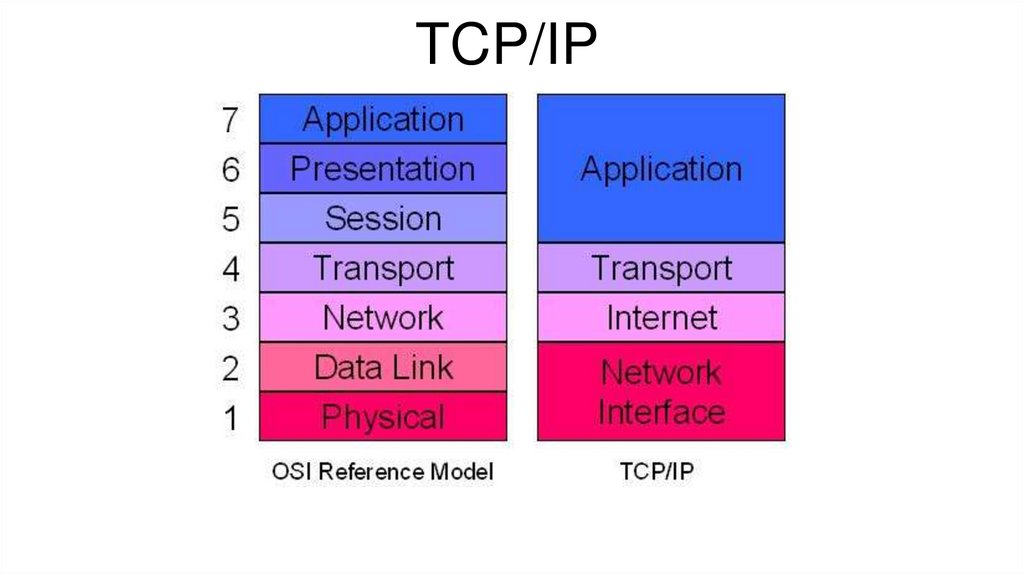
- Transmission Control Protocol/Internet Protocol (TCP/IP)
- Hypertext Transfer Protocol (HTTP/HTTPS)
- Secure Shell (SSH)
- DNS
- DHCP
6.
TCP/IP7.
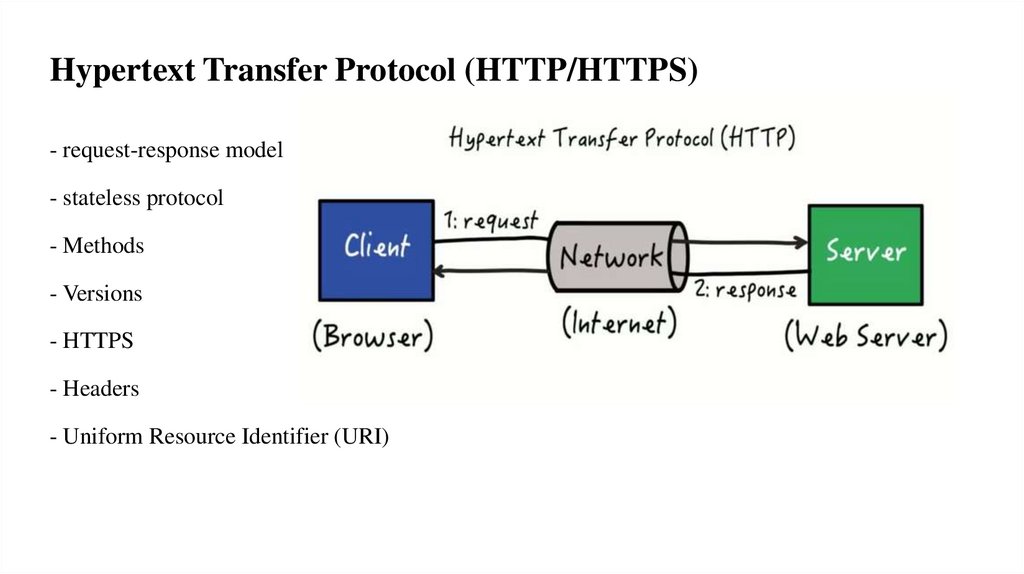
Hypertext Transfer Protocol (HTTP/HTTPS)- request-response model
- stateless protocol
- Methods
- Versions
- HTTPS
- Headers
- Uniform Resource Identifier (URI)
8.
