Similar presentations:
Hostilities 2.0 or the law of cyber armed conflicts: ratione materiae in cyberspace
1.
HOSTILITIES 2.0 OR THE LAW OFCYBER ARMED CONFLICTS: RATIONE
MATERIAE IN CYBERSPACE
Sergei Garkusha-Bozhko
2.
3.
Cyberspace is “fifth domain ofwarfare” next to land, sea, air and
space.
4.
Ratione materiae of the law of cyber armed conflicts.Why it is so important?
• Cyberspace is not an ordinary theatre of war
• Cyber means and methods of warfare are in no way connected
with the traditional use of armed force
• Most cyber systems still have a civilian character
• The possibility to execute a cyber operation both in wartime
and in peacetime (cyber attack in peacetime, use of cyber
means during riots, “colour revolutions”, etc)
• Cyber armed conflict vs. Cyber war
5.
The main questionDo the rules of international
humanitarian law apply only to
cyber operations that can be
recognized as an attack, or to all
military cyber operations?
6.
Article 48 of Protocol Additional to the Geneva Conventions of12 August 1949, and relating to the Protection of Victims of
International Armed Conflicts (Protocol I), 8 June 1977
In order to ensure respect for and protection of the civilian
population and civilian objects, the Parties to the conflict shall
at all times distinguish between the civilian population and
combatants and between civilian objects and military
objectives and accordingly shall direct their operations only
against military objectives
7.
Article 51 of Protocol Additional I:1. The civilian population and individual civilians shall enjoy general
protection against dangers arising from military operations.
2. The civilian population as such, as well as individual civilians, shall not
be the object of attack.
3. Civilians shall enjoy the protection afforded by this Section, unless and
for such time as they take a direct part in hostilities.
5. Among others, the following types of attacks are to be considered as
indiscriminate:
…
b) an attack which may be expected to cause incidental loss of civilian
life, injury to civilians, damage to civilian objects, or a combination
thereof, which would be excessive in relation to the concrete and direct
military advantage anticipated.
6. Attacks against the civilian population or civilians by way of reprisals
are prohibited.
8.
Article 52 (2) of Protocol Additional I:Attacks shall be limited strictly to
military objectives.
Article 57 (1) of Protocol Additional I:
In the conduct of military operations,
constant care shall be taken to spare the
civilian population, civilians and
civilian objects.
9.
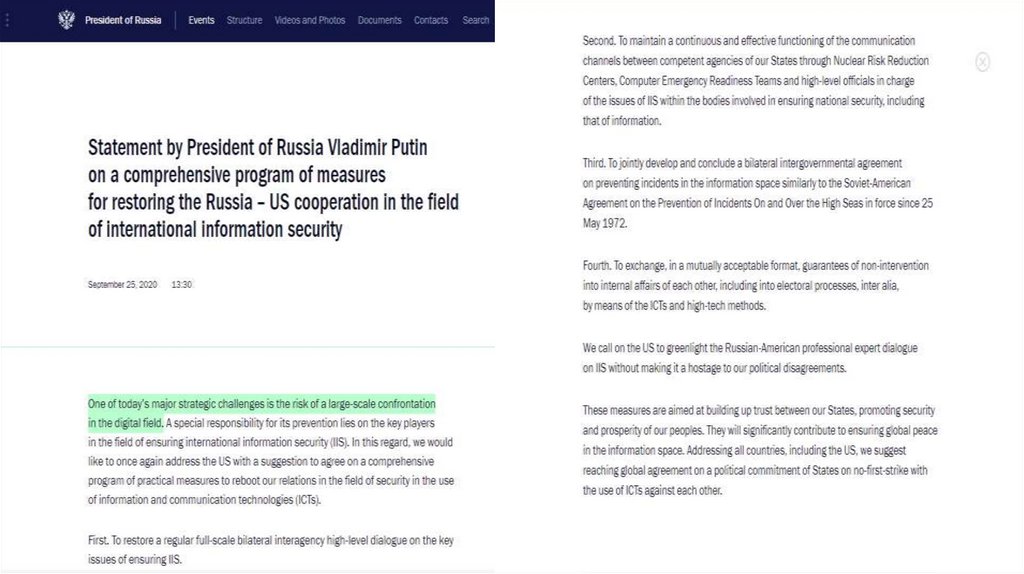
The first point of view on ratione materiae of IHL incyberspace
Only those cyber operations that are an attack
(cyber attacks) fall under the IHL limitations, in
particular, under the principle of distinction
M.N. Schmitt:
certain military operations can be specifically
directed against the civilian population, in
particular, psychological operations, and
therefore, not all military actions in cyberspace
will be limited by the principle of distinction
10.
