Similar presentations:
Computer Viruses and Worms
1. Computer Viruses and Worms
Krivorotov Eugeny 6 group2. Definition of Virus
A virus is a small piece of software thatpiggybacks on real programs in order to get
executed
Once it’s running, it spreads by inserting
copies of itself into other executable code or
documents
3. Computer Virus Timeline
1949Theories for self-replicating programs are first developed.
1981
Apple Viruses 1, 2, and 3 are some of the first viruses “in the wild,” or in the public domain. Found on
the Apple II operating system, the viruses spread through Texas A&M via pirated computer games.
1983
Fred Cohen, while working on his dissertation, formally defines a computer virus as “a computer
program that can affect other computer programs by modifying them in such a way as to include a
(possibly evolved) copy of itself.”
1986
Two programmers named Basit and Amjad replace the executable code in the boot sector of a floppy
disk with their own code designed to infect each 360kb floppy accessed on any drive. Infected floppies
had “© Brain” for a volume label.
1987
The Lehigh virus, one of the first file viruses, infects command.com files.
1988
One of the most common viruses, Jerusalem, is unleashed. Activated every Friday the 13th, the virus
affects both .exe and .com files and deletes any programs run on that day.
MacMag and the Scores virus cause the first major Macintosh outbreaks.
…
4. Worms
Worm - is a self-replicating program,similar to a computer virus. A virus
attaches itself to, and becomes part of,
another executable program; however,
a worm is self-contained and does not
need to be part of another program to
propagate itself.
5. History of Worms
The first worm to attract wide attention, theMorris worm, was written by Robert Tappan
Morris, who at the time was a graduate
student at Cornell University.
It was released on November 2, 1988
Morris himself was convicted under the US
Computer Crime and Abuse Act and received
three years probation, community service and
a fine in excess of $10,000.
Xerox PARC
6. Worms…
Worms – is a small piece of software thatuses computer networks and security holes to
replicate itself. A copy of the worm scans the
network for another machine that has a
specific security hole. It copies itself to the
new machine using the security hole, and
then starts replicating from there, as well.
They are often designed to exploit the file
transmission capabilities found on many
computers.
7. Zombies
Infected computers — mostly Windowsmachines — are now the major delivery
method of spam.
Zombies have been used extensively to
send e-mail spam; between 50% to
80% of all spam worldwide is now sent
by zombie computers
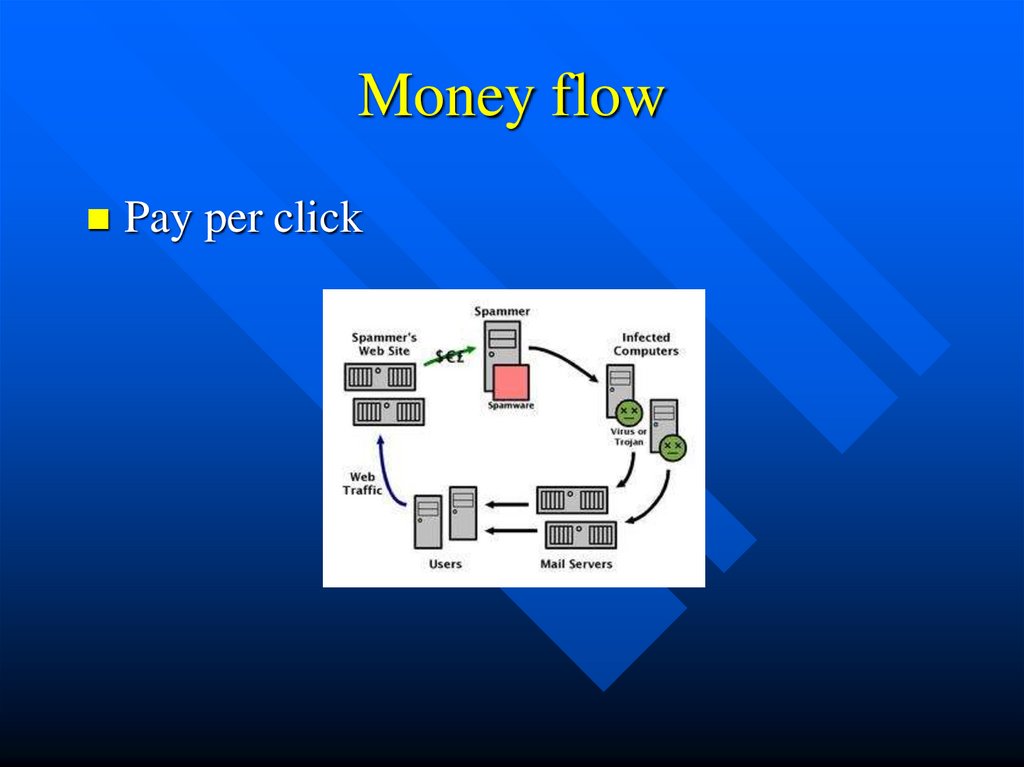
8. Money flow
Pay per click9. Typical things that some current Personal Computer (PC) viruses do
Display a message10. Typical things that some current Personal Computer (PC) viruses do
Display a messageErase files
Scramble data on a hard disk
Cause erratic screen behavior
Halt the PC
Many viruses do nothing obvious at all
except spread!