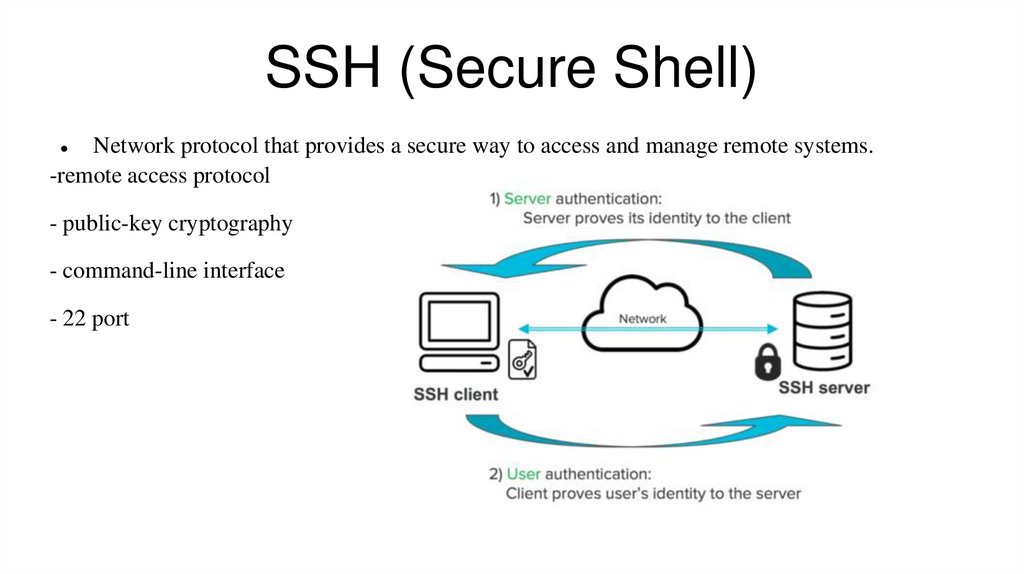
SSH (Secure Shell)Network protocol that provides a secure way to access and manage remote systems.
-remote access protocol
- public-key cryptography
- command-line interface
- 22 port
9.
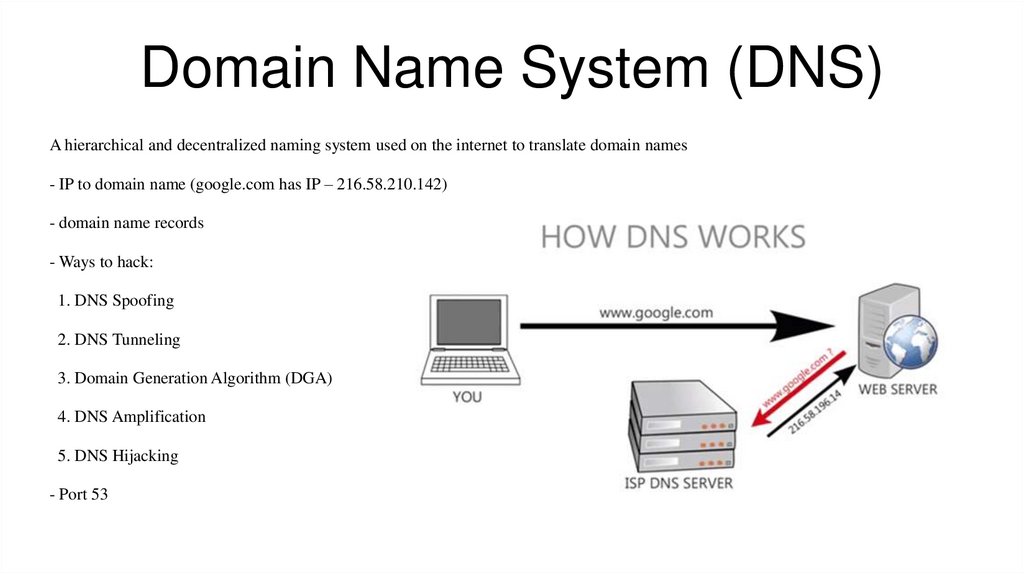
Domain Name System (DNS)A hierarchical and decentralized naming system used on the internet to translate domain names
- IP to domain name (google.com has IP – 216.58.210.142)
- domain name records
- Ways to hack:
1. DNS Spoofing
2. DNS Tunneling
3. Domain Generation Algorithm (DGA)
4. DNS Amplification
5. DNS Hijacking
- Port 53
10.