The second point of view (Nils Melzer)“Accurately understood, the applicability of the restraints imposed by
IHL on the conduct of hostilities to cyber operations depends not on
whether the operations in question qualify as “attacks” (that is, the
predominant form of conducting hostilities), but on whether they
constitute part of the “hostilities” within the meaning of IHL.
…
Accordingly, where cyber operations attributable to a belligerent party
are designed to harm the adversary, either by directly causing death,
injury or destruction, or by directly adversely affecting military
operations or military capacity, such operations must be regarded as
“hostilities” and, therefore, subject to all restrictions imposed by IHL on
the choice and use of means and methods of warfare. If conducted by
civilians, such operations also entail loss of protection against direct
attacks”
11.
Third point of view (HeatherHarrison Dinnis)
The prohibition of attacks on the civilians and
civilian objects applies not only to attacks .
According to articles 48, 51 and 57 of Protocol
Additional I, civilians are protected from hostilities
in general, including attacks; and therefore, the
principles of international humanitarian law are
fully applicable to cyber operations, including cyber
attacks, which are military actions, while cyber
attacks should be correlated with the use of
traditional armed force, but should not necessarily
lead to the same consequences.
12.
Cordula Droege (Chief Legal Officer and Head of the LegalDivision of the ICRC) reply to H.H. Dinnis position
“Despite these arguments in favour of expanding the
types of operations to which the rules on the conduct
of hostilities must apply, it is clear that states did
differentiate in Additional Protocol I between the
general principles in the respective chapeaux of the
rules of distinction and precaution and the specific
rules relating to attacks, and that they found it
necessary to define attacks specifically in Article 49 of
the Protocol. It is difficult to depart from this
dichotomy between military operations and attacks”.
13.
Our opinionThis dichotomy does not affect the application of the IHL principles
to attacks in any way – this definition of attacks was fixed based on
the fact that an attack is one of the main military operations, i.e. it is
the special phenomenon of the general concept of “hostilities”. In
addition, the position of H.H. Dinnis once again confirms the fact
that the principles of international humanitarian law apply to the
entire complex of military operations.
14.
Criticism of M.N. Schmitt point of viewC.Droege:
“…the argument made by Michael Schmitt that some
operations, such as psychological operations, can be
directed at civilians, implying that some military
operations could be directed at civilians, rests on a
misunderstanding of the concept of military operations.
Indeed, while it is true that some cyber operations, such as
psychological operations, can be directed at the civilian
population, this is because they do not fall under military
operations or hostilities within the meaning intended by
the Protocol’s drafters”.
15.
Legal Aspect of the Term“Military Operations”
“…the word “operations”…refers to military operations during which violence is used,
and not to ideological, political or religious campaigns. For reasons which have nothing
to do with the discussions in the Diplomatic Conference, the adjective “military” was
not used with the term “operations”, but this is certainly how the word should be
understood…“military operations” refers to all movements and acts related to
hostilities that are undertaken by armed forces”.
(Commentary to Article 48 of Protocol Additional I)
“…the term “military operations”…means all the movements and activities carried out
by armed forces related to hostilities”.
(Commentary to Article 51 of Protocol Additional I)
“The term “military operations” should be understood to mean any movements,
manoeuvres and other activities whatsoever carried out by the armed forces with a view
to combat”.
(Commentary to Article 57 of Protocol Additional I)
16.
ConclusionAll cyber operations that can be equated to military actions
in general, and not just to cyber attacks, fall under the
restrictions imposed by IHL. This is the ratione materiae of
international humanitarian law in cyberspace.
In addition, the position of Tallinn Manual 2.0:
“The term “cyber operations” includes, but is not limited
to, “cyber attacks”…Certain cyber operations, such as
those affecting the delivery of humanitarian assistance, are
governed by the law of armed conflict even if they do not
rise to the level of an “attack”.
17.
Cyber attack in the context of an armed conflictArticle 49 (1) of Protocol Additional I:
Attacks” means acts of violence against the
adversary, whether in offence or in defence
Can cyber attacks qualify as an attack, in
accordance with article 49 of Protocol
Additional I?