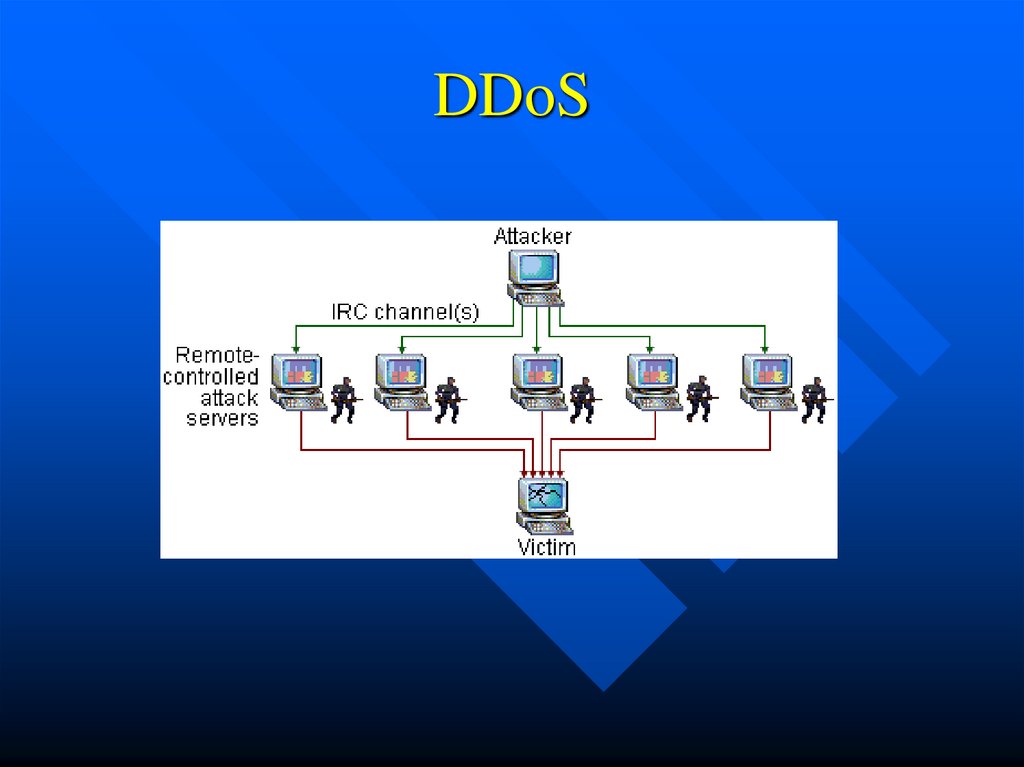
11. Distributed Denial of Service
A denial-of-service attack is an attack thatcauses a loss of service to users, typically
the loss of network connectivity and
services by consuming the bandwidth of the
victim network or overloading the
computational resources of the victim
system.
12. How it works?
The flood of incoming messages to the targetsystem essentially forces it to shut down, thereby
denying service to the system to legitimate users.
Victim's IP address.
Victim's port number.
Attacking packet size.
Attacking interpacket delay.
Duration of attack.
MyDoom – SCO Group
13. DDoS
14. MyDoom
26 January 2004: The Mydoom virus isfirst identified around 8am. Computer
security companies report that Mydoom is
responsible for approximately one in ten email messages at this time. Slows overall
internet performance by approximately ten
percent and average web page load times by
approximately fifty percent
15. MyDoom…
27 January: SCO Group offers a US $250,000reward for information leading to the arrest of the
worm's creator.
1 February: An estimated one million computers
around the world infected with Mydoom begin the
virus's massive distributed denial of service
attack—the largest such attack to date.
2 February: The SCO Group moves its site to
www.thescogroup.com.
16. Executable Viruses
Traditional Virusespieces of code attached to a legitimate
program
run when the legitimate program gets
executed
loads itself into memory and looks around
to see if it can find any other programs on
the disk
17. Boot Sector Viruses
Traditional Virusinfect the boot sector on floppy disks and
hard disks
By putting its code in the boot sector, a
virus can guarantee it gets executed
load itself into memory immediately, and it
is able to run whenever the computer is on
18. Decline of traditional viruses
Reasons:– Huge size of today’s programs storing on a
compact disk
– Operating systmes now protect the boot sector
19. E-mail Viruses
Moves around in e-mail messagesReplicates itself by automatically mailing
itself to dozens of people in the victim’s email address book
Example: Melissa virus, ILOVEYOU virus
20. Melissa virus
March 1999the Melissa virus was the fastest-spreading virus
ever seen
Someone created the virus as a Word document
uploaded to an Internet newsgroup
People who downloaded the document and opened
it would trigger the virus
The virus would then send the document in an email message to the first 50 people in the person's
address book
21. Melissa virus
Took advantage of the programminglanguage built into Microsoft Word called
VBA (Visual Basic for Applications)
22. Prevention
UpdatesAnti-Viruses
More secure operating systems
e.g. UNIX
23. Reference
http://mirror.aarnet.edu.au/pub/code-red/newframes-small-log.gifhttp://www.factmonster.com/ipka/A0872842.html
http://www.faqs.org/faqs/computer-virus/new-users/
http://www.mines.edu/academic/computer/viri-sysadmin.htm



















 software
software