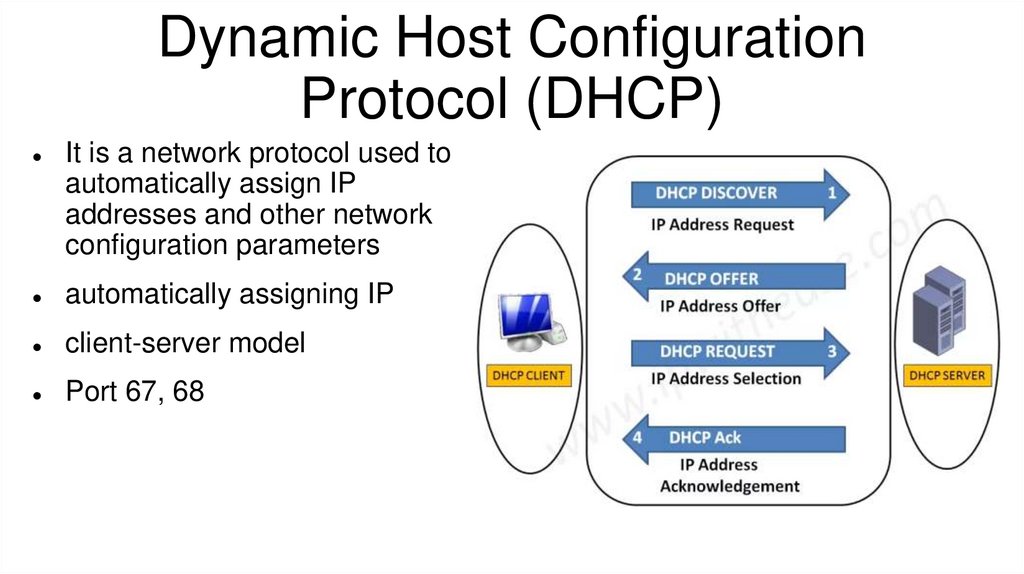
Dynamic Host ConfigurationProtocol (DHCP)
It is a network protocol used to
automatically assign IP
addresses and other network
configuration parameters
automatically assigning IP
client-server model
Port 67, 68
11.
Network Devices: Routerconnects two or more networks together and routes data packets
between them
12.
Network Devices: Switchconnects multiple devices on a network and directs data packets to their
intended destination
13.
Network Devices: Firewallused to protect a network from unauthorized access
14.
Network Devices: Modemconverts digital signals from a computer or other device into analog
signals that can be transmitted over telephone lines
15.