18.
First point of view (M.N. Schmitt)Earlier works:
“… cyber operations can therefore qualify as “attacks,” even though they are not
themselves “violent,” because they have “violent consequences.” A cyber operation, like
any other operation, is an attack when resulting in death or injury of individuals, whether
civilians or combatants, or damage to or destruction of objects, whether military
objectives or civilian objects”.
Past works:
“That reality has changed dramatically. In contemporary warfare, systems and
equipment, whether civilian or military, can be more susceptible to being rendered
inoperative by cyber than kinetic means. For instance, it may be impossible to target an
object kinetically because it is hardened, difficult to locate, or situated in the proximity of
civilians or civilian objects such that there is a risk of violating the rule of
proportionality. Yet, depending on the circumstances, such factors may be no hindrance
to cyber operations. Moreover, for the military and for civilians, it makes little difference
whether a computer system or an object relying on computers fails to function because it
is disabled kinetically or non-kinetically. It simply does not work. In the cyber context,
therefore, the logic underpinning the requirement for injury or physical damage breaks
down”.
19.
Second point of view (K. Dörmann)Cyber attacks can be an attack, even if there
are no traditional consequences of attacks in
the physical world.
20.
The Basis for the second point of viewArticle 52 (2) of Protocol Additional I:
Attacks shall be limited strictly to military objectives. In so far as
objects are concerned, military objectives are limited to those
objects which by their nature, location, purpose or use make an
effective contribution to military action and whose total or partial
destruction, capture or neutralization, in the circumstances
ruling at the time, offers a definite military advantage.
K. Dörmann:
“By referring not only to destruction or capture of the object but also to its
neutralization the definition implies that it is irrelevant whether an object is
disabled through destruction or in any other way”
21.
Criticism of K. Dörmann positionM.N. Schmitt
“However, Dörmann’s poses the opposite risk, that of overinclusivity. It
would encompass, for instance, all denial of service attacks, including
those in which mere inconvenience resulted, as in the case of blocking a
television broadcast or university website. State practice provides no
support for the notion that causation of inconvenience is intended to be
prohibited in IHL”.
After the evolution:
“Although the neutralization argument is counter-factual, the result it
achieves better approximates what I believe has become the prevailing
understanding of the concept of attack in the cyber context. Since my
initial “Wired Warfare” analysis was designed to capture the lex lata and
not the lex ferenda, my position demands “rewiring”.
22.
The Basis for the primary position ofM.N. Schmitt
Bothe M., Partsch K. J. & Solf W. A., 1982. New Rules for
Victims of Armed Conflicts: Commentary to the two 1977
Protocols Additional to the Geneva Conventions of 1949.
Martinus Nijhoff Publishers, pp. 325:
“The term “neutralization” , insofar as it deals with
bombardment, refers to an attack for the purpose of denying
the use of an object to the enemy without necessarily
destroying it”.
NB! This theory does not correspond to the reality!!!
23.
Tallinn Manual 2.0 on the International LawApplicable to Cyber Operations
Rule 92 – Definition of cyber attack
A cyber attack is a cyber operation, whether
offensive or defensive, that is reasonably
expected to cause injury or death to persons or
damage or destruction to objects.
Commentary, para. 2:
This Rule sets forth a definition of ‘attack’ that
draws on that found in Article 49(1) of
Additional Protocol I
24.
CriticismCordula Droege:
“However, as the commentary shows, experts [of the
Tallinn Manual] disagreed as to what exactly was to be
understood as “damage” to objects, and whether or what
type of impairment of the functioning of an object would
fall within its definition.
The weakness of the opinion is that it is under-inclusive.
First, it would not make sense to consider that if a
civilian object is rendered useless, regardless of the way
in which this was done, it is not damaged. Whether an
electrical grid is put out of order by physical damage or
interference with the computer system by which it is run
cannot be a relevant criterion”.
25.
The concept of “damage”The concept of “damage” differs in content from the concept of
“destruction”. Under the damage in this context, it is necessary to
understand the damage caused, as a result of which the damaged
object loses any of its useful characteristics. Therefore, it is quite
logical to consider the disruption of the normal functioning of
various infrastructures as a result of cyber attacks as damage.
NB! Disruption of normal functioning in cyberspace is a
temporary phenomenon, because a damaged system and data in it
can always be restored. Hence, it is logical to qualify cyber
attacks as an attack even if they have led to a temporary
disruption of the normal functioning of the infrastructure without
its physical destruction or destruction.
26.
The broad interpretation of the term“attack” in relation to cyberspace.
Absurd conclusion: all cyberattacks directed
against civilian cyber systems must be
recognized as attacks within the meaning of
IHL.
“to equate such disruptions of what are
essentially communication systems with attacks
would probably go beyond the scope of what
was envisaged by the rules on the conduct of
hostilities” (C. Droege).
27.
The criterion of inconvenienceM.N. Schmitt offers the criterion of
inconvenience
as
a
criterion
for
distinguishing cyberattacks, which are
attacks within the meaning of IHL, from
acts of cybercrime.
What is an inconvenience? It seems that
this criterion is rather vague.
28.
The concept of “critical infrastructure”Proposed by Nils Melzer
This concept is already reflected in existing
information security treaties and in the laws
of some States
29.
Critical infrastructure. Treaties and the lawsAgreement between the Governments of the Shanghai Cooperation Organization
Member States on Cooperation in the Field of Ensuring the International Information
Security of 16 June 2009 (entered into force 2 June 2011)
Agreement between the Government of the Russian Federation and the
Government of the Republic of Belarus on Cooperation in the Field of
Ensuring the International Information Security of 25 December 2013
(entered into force 27 February 2015)
Agreement between the Government of the Russian Federation and the
Government of the People’s Republic of China on Cooperation in the
Field of Ensuring the International Information Security of 8 May 2015
(entered into force 10 August 2016)
Russian Federal Law of 26 July 2017 No. 187-FZ “On the Security of the
Critical Information Infrastructure of the Russian Federation” (entered
into force 01 January 2018)
30.
Agreement between the Government of the Russian Federation and theGovernment of the People’s Republic of China on Cooperation in the Field of
Ensuring the International Information Security of 8 May 2015
Article 1:
Objects of critical information infrastructure – cyber
systems, information and telecommunication networks
of state bodies; cyber systems, information and
telecommunication networks and automated process
control systems designed to ensure the country’s
defence, state security, law and order, as well as
functioning in the field of healthcare, transport,
communications, in the credit and financial sphere, in
the military-industrial, fuel and energy complexes, in the
nuclear, rocket, space and chemical industries, in
industries with a continuous production cycle
31.
Objects of critical informationinfrastructure
A cyber attack that disrupts the normal functioning
of objects of critical information infrastructure
(without their physical destruction) should be
considered an attack within the meaning of IHL.
However, it must be assumed that appropriate State
practice is also necessary.
The doctrine notes that such practice is necessary for
the reason that it will be “a litmus test for the
adequacy of existing humanitarian law rules”
32.
Cyber attack. Conclusion.A cyber attack will be considered an attack within the meaning of
international humanitarian law in cases where it leads to the death of people,
injury to them, physical destruction or damage to objects, as well as in cases
where the normal functioning of critical information infrastructure objects is
disrupted without their physical destruction or damage.
However, the important role in the qualification of a cyber attack as an
attack within the meaning of IHL is played by the practice of States, which
needs to be actively developed
33.
Final conclusions1. All cyber operations that are equated to military operations fall under the
restrictions imposed by the norms of IHL.
2. A cyber attack will be qualified as an attack within the meaning of IHL in
cases where it leads to the death of people, injury to them, physical destruction
or damage to objects, as well as in situations where the normal functioning of
critical information infrastructure objects is disrupted without their physical
destruction or damage.
34.
State Practice. Conclusions• State practice plays the important role in
the issues of ratione materiae of IHL in
cyberspace.
• Moreover, State practice also plays the
important role in the development of
relevant rules of international law in
relation to cyberspace as a whole.
35.
Proposals• To develop an international treaty? – No!
The development of such an international
treaty may take not even years, but
decades!
• Not all States support the initiative to
develop and adopt such an international
treaty (the example of the Russian
concept of Convention on International
Information Security)
36.
The most acceptable solution• The development of relevant State practice.
The purpose of such practice creation is not
to develop new rules of international
humanitarian law, but to adapt existing rules
to cyberspace
• The international community must use other
ways to develop the relevant State practice: it
is necessary to submit this issue to the
agenda of plenary bodies of international
organizations, for example, to the UN
General Assembly




































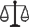 law
law