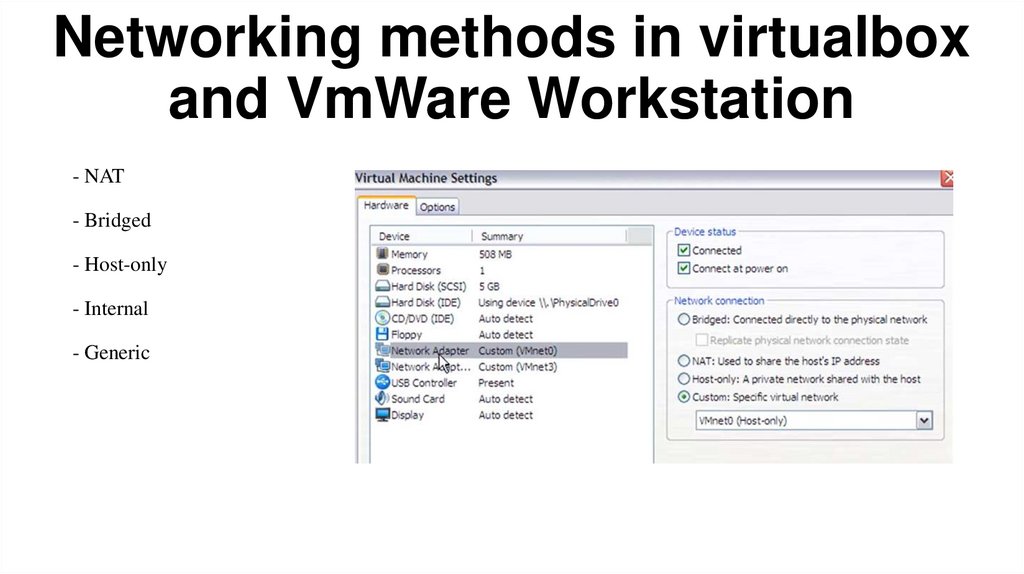
Networking methods in virtualboxand VmWare Workstation
- NAT
- Bridged
- Host-only
- Internal
- Generic
16.
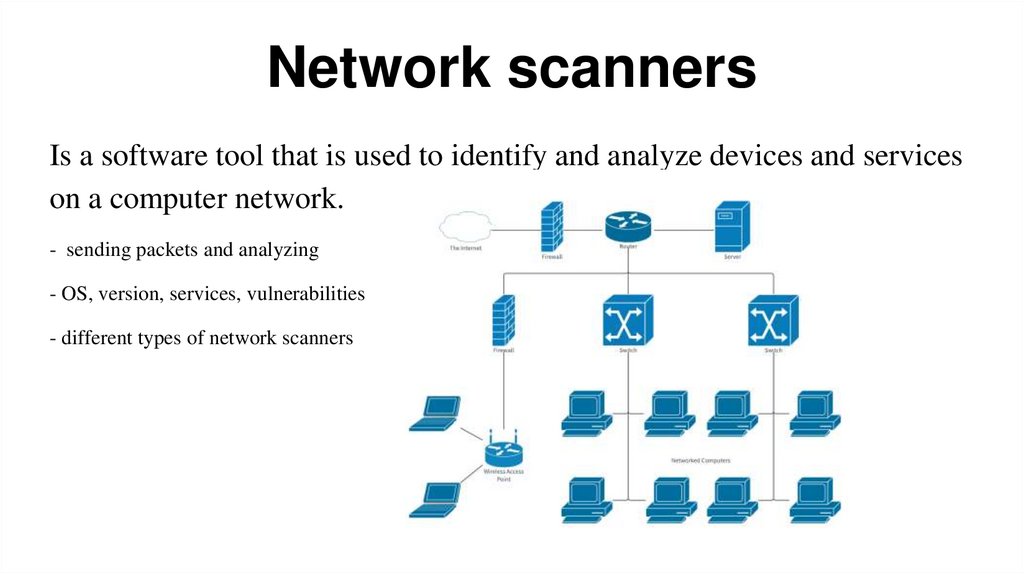
Network scannersIs a software tool that is used to identify and analyze devices and services
on a computer network.
- sending packets and analyzing
- OS, version, services, vulnerabilities
- different types of network scanners
17.
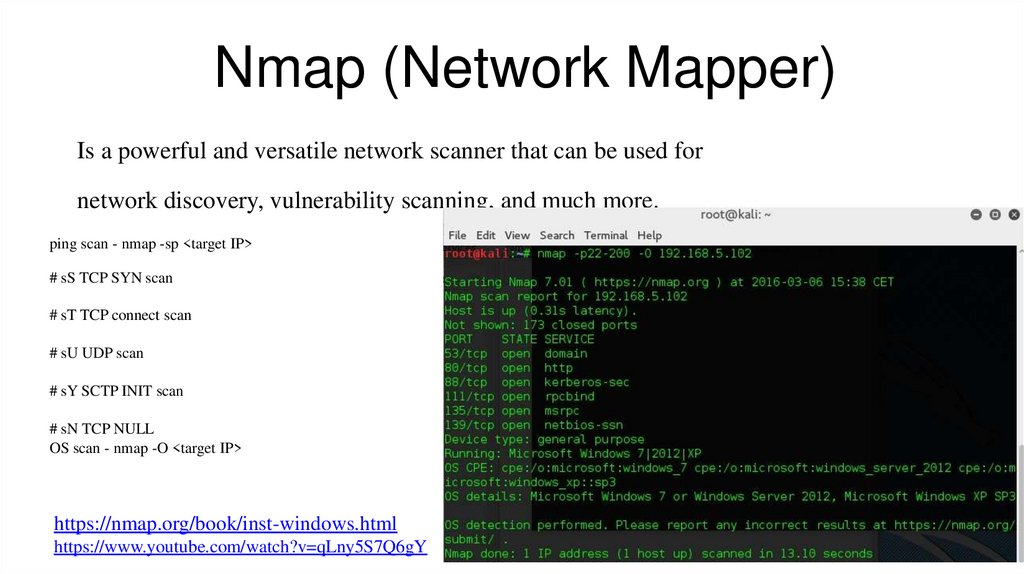
Nmap (Network Mapper)Is a powerful and versatile network scanner that can be used for
network discovery, vulnerability scanning, and much more.
ping scan - nmap -sp <target IP>
# sS TCP SYN scan
# sT TCP connect scan
# sU UDP scan
# sY SCTP INIT scan
# sN TCP NULL
OS scan - nmap -O <target IP>
https://nmap.org/book/inst-windows.html
https://www.youtube.com/watch?v=qLny5S7Q6gY
18.
Anrgy IP ScannerHelps you to scan a range of IP addresses to find live hosts, open ports, and other relevant
information of each and every IP address.
https://angryip.org/download/#windows
https://www.youtube.com/watch?v=B05RbvC0x7I
19.
OpenVASOpen-source vulnerability
scanner and management
software
-components
- vulnerability checks
https://www.youtube.com/wat
ch?v=jxbryT68_f0
20.
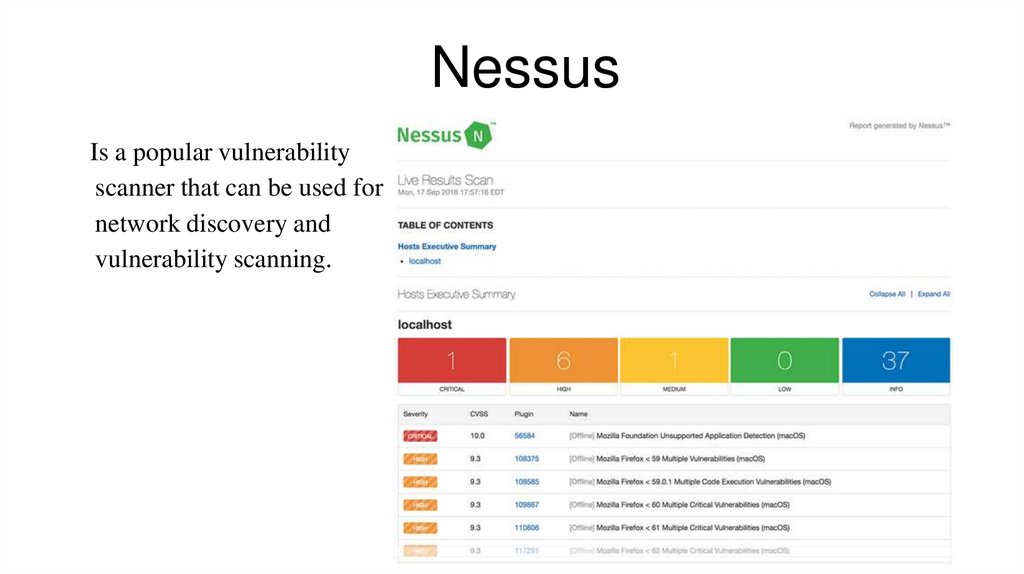
NessusIs a popular vulnerability
scanner that can be used for
network discovery and
vulnerability scanning.








 internet
internet